2020 was a year of incredible change—changes that I believe will have a lasting impact, but also changes that require immense flexibility with traditional structure and workflows. This is observable in every industry, and ours is no different. Not only has the model of network traffic changed with a work-from-home model, but so has our ability to collaborate as a team. We moved from primarily being in the same physical room as our colleagues to now spending our time in virtual channels. One of the most widely adopted of these digital workspaces is Microsoft Teams.
With Teams being the primary space for collaboration, having a network monitoring solution like Plixer Scrutinizer post alarms to a dedicated Teams channel is an incredibly effective way of monitoring, tracking and assigning network events to team members for investigation. Let’s take a look at how easy it is to configure this integration within Scrutinizer.
Teams makes this fairly easy for us with their ability to leverage API webhooks to post to a particular channel. Let’s walk through the configuration steps.
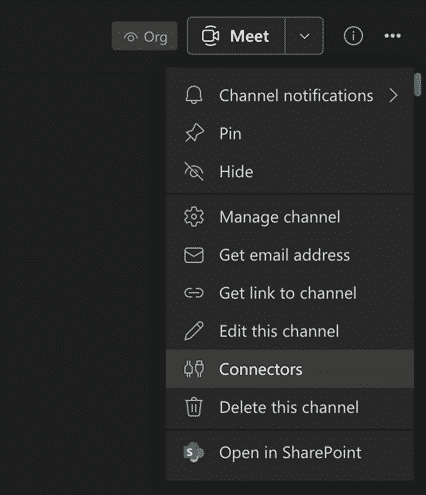
I’d recommend creating a new Teams channel to start. This will give you a clean space for Plixer Scrutinizer to post alarms to, without taking over other conversations. Once we have our chosen Teams channel, we’ll create our webhook connector. From within the channel, click the ellipsis configuration menu and select “Connectors.”
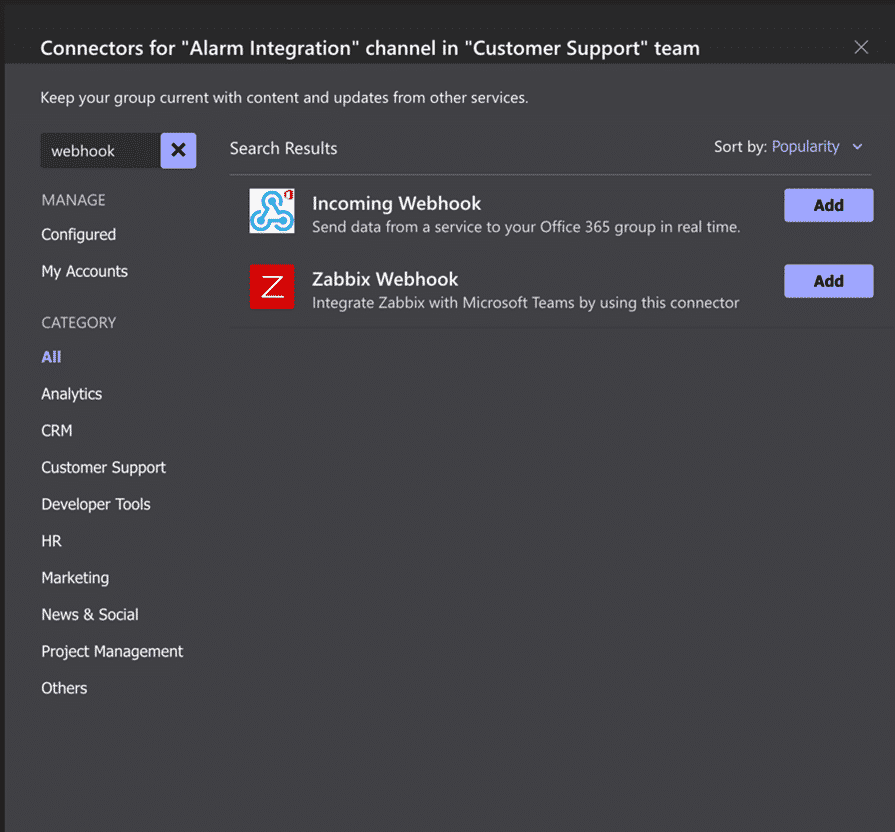
From here, use the search option to search “webhook” and click either Add or Configure for the Incoming Webhoook option.
