FaceApp is another selfie service that allows you to share aging and other filtered photos with your friends. It has been downloaded by millions of users since its introduction in January 2017 and seems harmless enough. But like with any new social media application, I was suspicious and rightfully so.
What’s my traffic normally like?
Before I began my investigation, I wanted to get a baseline of what my traffic normally looked like. Using our network traffic analyzer, Scrutinizer, I pulled a report from our FlowPro Defender exporter to look at host-to-host connections and destination FQDNs. I made sure to look across all exporters and interfaces in my network, because I wasn’t sure what path my phone may take. I then went to my phone and grabbed my IP address, also adding this as the IP host filter in Scrutinizer.
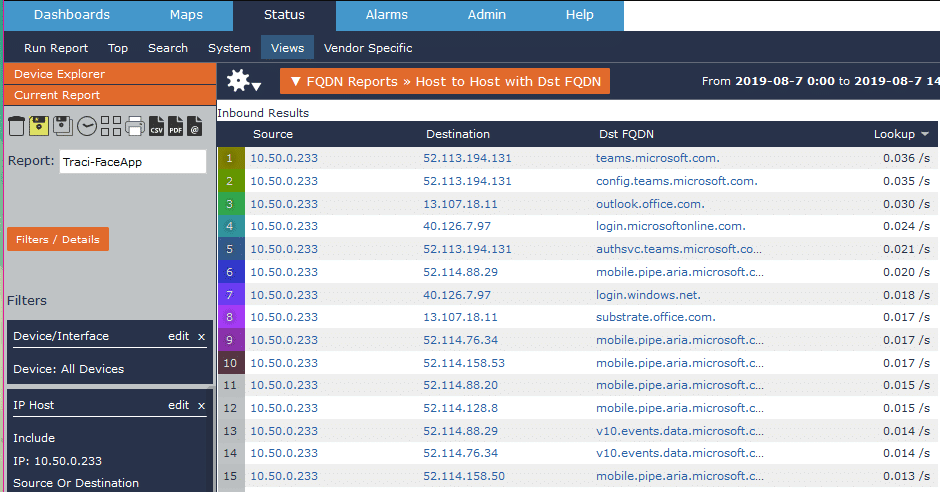
I looked through a day’s worth of traffic and saw that it was all mostly the same Microsoft traffic. Once I had a baseline for my traffic, I decided to play it safe by backing up and removing my photos and other programs from my phone. Then I installed FaceApp.
What’s my traffic like while using FaceApp?
I installed FaceApp, allowed it to access my photos, and agreed to cloud photo processing. I then took my first FaceApp photo and applied the ‘Cool Old’ filter.
I expected to see some traffic to one of their cloud servers while the application processed one of my filtered photos.
This is what I saw instead:
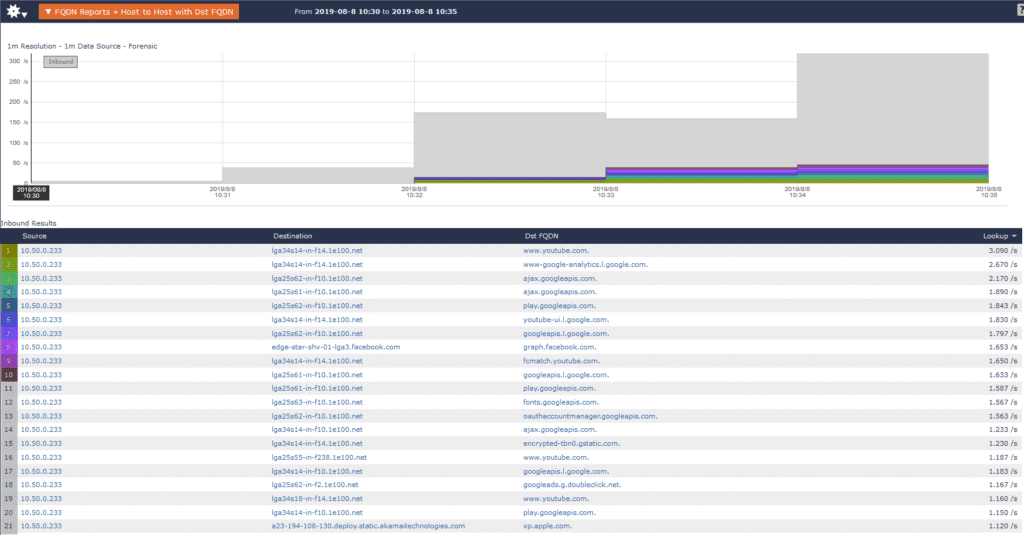
This is a good time to note that I do not have YouTube or Facebook installed on my phone. Nor did I have any other programs running. So why would my phone be reaching out to these sites?
