We all know that VPN monitoring is something every network and security engineer should be familiar with, but with the recent uptick of changes in companies work-from-home policies, IT departments are struggling to scale up to the VPN demands. Let’s be 100% honest about this: most networks weren’t designed to handle the demand we are seeing right now.
We need to make sure our business-critical applications are working properly. Our NetOps and SecOps teams have to take a much more granular approach when looking at this information since a lot of data breaches have been traced back to improper VPN access controls. This blog will cover how to keep a close eye on this type of traffic and get alerted proactively when odd behaviors are observed.
VPN IPFIX exports
The good news is that many VPN vendors have implemented NetFlow, IPFIX, or other forms of metadata exports we can integrate with. Some of the major vendors/solutions doing this are listed below (this is by no means a complete list; please reach out to the Plixer team with questions!).
- Palo Alto
- Cisco ASA
- SonicWALL
- Juniper
- CounterACT
- Microsoft Active Directory
By collecting from these vendors, we can get insight into which users have logged in, what resources they have touched, and what applications they have used. This level of visibility and accountability needed when you make configuration changes or other network-related actions. Take the image below, which shows my VPN traffic from when I was working remotely (obfuscated critical resources). I can easily see when I logged into the network and exactly what resources I touched.
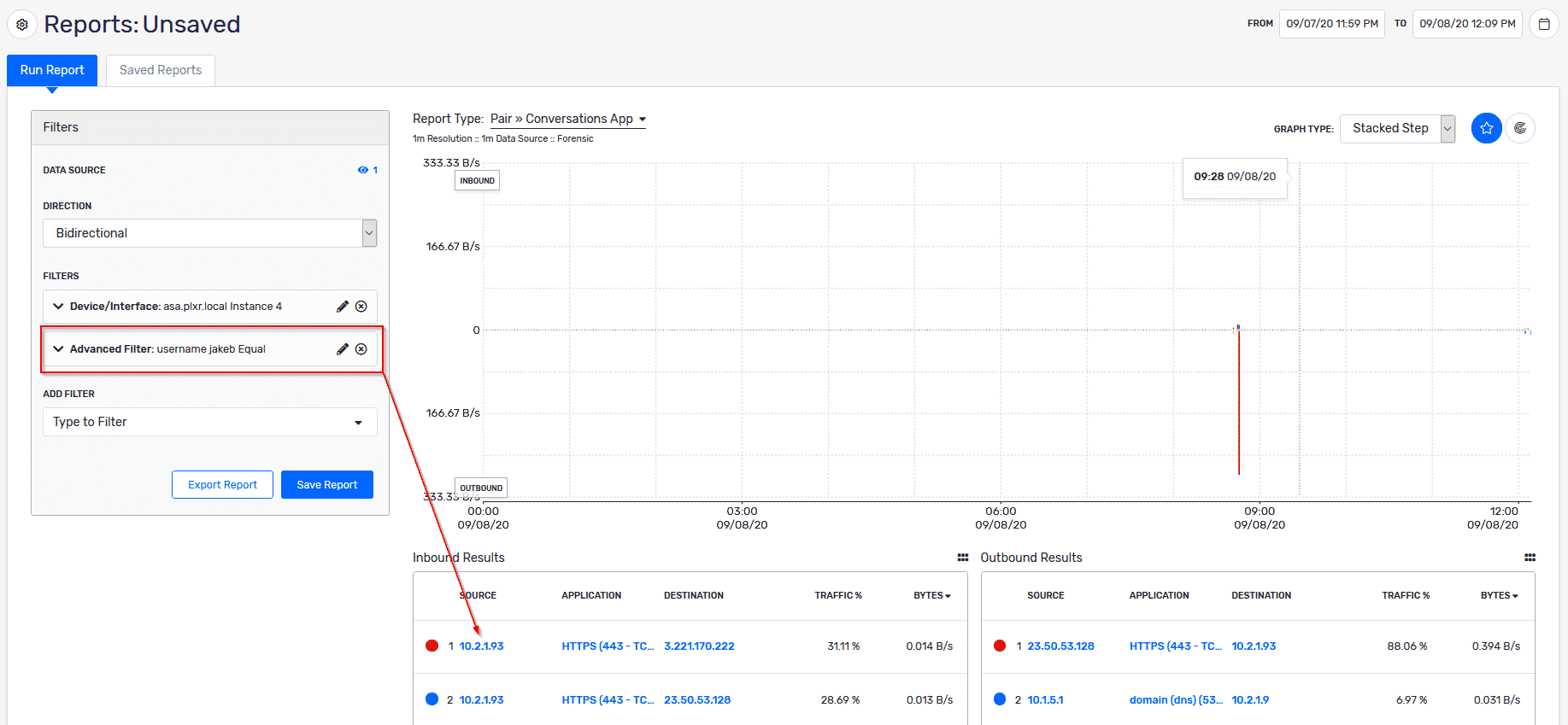
Notice the filter on the far left for my username. The best part about this reporting is that we never need to remember IP addresses; we just need the username that is used for access.
