Sophisticated attacks continue to grow and breach organizational defenses, and they do so without being detected.
Traditional attacks use straightforward methods, such as weaponizing emails in phishing attacks, which direct the victim to a bad domain where malicious actors can compromise or steal important information. If security teams in the organization can detect and identify such attacks early on, it will help the security team work efficiently and determine whether the attack is a nuisance that can be removed or one that’s debilitating and costly.
Most attacks will involve the network, and security teams should know how to identify the telltale signs in time. Consider the typical data exfiltration attack, which involves the attackers breaching an endpoint and moving laterally throughout the organization from one server to another to find data of value and exfiltrate it.
It is imperative for the organization to identify such attacks as they unfold. And one of the most effective ways to do that is with what’s known as MITRE Adversarial Tactics, Techniques, and Common Knowledge (the MITRE ATT&CK® framework). When studying the MITRE ATT&CK® matrix, we learn much about what an ideal network detection and response (NDR) tool should provide.
What is MITRE ATT&CK®
MITRE ATT&CK® is a clearly defined knowledge base of the techniques and tactics digital attackers are known to use in real-world attacks. The framework is used by organizations around the world to better identify the distinct stages of a cyber-attack. Because most attacks will use some aspect of the ATT&CK® matrix over time, a capable enterprise NDR solution can actively recognize the various stages of a digital attack.
MITRE ATT&CK® currently consists of 14 tactics within digital attacks. Each facet consists of several techniques—ranging from a low of seven techniques to a high of 42. There are several sub-techniques as well. Here are the current 14 tactics:
Reconnaissance: Learning about the target, such as scanning externally facing applications.
Resource development: A stage of preparation, such as creating social media accounts that will be used during the attack to cyber exploit development, etc.
Initial access: The act of getting into an endpoint or workload. This could be as simple as a phishing attack to something as complex as exploiting a weakness in a networked application.
Execution: The attacker has gained initial access and is now running malware or attack code within a system controlled by the targeted victim.
Persistence: Now that the attacker is in, they want to remain in the targeted organization. They do this in many ways, from creating new accounts to hijacking operating system processes.
Privilege escalation: The attacker looks for ways to increase their level of permissions. For instance, they may look for ways to go from a standard user to an admin.
Defense evasion: The attacker uses techniques to remain hidden, such as deploying a container to hide within and attack systems from.
Credential access: The attacker tries to get account access by stealing or even guessing usernames and access.
Discovery: The attacker is surveilling the environment from the inside to learn as much as possible.
Collection: The attacker uses techniques that typically involve using scripts to automatically gather information stored locally, in the cloud, or in volatile memory.
Command and control: The attacker can send commands and receive feedback from the systems compromised within the victim’s environment.
Exfiltration: Often, after data is gathered, the attacker will package the data for stealing, oftentimes compressing or encrypting it so systems don’t recognize it as it traverses a network.
Impact: This is the outcome of many attacks and will range from website defacement to data manipulation to deny access to a service to encryption of data for a ransomware attack.
Plixer Enterprise Platform and MITRE ATT&CK®
The ideal NDR solution such as Plixer Enterprise Platform certainly has both capabilities to detect and respond to attacker actions, such as when the endpoint is accessing a bad domain or when the threat actor moves laterally via common ports and protocols like RDP or SAMBA across north-south and east-west traffic. Any ideal NDR can identify exfiltration techniques, such as when data is being collected before being stolen, or communication across protocols used to transfer data.
By leveraging NetFlow metadata, Plixer can detect these attack techniques and map them into the MITRE ATT&CK® framework.
The below pictures show the alarms being mapped to MITRE ATT&CK®.
Bad Domain Access

Lateral Movement

Accumulation

Data Exfiltration

The benefits of Plixer with MITRE ATT&CK® mapping capabilities
With MITRE ATT&CK® mapping, the security team can identify the threats and categorize them accordingly beginning at an early stage of the attack, such as when network scanning and bad domain access are done. They can also be categorized at later stages as well, like during data accumulation and data exfiltration.
Since Plixer leverages NetFlow, a lightweight protocol, enabling MITRE ATT&CK® coverage without the high costs and heavy lifting that is required by packet-based NDR solutions.
Lastly, MITRE ATT&CK® mapping that is delivered by Plixer can be used by the organization to measure the maturity and effectiveness of an organization’s SOC. By performing tests against each of the techniques outlined within the MITRE ATT&CK® framework, an organization can test the effectiveness of its SOC and defenses against the cyber threats they are likely to face.
The following shows the MITRE ATT&CK® mapping in the Plixer Enterprise Platform.
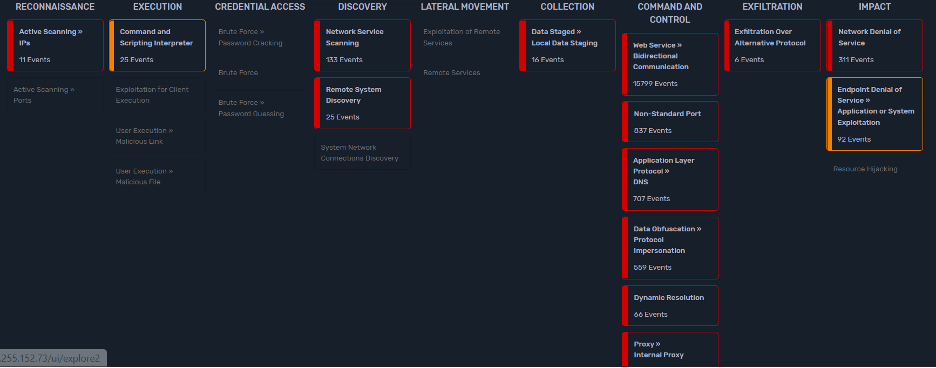
Plixer Enterprise Platform is a powerful NDR and a focus on the MITRE ATT&CK® framework makes it not only possible but much more likely to spot attacks before they get too costly or damaging.
Click here to try the MITRE ATT&CK® framework mapping on your network.