Within the webhook configuration view, you’ll want to associate a name for your incoming webhook connector. Optionally you can also associate an image for the Teams messages. Click Create and take note of the generated webhook URL provided.
Now we’re ready to configure Plixer Scrutinizer to post alarms to your Teams channel using the webhook we just created. First, we’ll create a custom directory for our script to live in:
mkdir /home/plixer/scrutinizer/files/customScripts
Then assign ownership of that directory to the plixer OS user:
chown plixer:plixer /home/plixer/scrutinizer/files/customScripts
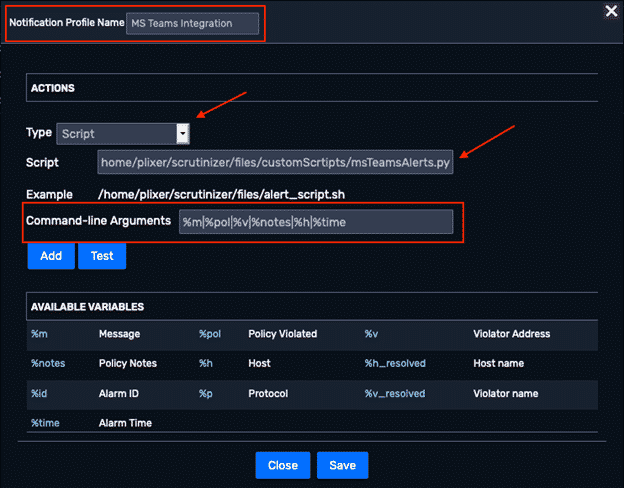
Now that we have a home for our integration script, let’s create the notification profile that will call our integration script. From within the Scrutinizer GUI, navigate to Admin > Definitions > Notification Profiles and click Add.
In the notification profile creation view, we’ll want to:
- Give the notification profile a name (i.e. “MS Teams Integration”)
- Select Script from the Type dropdown
- Supply the full path to our script (i.e. home/plixer/scrutinizer/files/customScripts/msTeamsAlerts.py)
- Under Command-line Arguments, we’ll choose the alarm parameters we want to collect. In my example, I chose the following:
- %m – the full message of the alarm event
- %pol – the name of the policy violated
- %v – the violator address observed in the event
- %notes – any notes associated to the particular policy
- %h – the host observed in the violation (in most cases this would be the destination host)
- %time – the time stamp associated with the violation
With these settings configured, click Save. Now we need to pivot back to CLI and write the actual script. Because Python has a module that makes Teams integration very simple, it will be the language of choice for this project.
!/usr/bin/python3
import sys
import pymsteams
almMsgSplt = sys.argv[1].split('|')
myMsg = f"{almMsgSplt[0]}"
myPolicy = f"{almMsgSplt[1]}"
myViolator = f"{almMsgSplt[2]}"
myNotes = f"{almMsgSplt[3]}"
myHost = f"{almMsgSplt[4]}"
myTime = f"{almMsgSplt[5]}"
teamsConnector = pymsteams.connectorcard("https://CompanyName.webhook.office.com/webhookb2/…………")
teamsConnector.text(f"<b>Scrutinizer Violation</b>")
myMsgSection = pymsteams.cardsection()
myMsgSection.activityTitle(f"Alert for {myPolicy}")
myMsgSection.activityImage("http://127.0.0.1/images/common/xcheck.jpg")
myMsgSection.addFact("Message", f"{myMsg}")
myMsgSection.addFact("Policy", f"{myPolicy}")
myMsgSection.addFact("Violator", f"{myViolator}")
myMsgSection.addFact("Host", f"{myHost}")
myMsgSection.addFact("Time", f"{myTime}")
myMsgSection.addFact("Notes", f"{myNotes}")
teamsConnector.addSection(myMsgSection)
teamsConnector.send()
Let’s break this script down line by line:
- Line #1 sets our interpreter to use python3
- Line #3 imports the sys module, allowing us to accept command line arguments
- Line #4 imports the pymsteams module, which makes the Teams integration nice and simple
- Line #6 is where we associate the command line argument to a variable.
