 One of the most daunting tasks network administrators face on a day to day basis is ensuring that authorized users can access the network resources they need while unauthorized individuals are kept at bay. Before allowing anyone to perform certain actions, you must ensure you know who they actually are (Authentication) and if they are authorized to perform this action (Authorization).
One of the most daunting tasks network administrators face on a day to day basis is ensuring that authorized users can access the network resources they need while unauthorized individuals are kept at bay. Before allowing anyone to perform certain actions, you must ensure you know who they actually are (Authentication) and if they are authorized to perform this action (Authorization).
Also, accurate records must be maintained showing that the action has occurred (Accounting). TACACS+ and RADIUS are the two main AAA protocols commonly used in enterprise networks today. In this blog, I’ll be covering one of Scrutinizer’s newest features – TACACS+ authentication support for secure logins.
What is TACACS+?
Terminal Access Controller Access-Control System Plus (TACACS+) is one of the major AAA protocols commonly used in enterprise networks today. Developed by Cisco, it was released as an open standard in 1993. TACACS is defined in RFC 1492 and uses port TCP 49 by default. While this AAA protocol is mainly used for device administration, it can also be used for some types of network access.
The TACACS+ protocol provides detailed accounting information and flexible administrative control over the authentication, authorization, and accounting process. It enables a TACACS+ client to request specific access control and the TACACS + process to respond to each component into.
The protocol provides security by encrypting all traffic between the Network Access Server (NAS) and the process with a secret key being known to both the client and the TACACS+ process. TACACS+ authentication uses three packet types. The user always sends Start packets and Continue packets, while the TACACS+ process responds with Reply packets. The latter will either grant or deny access, report an error, or challenge the user. Once the authentication is complete, the connection gets closed. Typically, only three login retries are allowed.
TACACS+ vs RADIUS
Since TCP is a connection-oriented protocol, TACACS+ does not have to implement transmission control. RADIUS, however, does have to detect and correct transmission errors such as packet loss, timeout, etc. since it relies on UDP.
RADIUS encrypts only the users’ password as it travels from the RADIUS client to RADIUS server. All other information: the username, authorization, accounting get transmitted in clear text. TACACS+ encrypts all the information mentioned above and does not have the vulnerabilities present in the RADIUS protocol.
Another advantage of using TACACS+ lies in its ability to separate authentication, authorization, and accounting. TACACS+ communication between the client and server uses different message types depending on the function. With that said, different messages may be used for authentication than are used for authorization and accounting. This is why TACACS+ is so commonly used for device administration.
For more information on RADIUS AAA protocol, please visit Joanna’s blog RADIUS Authentication in Scrutinizer.
How to set up TACACS+ Authentication in Scrutinizer
Now it’s time for the most exciting part of the blog – configuring TACACS+ authentication to securely log in to Scrutinizer.
Let’s start with opening up Scrutinizer in the web browser, selecting the Admin tab, then Security and TACACS+ Configuration (BETA). Once in the new window, all you have to do is input the information regarding your TACACS+ Authentication server, and you’re all set!
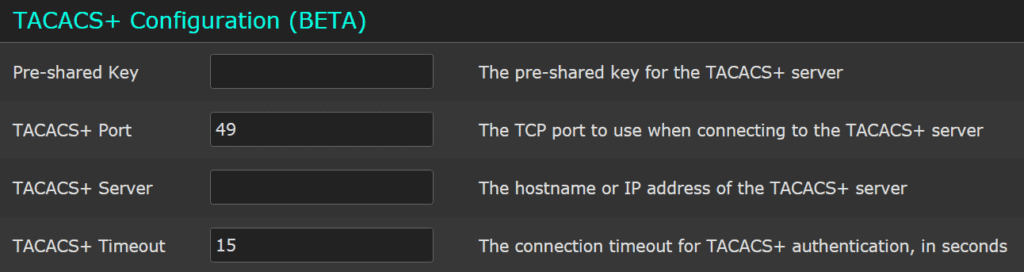
Now log out of Scrutinizer and log in using your TACACS+ credentials. A piece of cake, wasn’t it?
What’s Next?
If you are already using TACACS+ for accessing applications in your network, you can now use that to securely log in to Scrutinizer. Please feel free to download the latest version of our NetFlow analyzer and give it a test drive.


