A few years ago, I wrote a blog that talked about how our Palo Alto NetFlow reporting allows network administrators to easily identify traffic trends occurring on the network. The application and username correlation reporting has proved to be extremely value to our customers using Palo Alto Networks as their firewall platforms.
Since then, we have added another reporting and analaysis dimension in regard to the Palo Alto NetFlow. We now use the username visibility to provide global username correlation to any IP address seen on any network device, anywhere on the network.
The benefit of username correlation
Username correlation and awarness is a powerful feature because tying the username to the flows created by a host makes tracking down a culprit much faster. Remember, IP addresses can change. The ability to see any user who had a login event on any IP address, in any timeframe, provides greater situational awareness when investigating network security incidents.
As the frequency and cost of insider threats continue to grow, the ability to track lateral movement from insider threats using username correlation becomes a necessary tool in the security administrator’s arsenal.
In a recent Brilliance Security Magazine article, Justin Jett, Director of Audit and Compliance for Plixer, stated that:
“As the cost of insider threats continues to grow, it is important for IT professionals to have the data context they need to know where an attack is taking place. As the report indicated, 64% of incidents resulted from negligent employees. Credential misuse is a primary method for hackers to gain a foothold on a network. By using phishing attacks to steal employees’ credentials, malicious actors can begin looking for ways to steal data on the network. By using network traffic analytics, IT professionals can easily see where employees’ credentials are being used and stop hackers from gaining the foothold when they see credentials being used in atypical locations.”
Check and alarm on username credential misuse
Using our Network and Security Intelligence Platform, we can actively monitor for username credential misuse by checking the number of logins that a particular user has to any host IP addresses on the network.
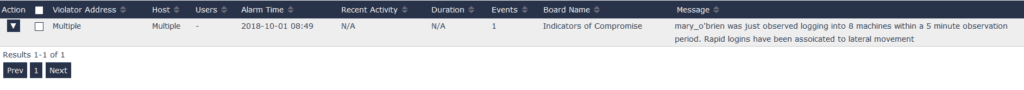
From this alert, you can detect possible lateral movement, then pivot directly to the timeframe and the flow data that represents that traffic. From there, you can add filters and change the timeframe to learn where this user/IP host has made connections, and what type of protocols were involved in those connections.
NetFlow and IPFIX are great for knowing the whos, whats, and whens that make up your network traffic. By collecting flows representing all of the conversations traversing the network, you gain visibility into suspicious conversations coming in and out of your network, as well as those moving laterally inside. Now with the added contextual awareness of correlation between the usernames and the host IP addresses, security administrators can recognize and analyze the odd behaviors to identify an infection.
If you have Palo Alto firewalls, configure NetFlow and download Scrutinizer, and become user-aware.


