Today, I want to discuss how you can use NetFlow for detecting malicious traffic on your network. With all of the recent malware outbreaks the network security tools and solutions put in place are becoming more and more critical. Alongside client Anti-Virus, corporate firewalls, and content filtering, malware can sometimes slip through all of that and still make it onto the network. When it does, how do you tell where it’s at? Who is it talking to? And perhaps more importantly, what kind of information is it sending off your network? Using NetFlow we have an index of every conversation and transaction that has taken place on your network. We can use this data to pinpoint the user who is infected and lower the response time to eradicate the malware.
Network Security Algorithms:
We know that NetFlow data can give us almost any information element that is being observed by the exporter. This is great, but we need a way to proactively monitor this traffic. We don’t want to sit in front of our NetFlow collector or incident response system waiting for malicious traffic. Using highly customizable network security algorithms we can let the NetFlow collector do the work for us (that is why you bought it, right?). The image to the right shows just some of the algorithms and host reputation lists that you can monitor using our incident response system.
collector or incident response system waiting for malicious traffic. Using highly customizable network security algorithms we can let the NetFlow collector do the work for us (that is why you bought it, right?). The image to the right shows just some of the algorithms and host reputation lists that you can monitor using our incident response system.
Monitoring Data Exfiltration:
Now that we know we can be alerted when malicious traffic is on our network, how can we tell what it’s doing? For the next step we need a NetFlow collector that has a robust reporting engine. This way we can track the malicious traffic for a long period of time. Why is this important? Since we know the user became infected and is communicating to known malicious hosts we probably want to 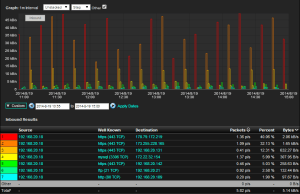 find out how it made it onto our network. Maybe the user clicked a bad URL when checking their email (IE Spear Fishing), perhaps it was a drive-by download on a compromised website. Either way, all of this information can be contained in NetFlow/IPFIX. The image to the left shows a host that was communicating out to known botnet servers. Notice the systematic heartbeat that is going out, usually this means they are trying to pull down new instruction sets from the C&C server. You can also see that it is reaching out to other hosts on the network looking for open ports that they can exploit. Now that we know the infected host and who they were communicating with, we can sandbox the PCs in question and monitor them to see what exactly they were trying to do.
find out how it made it onto our network. Maybe the user clicked a bad URL when checking their email (IE Spear Fishing), perhaps it was a drive-by download on a compromised website. Either way, all of this information can be contained in NetFlow/IPFIX. The image to the left shows a host that was communicating out to known botnet servers. Notice the systematic heartbeat that is going out, usually this means they are trying to pull down new instruction sets from the C&C server. You can also see that it is reaching out to other hosts on the network looking for open ports that they can exploit. Now that we know the infected host and who they were communicating with, we can sandbox the PCs in question and monitor them to see what exactly they were trying to do.
Future of Network Security:
Unfortunately I can’t say for certain what the future has in store for new threats, but I can say that they will be there and they will be more advanced than anything we are currently seeing. The best defense against them is a layered security approach.With the use of NetFlow you will be able to track any bad behaviors on your network. Stay tuned as next week we will be posting a more in-depth analysis of the advanced persistent threat that was monitored using our incident response system.


