If you are familiar with the MITRE ATT&CK framework, then you know most attackers will follow a general sequence of steps in order to carry out an attack. It’s typically along the lines of gaining entry, performing recon, moving to vulnerable targets, doing bad things, and exfiltrating data.
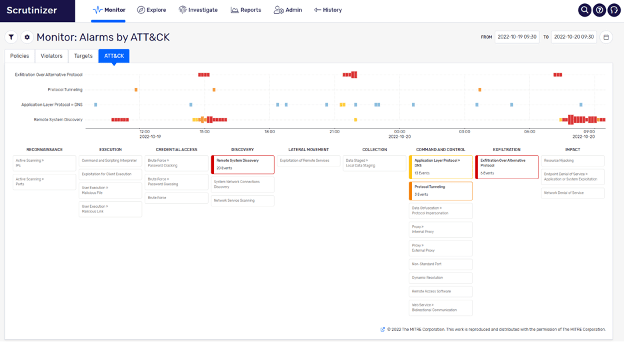
Most organizations put a lot of effort into securing their perimeter but have relatively little in the way of inter-network detection capabilities. This is where Plixer not only performs perimeter detections but also provides significant detections for lateral movement. Let’s investigate how Plixer accomplishes this.
- Port Scan detections – There is a broad type of port scan detections that Plixer monitors for. From your noisy XMAS scan to your stealthy FIN scan and everything in between. Even a simple usage of PING can get picked up and alerted on when it’s used outside of typical usage thanks to our machine learning.
- Brute Force – Examining flow behaviors that may indicate a brute force password attack on an internal IP address. This is accomplished by examining the flow, byte, and packet counts being exchanged in short-duration completed flows between one source and one destination, with specific behaviors observed for common attack vectors such as SSH, LDAP, and RDP.
- Worm Attack – Identifies possible worm behavior from a host by watching the internal connections between hosts. Worms are malicious software that replicate across hosts and can lead to additional security risks including data loss and botnet activity. Plixer monitors behavior on a per-host basis for this type of behavior.
- Worm Propagation – What happens when a target of a worm attack becomes the initiator of a second worm attack? The worm is most likely propagating. This type of detection can be invaluable when an attack is ongoing.
- Different Protocols – Are there certain protocols not in use on your network? Maybe you don’t use PGP anywhere. So, what happens when an attacker uses it to encrypt data transmission? No problem, as Plixer will alert that there is a previously unused protocol now in use on the network.
- ML-based anomalies – Arguably the most potent and best way to detect lateral movement. One of the biggest issues with detecting this activity is that different internal hosts behave differently. It becomes challenging to apply notification thresholds and distinguish between heavy and anomalous usage. This is where Machine Learning comes in. By generating and maintaining models of host behaviors, Plixer is able to easily distinguish between the two. This leads to more accurate detections and better use of an analyst’s time.
Detecting internal, nefarious activity can be challenging, especially when an attacker has valid credentials and is actively trying to cover their activity. However, thanks to its use of network-based monitoring technologies combined with the use of Machine Learning, Plixer is able to easily detect lateral movement within any network.
Interested in learning more about Plixer’s Lateral movement detections or are you curious to find out other ways we are able to protect networks? Schedule a demo today.