You and I both know that AI is all the buzz today. Artificial Intelligence (AI) is quickly fueling the evolution of today’s high-octane environment.
Being able to effectively monitor and manage today’s cyber threats is a monumental task. Every day I talk to people whose pain points are similar. They don’t have the budget or resources needed to effectively deal with this onslaught of activity that their team is facing. It makes sense that AI/ML in threat intelligence is what today’s SecOps teams are leveraging to deal with zero days and other unknown APTs in their network.
So are your enemies . . . . . . .
Clearly, cybersecurity and AI go hand-in-hand. It’s also a tool that is being used by cybercriminals and they are doing it at a rate that is faster than security experts can keep up with.
Around this time of year, it’s common for me to work with clients who are in the process of mapping out next year’s budget, and, as you guessed, strengthening their security posture is a big part of our discussion. Of course, the AI/ML side of cybersecurity is fluid and I would have to wrangle a bunch of experts to even make a dent in the discussion, but here are a few ways that cybercriminals are using AI to infiltrate and exploit our networks.
Here are a few ways we’re seeing attackers use AI/ML
“Hacking into a network used to take months. But with AI and machine learning (ML) technologies on their side, cybercriminals can see this time span reduced to a matter of days. As more AI-enhanced attacks are orchestrated, the techniques used in these events become increasingly available and inexpensive for more and more cybercriminals.” –Fortinet
Deepfakes and Social Engineering
Although the technology is coming of age, we’re not seeing voice or video examples of deepfake directly on the reconnaissance side. Where we are seeing this is in the sophistication of phishing attacks. As time progresses, it will become harder to determine legitimate emails from malicious ones. This is because dark AI/ML can learn enough about you to accurately imitate a trusted personal source. Phishing emails using machine learning can impersonate a boss, coworker, friend, or reputable organization with increasing precision.
AI-Supported Password Guessing
We all know that user-generated passwords are the most common method employed to protect resources online. Unfortunately, there is already a boatload of methods designed to guess passwords.
Ahhh the simpler days of brute force password attacks. Don’t you miss them?
Today’s enemies are smarter and are using AI-powered password guessing like PassGAN to get the upper edge. PassGAN uses deep learning to guess passwords after being trained on a set of known passwords from two large leaks in the past and reports tell us that it was able to expand the number of correctly guessed passwords by 20-25% when combined with current state-of-the-art methods.
Using ML and AI to build their own environments to test and improve on their own malware.
Basically, it’s a “you can’t play in my sandbox” type of thing. As the level of attack sophistication grows, so are the network tools supporting it. Using machine learning, hackers can automate some or all of the data breach processes, including:
- Vulnerability discovery—finding a weakness in the targeted network
- Initial exploitation—exploiting the weakness to gain access to the network
- Targeted exploitation—finding and exploiting vulnerabilities within the network
- Data theft—removing sensitive or valuable data from the network
Simply put, automated and scripted techniques can also exponentially increase the speed and scale of a cyberattack. Attackers are moving to automate the entire process of mapping networks, discovering targets, finding vulnerabilities, and launching a custom attack and this significantly increases the volume of attacks even a single bad actor can pull off.
Moving forward . . . .
It’s clear that AI/ML will extend the scale and sophistication of cybercrime. So how do you position your company to better deal with the unforeseen future? Here are a few thoughts.
Scalable visibility as a foundation
You can’t protect what you can’t see. Find and deploy a solution that will give you complete network visibility. In the past, technology like probes have been the go-to source of truth, but with the evolving footprint of network flow data, like NetFlow & IPFIX, is become preferable. Not all flows are the same, so make sure your tool supports all the various flow types and can easily add other observation points to the mix.
AI/ML
Make sure the solution you choose is utilizing AI/ML learning to filter out the noise and gives you and your team clear, actionable data. As I mentioned earlier, it’s almost impossible to have the physical team and resources to monitor your data. You need some help.
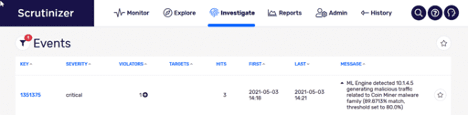
Integration
How does the tool integrate into your company’s workflow? Make sure it supports common industry standards like the MITRE ATT&K framework, adds context with outside threat feeds, and physically integrates with your current toolset.
With the worry of AI becoming a “go-to” tool in today’s cyber-underworld, having real-time visualization across your network is important but is less effective unless you employ similar AI to help combat the new enemy. It is nearly impossible to gather a physical army to combat this. As I mentioned before, AI/ML not only plays a big role in your cybersecurity footprint but it’s also a big part of your enemies. When you are evaluating tools make sure to ask about how they are leveraging AI/ML. Are they able to easily add context to a detected abnormality or do you have to click through multiple applications? Are you looking for conversation-rich visibility along with the flexibility to integrate that data into your current environment? Why not evaluate Scrutinizer?


