Last week Ixia announced the integration of their Application and Threat Intelligence Processor and our cyber threat incident response solution. Using IPFIX, or what Ixia calls Ixflow exports, this combined solution gives administrators additional ability to identify and track users, operating systems and applications that generate excessive traffic or security threats.
Today, I wanted to follow up on that announcement and talk about how you configure this flow export which will increase your overall network and application visibility, and network threat forensics and incident response.
I talk to customers all the time who are looking to leverage NetFlow or IPFIX to gain some visibility in to the traffic on their networks. But sometimes they find that the devices they have don’t support any kind of flow monitoring. Or maybe they have devices that support some kind of flow monitoring, but they don’t get the visibility that they really need.
Whether you are looking to flow monitoring for network forensics and incident response, or general traffic visibility, you need insight into all areas of the network.
Ixia’s network packet broker (NPB) is a device that directs network traffic from switch SPAN ports, taps, and/or between two connected routers and/or switches, and then manipulates that traffic by parsing and copying it to allow the more efficient use of network security and performance tools.
Ixia brings a new level of intelligence to the network packet control and analysis. Distinct Application Fingerprints and dynamic identification capability for unknown applications give network managers a complete view of their networks, including application success and failure tracking. By combining rich contextual information such as geo-location of application usage, handset or device type, operating system and browser type, the Application and Threat Intelligence Processor helps to identify suspicious activity such as unauthorized BYOD usage or business connections from untrusted locations.
So why is gathering this type of information important to your network monitoring needs?
- It gives administrators the ability to visualize, understand and optimize their network
- It allows network tools to work better by providing Deep Packet Inspection meta, packet and flow data
- Provides deeper application, device, and user information than available from traditional data sources like routers and switches
- Provides detailed security classification through application signatures, AND dynamic application discovery
- Provides enhanced visibility in to what are normally blind spots when it comes to network traffic monitoring
And all of this rich traffic insight can be exported in flow exports!
Regarding last week’s press release, Greg Copeland, Business Development Manager at Ixia said, “It’s safe to say that almost every network in the world suffers from either application performance problems or malware infections. Companies need to make sure that they have a reliable incident response system when disaster strikes. Ixia’s Application Threat Intelligence Processor’s application intelligence combined with Plixer’s Scrutinizer, provides customers with peace of mind knowing that their network traffic is constantly being scrutinized for unwanted behaviors.”
To configure the flow export you:
- Login to Ixia ATI Processor card settings via web interface.
- Click the Netflow option and enable a Netflow Exporter (choose DHCP or Static IP as appropriate), check Netflow V10, check Enable IxFlow, check Enable Netflow, select the options that you want exported, then click Save
- In the Netflow Settings screen, configure it to send traffic to a collector; click Enabled box, add the IP address and listening port of the collector, then click Save
- That’s it!
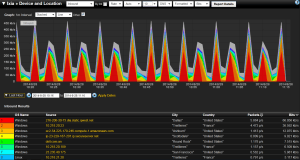
Now let’s take a look at some of the unique reporting that is available.
Notice in the report below we can see the operating system, the host, the city and country, and how much traffic is being generated. You can filter these reports on any field element exported in the flow records, as well as any date/time window that might be of interest.
Efficient traffic management requires usable and relevant information from all points on the network. Collecting IPFIX provides an efficient means to identify inappropriate behavior, problems and discrepancies. The ability to drill down to specifics makes incident response using IPFIX an invaluable tool for charting the health of your network. When security professionals need to go back in time and view a communication pattern, they can find the flows that contain the conversations that they want to investigate.
Do you have blind spots, or visibility points on your network that you wish that you had richer traffic details? If the answer to this questions is yes, let us help you get this type of advanced flow monitoring set up.