One theory is that FaceApp was generating ad revenue from sites like Facebook and YouTube by pretending to be me to boost their own views. That’s just a theory, but what reason would FaceApp have to reach out to YouTube as often as it does?
During the five-minute period that FaceApp was in use, 300 small conversations occurred. Of those individual conversations, only one involved a cloud server. The rest involved YouTube, Facebook, and ad services.
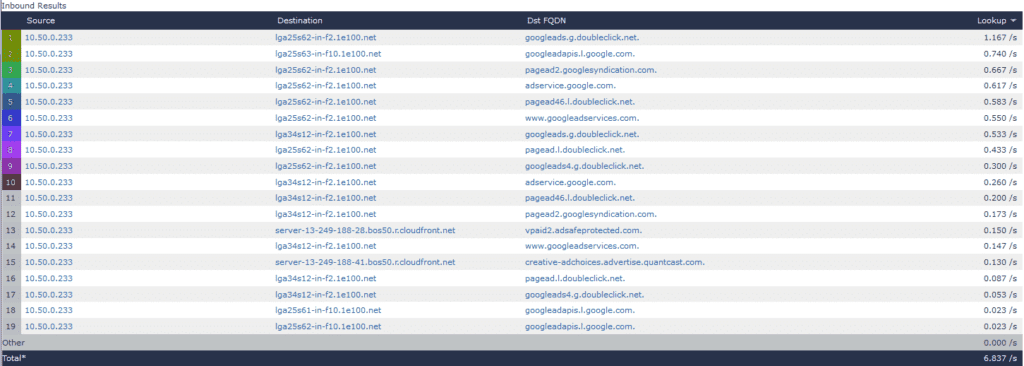
Below, I filtered on only those ad services:
What’s FaceApp up to when the app isn’t in use?
Whether the app was in use or not, I saw the same traffic patterns.
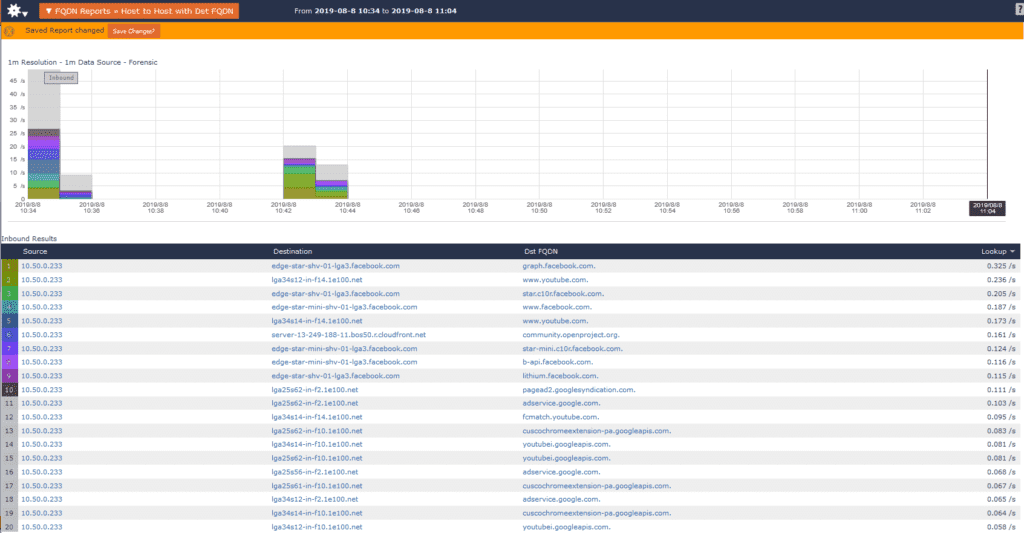
Seeing traffic like this is representative of an application that is either stealing your data for the purpose of building targeted advertisements or using your data to boost their own ad revenue. FaceApp isn’t the only application that has been doing things like this either; companies you trust are stealing from you all the time. Check out your own network traffic using Scrutinizer.


