Most companies are taking the position that BYOD (Bring Your Own Device) is allowing businesses to gain more productivity from their work force. Because of this, Mobile Workers are on the rise and it is creating a new IT challenge.  “Certain bring-your-own-device strategies present certain security risks: the introduction of mobile malware onto a hospital network, for example,” said Lynne Dunbrack, IDC Health Insights program director. Some hospitals embracing BYOD, are restricting BYOD devices to Internet access only. Why?
“Certain bring-your-own-device strategies present certain security risks: the introduction of mobile malware onto a hospital network, for example,” said Lynne Dunbrack, IDC Health Insights program director. Some hospitals embracing BYOD, are restricting BYOD devices to Internet access only. Why?
“BYOD has really become an increasing issue for us in the past year,” Bryan Safrit, a senior network architect for Rex Healthcare in North Carolina, said in a statement. “Much more of the traffic we see is from iPhones, iPads and Android devices. Without the ability to differentiate users and enforce policies, our BYOD traffic could overwhelm our bandwidth.” How can employers be sure that the increase in traffic is actually work related? And, how can companies protect themselves from the inherent risks associated with the explosion of BYOD in the work place? We’ll, that is a tough question. First lets understand the problem.
Despite the increase in productivity, some employees like to respond to their turn at Scrabble or to respond to personal skype messages and the like. In the old days, companies could check the phone bill to see if an employee was making or receiving excessive personal phone calls during the day. Today, it isn’t that easy especially when websites like Facebook.com make it easy to play Angry Birds over an SSL connection: https://apps.facebook.com/angrybirds/.
Some of the best ways to track BYOD devices I’ve seen so far are to use NetFlow, sFlow or IPFIX data to:
- Filter on MAC addresses.Specifically, vendor ID can be used.
- Filter on subnets set aside specifically for wireless devices
- Integration with Cisco ISE or Enterasys Mobile IAM
Filtering on MAC or IP Addresses:
We can certainly ask employees to govern their own behaviors when using the wireless network. However, we still need to check on traffic with network traffic reporting tools like a NetFlow Analyzer which can filter on the vendor ID of MAC addresses (e.g. iPhones):
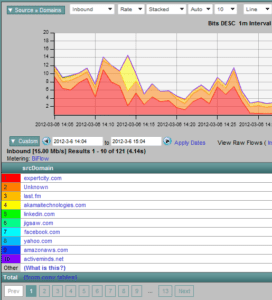
A change in the report above to view the top domains visited by the filtered MAC addresses could result in a BYOD Traffic Reporting solution which includes information like this:
When violators are found, enforce consequences for improper behaviors and word will spread amongst the employees. If administrators want to see how many devices a user has authenticated onto the network, many firewalls (e.g. Cisco ASA, Palo Alto Networks, SonicWALL) support NetFlow or IPFIX and provide the username in their exports. When they don’t, these flow exports can be correlated with the Microsoft Active Directory server, Cisco ISE or Extreme Mobile IAM to gather username details.
Integration with Cisco ISE or Enterasys Mobile IAM
The Extreme Mobile IAM solution can also be used to track BYOD. These systems determine the type of device (e.g. iPhone, Android, laptop, etc.) and consider the username authenticating onto the network and then push policy down to the switches on the network that will be handling the communication for the device. This type of BYOD traffic monitoring allows administrators to track BYOD devices and even group them:
Drill in on a OS above and find who is authenticating these devices and how much traffic they are creating. Reach out to us to learn more!