Proactive VPN monitoring
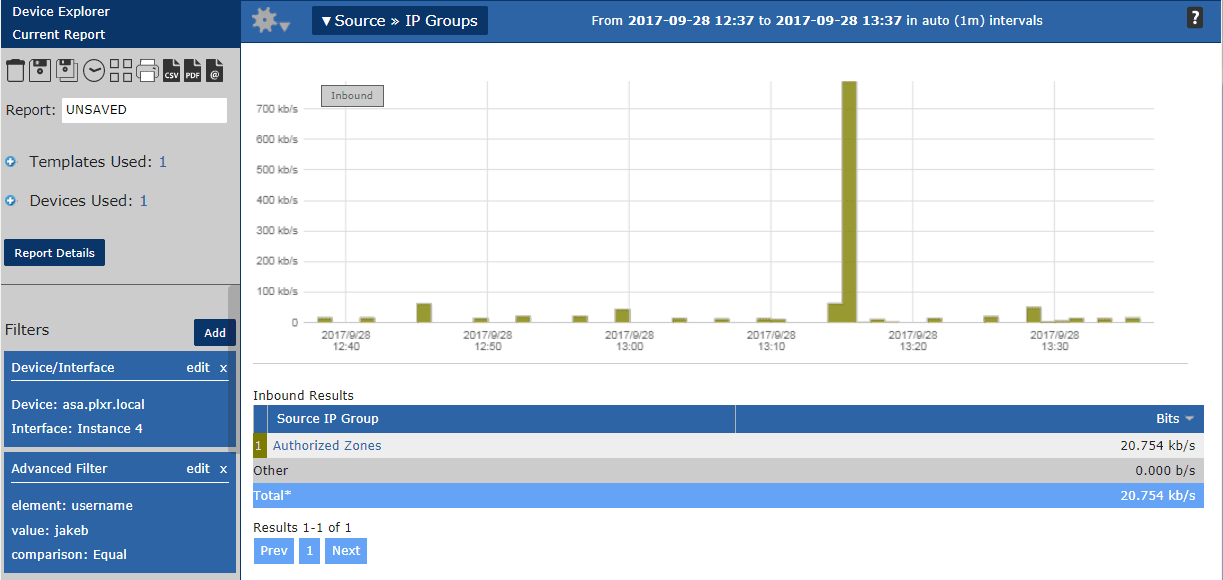
Now that we have our VPN device configured for NetFlow/IPFIX, it’s time to create some thresholds and reports to make sure that our vendors are only accessing what they need. We can easily define authorized/unauthorized zones with IP groups. See the example below that I have set up for the particular server IPs that the vendor should be accessing. Once I take a look at the report with the particular vendor, I’ll be able to see any other groups they are accessing (this is made even easier through our various IPAM integrations).
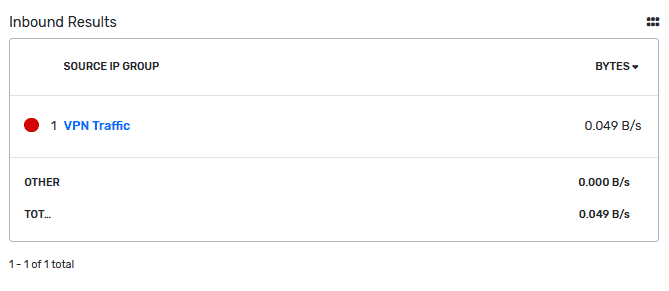
You can now see from the image below that the user in question (jakeb) has only accessed the Authorized Zones group we created!
Future of VPN monitoring
Since networks are getting larger and VPN access is becoming more and more prevalent the need to monitor this traffic is becoming a necessity, even in smaller networks. Take the quote below, which is from 2013:
“For example, 63 percent of the 450 data breaches studied in the 2013 Trustwave Global Security Report were “linked to a third-party component of IT system administrators,” meaning a third-party introduced security deficiencies easily exploited by hackers.” – Wired
Even though the quote is 4 years old, I think it is still extremely relevant given the latest data breaches. It shows that even back then, network and security engineers had to stay vigilant on who accessed their network. Using NetFlow/IPFIX and other forms of metadata will help shed light on suspicious traffic and problem users. At a time when IT is scrambling to deal with all the challenges of a quickly growing remote workforce, a tool like Scrutinizer provides the ability to visualize, monitor, and secure their network traffic.
If you have questions or need help policing this traffic, feel free to reach out to our team here!




