The continuous increase of gigabit speeds in computer networks has considerably stimulated the usage of flow monitoring techniques for network management. For this reason, researchers and operators are searching out more flexible and scalable solutions. This blog will briefly discuss NetFlow adoption and why it has surpassed other technologies like SNMP and packet capture.
Flow data like SNMP is widely adopted and has been implemented on nearly every router manufactured by most vendors. This is because it has several advantages over traditional traffic analysis protocols. Flows are a push technology whereby, unlike SNMP no polling is needed. For this reason, it also doesn’t require a password or community string.
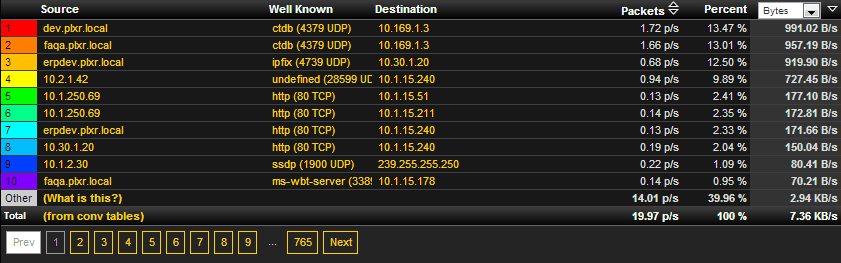
Accessibility is another driver of flow growth. It’s readily accessible in almost all the corners of every network. It simply needs to be turned on. Nearly all firewalls support it as do many server operating systems (e.g. VMware, Linux). Several vendors are now marketing true flow capable switches in lieu of packet sampling technologies such as sFlow.
Flow technologies, as sighted by the Gartner Group, should be done 80% of the time and that packet capture with probes should be done 20% of the time.
Another major reason for this widespread NetFlow adoption is because of regulator compliances. Concerns over regulatory compliance such as HIPAA, FIPS, NERC, SCADA, PCI, NPPI, SOX and COSO have executives prepared to make investments to ensure that in the event of an audit, they can provide the deepest levels of visibility, accountability and measurability required for ensuring and maintaining compliance with these industry standards. Flow technology allows administrators to quickly confirm the source of the problem by narrowing down the issue to the client, server or network, thereby preparing for an audit weeks, months, or even years before an audit takes place. When an audit happens, the company will be ready with the information needed.
NetFlow and IPFIX have become recognized as flexible and readily available protocols for improving several network management related tasks. Flow technology has come of age and is no longer viewed as a simple accounting protocol for billing or for just identifying bandwidth hogs. The introduction of templates has opened up the technology and empowers hardware developers to export nearly any metric / information imaginable.
Due to its widespread adoption and surge in innovative exports, flow technology can be used to help optimize applications at nearly all layers of the OSI model. When it isn’t employed by hardware for monitoring performance, flows can carry details related to syslogs, event logs and nearly any other machine message. Once centrally located, messages can be correlated across different vendor platforms and archived indefinitely for historical research which also services several regulatory compliance obligations.
To learn more about NetFlow adoption and Flow-based approaches in network management download our whitepaper today.