- Note here we’re doing a split on the “|” character used in our notification profile setup
- Lines #9 – 14 set unique variables to each of our alarm parameters based on list indexing
- Line #18 is where we provide the webhook URL created earlier in Teams
- Line #19 is where we set the header text for our Teams message
- Line #22 creates sections for our Teams message
- Lines #24 – 31 set our section parameters for the alarm activity
- These are customizable and optional
- I chose to set an activity title using the policy name
- I included an image readily available on the Scrutinizer appliance
- I define facts for each parameter contained in the alarm (facts here are key:value pairs)
- Line #34 adds the sections previously created into our Teams connector
- Finally, line #36 is where we send our bundled Teams message
With the script created and in place, all we need to do is set the correct permissions and ownership of the script itself:
chown plixer:plixer /home/plixer/scrutinizer/files/customScripts/msTeamsAlerts.py chmod 755 /home/plixer/scrutinizer/files/customScripts/msTeamsAlerts.py
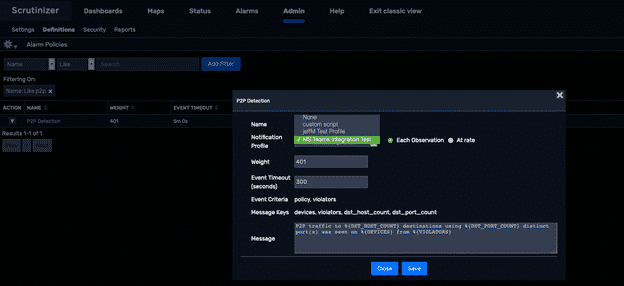
And finally, we’ll now attach our notification profile to any policy we want to receive Teams alerts for. To do this, we’ll navigate to Admin > Definitions > Alarm Policies. Select the policy of interest and use the Notification Profile dropdown to select the previously created profile.
Now we’re done! With this integration in place, the team has a central location to see all alarm violations observed by the Plixer Scrutinizer appliance!
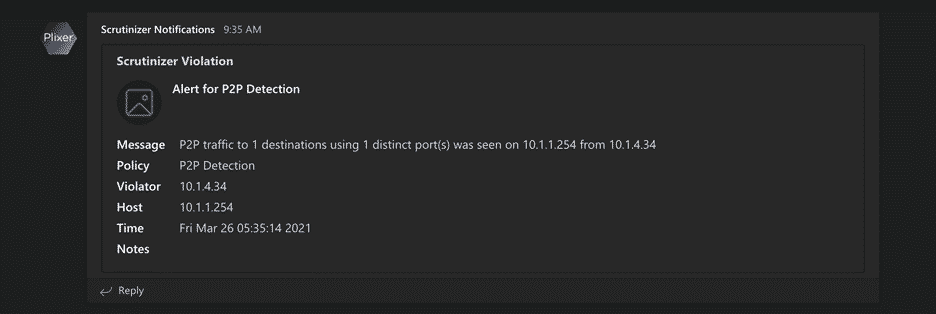
I’m always curious to see how these custom integrations grow. Using this custom integration and the pymsteams Python module, there are many more options we can take advantage of, such as setting a “status” variable, defining potential actions, or even including a webhook back into Scrutinizer from the alarm message in Teams. If you need any help setting this up, definitely don’t hesitate to reach out to us!