When it comes to network security there are dozens of factors that we always need to consider. Can we block malicious traffic? Are we able to prevent data from leaving our network? What about threats that come from inside the network? The list goes on and on. One additional thing to think about is secure authentication. If a user’s credentials become compromised that can pose a serious issue. Suddenly, someone on the outside now has the ability to log in and start sending data out. Furthermore, this bad actor now has access to business critical applications. The question then becomes, what can we do to make sure users are logging in to critical applications safely? In this blog, I will highlight how Scrutinizer now offers RADIUS authentication support for secure log ins.
While we can’t help your users log in safely to every application on your network we can certainly start with Scrutinizer! In our latest release, 16.7, we began offering RADIUS Authentication as well as TACACS+. To keep this short and sweet, I will just be focusing on Radius.
What is RADIUS Authentication?
RADIUS stands for, “Remote Authentication Dial-In User Service”. The Radius protocol was developed by Livingston Enterprises, Inc. as an access server authentication and accounting protocol. So what does that all mean and how does it work?
The Details
Normally when you log in to an application, you enter a set of credentials that are stored in the application. You type in your username and password, the application checks the database for the credentials, then logs you in. Pretty simple stuff. With RADIUS, things become a little more complicated but in a good way! RADIUS is a client/server protocol. The RADIUS client is typically a NAS (network attached storage) and the Radius server is usually a daemon process running on a UNIX or Windows NT machine. When a user goes to log in, the RADIUS servers receive a user connection request, authenticate the user, and then return the configuration information necessary for the client to deliver service to the user. Also, a RADIUS server can act as a proxy client to other RADIUS servers or other kinds of authentication servers. There’s a lot more fancy stuff behind it which you can read about here on Cisco’s website .
Where Scrutinizer Comes In
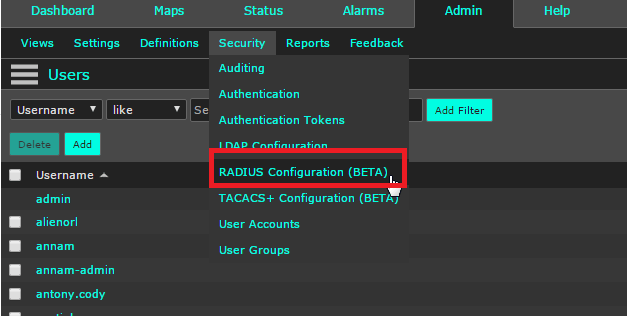
As I stated earlier, you can now log in to Scrutinizer using RADIUS! To do this, open up Scrutinizer in your web browser, select the admin tab, and then security. Under the security option you’ll be given a variety of different ways to allow users to log in. For this blog, select the RADIUS configuration.
Once in the new window, all you need to do is input the information regarding your RADIUS Authentication server and you’re all set! Log out of Scrutinizer and log in using your RADIUS credentials to enjoy a secure log in experience.
Of course if you want to give the latest version a try feel free to download and give it a test drive. If you need assistance with your install my colleagues and I would be happy to help so don’t hesitate to reach out!
Peace, love, and Netflow.