In the past few months I’ve noticed that the number of support calls we’re taking for help using our NetFlow Analyzer for detecting DDOS attacks seems to be on the rise. We have some existing blogs about these cyber threats, but it’s been a few years since they were written, and the attackers are becoming much more sophisticated and using a number of new methods to conceal and control the attacks.
It used to be the case that discovering suspicious behavior that might be a DDoS attack was simply a matter of looking at overall flow volume for all routers, to see if a spike had occurred. Once that determination had been made, admins could use our NetFlow/IPFIX solution to drill in, find the problem router and take steps to ameliorate or eliminate the threat. These volume based attacks are still being used, but the arsenal of cyber threats is growing.
Evolving Threats
Evolving DDoS attack methods mandate a more sophisticated approach. Application DDoS attacks most commonly target HTTP in an attempt to exhaust web servers through HTTP POSTs or GETs. Attackers are increasingly targeting DNS and VoIP services via DNS Amplification Attacks and SIP INVITE Flood Attacks. Instances of Encrypted SSL DDoS attacks are on the rise, because they are heavy resource users that amplify the impact on the target.
Our NetFlow Analyzer is used by a wide variety of organizations, from Universities and Research Institutes to large industrial concerns and government agencies and ISPs. The network architectures and purposes of these entities vary greatly, but the the approach to dealing with DDoS attacks should be similar for all of them. The methods attackers use may differ, but the goal remains the same, to deny the use of the network asset for its intended purpose.
Our NetFlow analyzer uses Flow Analytics to perform network behavior analysis. There are a number of Flow Analytics algorithms, below is a screenshot of the configuration screen for the DDoS algorithm.
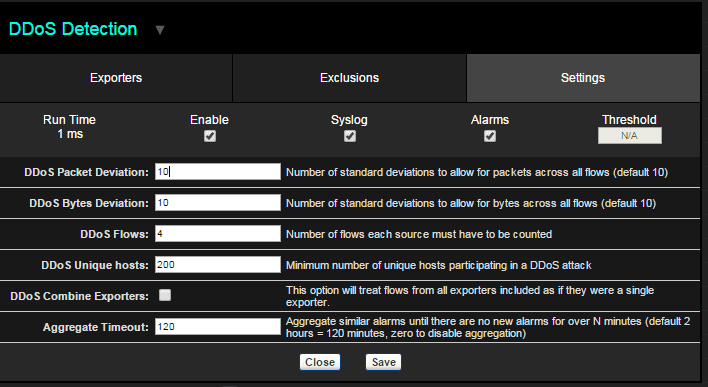
Users are able to configure the DDoS Detection algorithm according to the character and design of the network and the type of cyber threats for which it is a likely target. For example a university system that services a large number of students may want to increase the number of Unique hosts in order to avoid false positives. Other entities may find a DDoS Flow parameter of 4 is too high, and experiment with a value of 3 or even 2, until the right balance is found.
Once configured the DDoS algorithm will produce an alarms report like this:
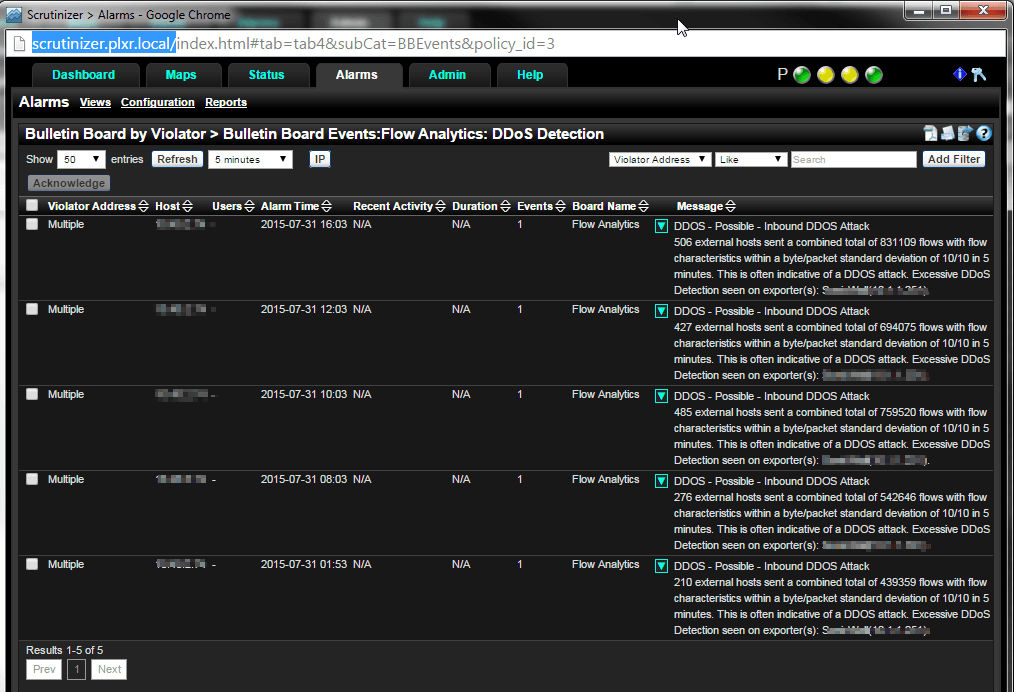
The report details the number of external hosts, number of flows and identifies the device that is experiencing the attack, together with some other detail. Armed with this information you can investigate further to determine if its time to activate your incident response plan.
As I was working on this blog I got an email from United States Computer Emergency Readiness Team that I include here because it’s pertinent and by way of suggesting that you subscribe to these alerts, as part of your cyber incident response plan. The email indicated that the FBI had recently issued an alert about a rise in emailed extortion campaigns, in which businesses receive an email threatening a DDoS attack on the targeted business’ website, unless an ransom is paid, typically in bitcoin. Businesses that came under attack reported NTP, SSDP, SYN Flood and other attacks. The FBI cautions against responding to the attackers, and advises affected businesses to use DDoS mitigation efforts instead.
If you need an Incident Response System that’s capable of identifying Distributed Denial Of Service attacks and other cyber threats, we have the solution for you.




