In the past, network admins used packet capture technology to dig down into what was happening on their network. For troubleshooting general networking issues, this was good. But networks grew, issues became global, and security became a main player in an admin’s day. Sadly, this growth presented some problems with using packet capture technology.
With a packet capture, you are grabbing the whole enchilada, payload and all. Sometimes this is needed, but much of the time it’s not. Basically, shifting through all that data for evidence of an intrusion is like finding a needle in a haystack. Data of this size also presents an issue with filtering/reporting and in reality, a full packet capture might not be worth the investment.
Holy payload, Batman!
Every superhero has a sidekick, right? Well, NetFlow is the Robin to the packet capture Batman. I know, silly analogy, but stay with me for a minute—it gets better. As I mentioned before, one of the biggest issues with using a packet capture is the sheer load of the data. With this load comes added cost. Not just added storage costs, but the cost involved with making sure that you have the right hardware and software to manage and report on the data.
Also, packet capture probes have to be deployed in targeted locations to gain the needed visibility. This process can also be cumbersome and costly. The maintenance demands of probes alone limit the deployments on a large scale. So in practice, it is usually impossible to gain enterprise-wide visibility using packet analyzers by themselves. We need packet capture, but it needs something to complement it. Our Batman needs a Robin.
At this point you might be thinking that I am anti-packet capture. You’re saying things like, “Jimmy D, he’s all NetFlow,” and “He’s the NetFlow Detective, so no pcap for him.” That is far from the truth. In reality, packet capture technology is still the go-to tool in some situations. Specifically, NetFlow lacks the ability to provide the actual data transferred in the suspect conversation. It’s this payload visibility that is vital in on-the-fly forensics investigations.
In the event of a data breach, for example, you need to be able to quickly understand what happened, how it happened, and what systems or data sources were compromised. Packet capture provides a complete and accurate historical record of network traffic, so you can reconstruct events and drill down to the actual network packets to pinpoint exactly what took place.
So riddle me this Batman, how does NetFlow help?
As the Robin to the packet capture Batman, NetFlow provides you with the “who,” “what,” and “when” of network transactions, but because of its light metadata, it lacks the weight of a packet capture.
NetFlow is UDP technology that gives metadata visibility on things like the senders/receivers IP address, the ports they communicated on, the time it happened, the date that conversation occurred, the length of the conversation, and the amount of data that was transferred. I am oversimplifying the metadata that can be reported on, but you get the idea. NetFlow provides lots of detail without the overhead. Matter of fact, with some of the latest versions of NetFlow, like Flexible NetFlow, you are able to see much more than basic IP accounting.
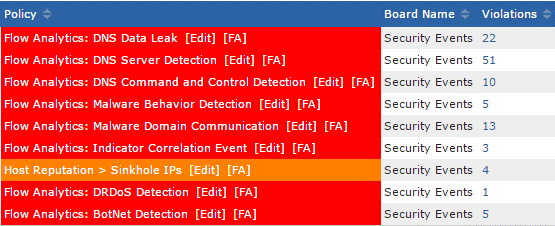
This metadata creates a lightweight view of all of your network’s traffic. It’s the sidekick we were looking for. It’s our Robin! Network forensics and security monitoring tools, like Scrutinizer, can also use this data to monitor and alert for traffic abnormalities along with other IOCs. Since the flow is so light, you can store it for as long as you want, making digging into your conversations easier. Let’s not forget that NetFlow, or any of the other variants, is built into your device. Your routers, firewalls, and other supported devices now become your probes.
So how do they work together?
NetFlow monitors your entire network’s traffic and it does it with limited overhead. Flow collection delivers the most important details offered by SNMP while providing over 90% of the visibility most IT professionals used to turn to packet analysis for. Because of this, security teams can leverage flows to monitor for abnormal behavior and trigger for suspicious events that are a sign of unwanted infiltrations. Sometimes you need more granular insight to the “what” in a conversation. This is where packet capture shines, because it retains the packet payload in its entirety.
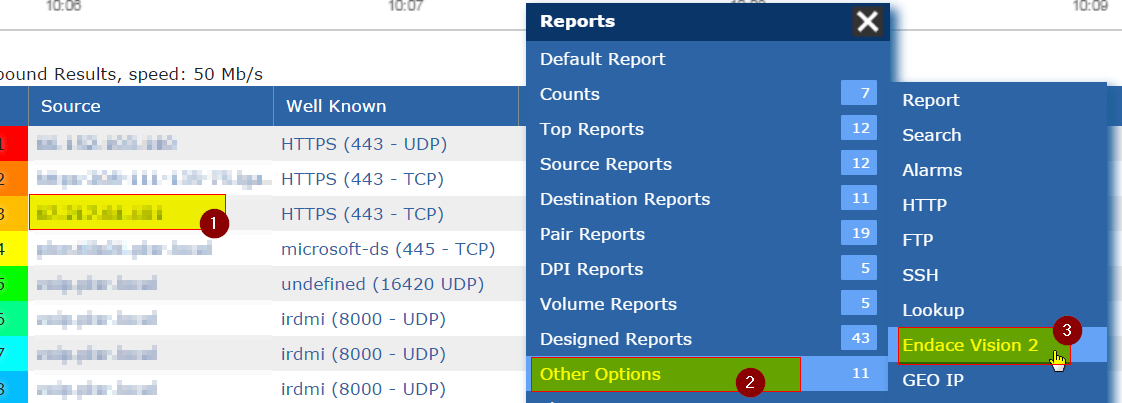
Integrating packet capture technology, like the Endace Packet Capture Solution, into your NetFlow tool allows you to combine the benefits of NetFlow monitoring with the deep-dive appeal of a packet capture. It lessens the load that a packet capture requires while still providing the raw data when you need it.
In the end, that’s what it’s all about—lessening time to resolution when an incident occurs on your network. Combing the two technologies can lessen investigation time from hours or days to just minutes. To make a long story short, it’s like having your own dynamic duo in your toolbox. If you would like to see how Scrutinizer can be used to monitor for abnormal behavior on your network or how to leverage packet capture tools with NetFlow, download a free trial of Scrutinizer.