It’s hard to believe, isn’t it? Our security vendors (e.g. McAfee, SonicWALL and others) are using the same tactics as malware to extract information from the computers on our networks and they are sending it in a way that evades some of the best firewalls on the market.
How are they doing it?
It is done with something we call “data exfiltration tunneling” and it uses disposable DNS names. McAfee and SonicWALL are two vendors we see doing it here at Plixer – a lot. These exfiltration tunnels are used as a type of “phone home data collection” methodology.
How it works
Client computers that have the McAfee anti-virus program installed will make DNS requests for a domain that resembles a-0.19-b3000081.a010083.15e0.1d99.36d4.210.0.ic7arfsqqzf694fs8zf8nz2t9b.avts.mcafee.com. If that looks obnoxious, read on as it gets more interesting. When the local DNS for the client determines that it can’t resolve this crazy long domain to an IP address, it will forward the domain request to an authoritative DNS in an effort to resolve the domain to an IP address. Eventually, a DNS server at McAfee.com will receive the domain request and it may or may not reply to the clients, it will likely keep the contents hidden in the crazy long DNS name. This is where you ask “What do they want with it?” The answer is “I’ll have to speculate.” My guess is that they are doing real-time data collection to create / distribute new threat signatures (i.e. their intentions are good).
What is a DNS NXDomain Response?
In many cases, when the client tries to resolve one of these crazy long domain names, a NXDomain response will eventually be sent by the local DNS back to the client. NXDOMAIN is a DNS message type received by the DNS Resolver (i.e. client) when a request to resolve a domain is sent to the Recursive DNS which it cannot resolve to an IP address. An NXDOMAIN error message means that the domain does not exist.
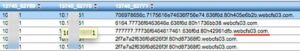
Below is an example of a crazy long DNS request headed to SonicWALLs domain (webcfs03.com). Presumably, encoded messages are encrypted into those long domain names. Again, this domain is whitelisted traffic but, the problem is that the bad guys are using the same tactic because it is so effective at getting past all firewalls. Below is a NXDOMAIN response triggered by webcfs03.com (sonicwall) which was captured by our FlowPro Defender. It monitors DNS NX Domain Responses and it also monitors DNS TXT messages.
McAfee’s Friendly BotNets
If you don’t like how McAfee is phoning home with details about your company from all of the computers on your network that have the McAfee software installed – too bad! My guess is that you may have agreed to it as part of their End User License Agreement (EULA) when you installed the software. This phone home strategy used by companies like McAfee, Sophos, Apple and SonicWALL allows them to setup a form of “legal botnet” which is used to create an army of drones at all of their customer networks. McAfee, SonicWALL and the others in a sense are the Command and Control (C&C) center. Again, this type of DNS request is exercised by McAfee in the best interest of everyone involved (i.e. to fight malware) but, the bad actors are using this data exfiltration tunneling technique as well. If you are asking ‘why’ again, the reason is because in many cases the local firewall won’t question this type of DNS request and will pass the information on toward Internet with little scrutiny.
What can we do to stop this type of DNS traffic which leverages data exfiltration tunneling techniques? Mostly, we don’t want to stop it but, we should monitor it and allow it by exception. That is, create a “white list” of destinations that you will allow, but trigger a watch on any others that are observed.
Monitor DNS NXDomain
Some forms of bot software leverage domain generating algorithms (DGA) to try and reach the C&C. In some cases hundreds or thousands of requests generated by the DGA are sent to the local DNS by the malware every day. Each new domain requested by the infected client will likely trigger a NXDomain response by the DNS. By monitoring DNS NXDomain requests and keeping scores per client, we can raise awareness of suspicious activities but, we shouldn’t alarm without further homework. The reason why is that we want to reduce the risk of false positives. First, we have to whitelist domains like mcafee.com and webcfs03.com (sonicwall) because we know that NXDomain responses for these domains are considered friendly communications. Then, we have to look for activities from suspicious clients such as:
- Reaching out to a domain that is on the black list for having a poor reputation
- Reaching out to sites often used by malware that provide the same service as http://whatismyipaddress.com/ to determine the Internet facing IP address which the malware sends onto the C&C. This allows the bad actors behind the C&C to determine if the infected company that resolves to the IP address is worth trying to penetrate deeper with a more targeted attack.
If you would like to try a solution that identifies infected machines using the strategies discussed in this post, check out the FlowPro Defender .
Give our guys a call for a demonstration on how it can help you reinforce you defenses against bots that are trying to exfiltrate your corporate assets using stealthy DNS tactics.