We’ve seen a lot of coverage regarding the growth of Extreme Networks lately. Between their recent acquisition of Brocade and Avaya, it would appear that they are serious about expanding their product lineup to increase performance and network visibility; by means of the type of NetFlow exported by their devices.
I’ve recently heard Extreme mentioned more and more in conversations with our customers. I found that many individuals enjoy using Extreme’s S-Series, N-Series, and K-Series devices on their network.
What version of NetFlow is exported?
Extreme’s S-Series, N-Series, and K-Series devices all export version 9 NetFlow. V9 not only offers more visibility, but does not operate on a fixed template like V5. Instead, the templates exported by V9 are dynamic, allowing for more detail to be exported to your NetFlow collector.
S-Series, N-Series, and K-Series NetFlow configuration:
Now down to the good stuff! Extreme has kept this configuration fairly simple for its users. Following the guide offered by their website, we can begin to configure the device using the below format:
# netflow set netflow export-interval 1 set netflow export-destination 10.20.30.40 2055 set netflow export-version 9 set netflow port ge.2.110 enable both set netflow template refresh-rate 600 timeout 1 set netflow cache enable ! end
In this example, the data being captured for export is on ge.2.110.
The export destination will be the IP of your collector or tool, followed by the port it is to be received on.
In this case, they have chosen port 2055, which is a common port used in collection. As long as your destination tool is set to listen on the port that you reference as the destination, you should be able to view your data as it is sent to your collection tool.
For the S-Series, N-Series, and K-Series, the “primary” and “management” values need to be included.
interface vlan.0.192 ip address 192.168.0.1 255.255.254.0 primary management no shutdown exit
The above configuration can be found in Extreme’s recommended configuration.
This is all good and dandy, but what can I do with it?
So glad you asked!! What’s the point of going through all this? The types of details you can view depends on the type of tool you send the data to.
Here at Plixer, we use Scrutinizer. Scrutinizer allows for device-specific reporting as well as 1-minute data intervals.
Below I’ve used Scrutinizer to run an Applications Defined report across all my devices.
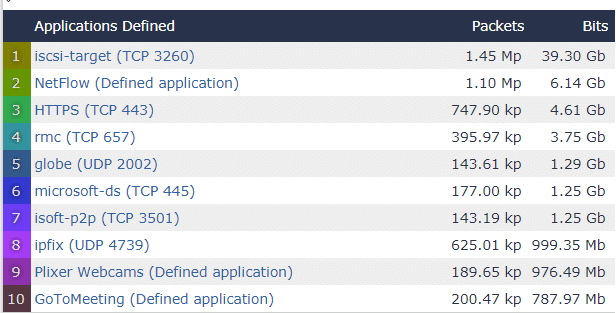
Here I’ve only displayed the top ten but Scrutinizer displays every conversation that matches the filter.
The above looks like normal traffic for our network; however, you can bet that if I saw Facebook, Netflix or Instagram on here I would continue filtering to find the users wasting space on my network.
Though Scrutinizer will alert me to any thresholds I’ve created or alarms I’ve adjusted to send an email notification; I can also view them on the Alarms tab.
From here I can easily view violations, violators, time it occurred, etc. and then jump to a report for even further investigation.
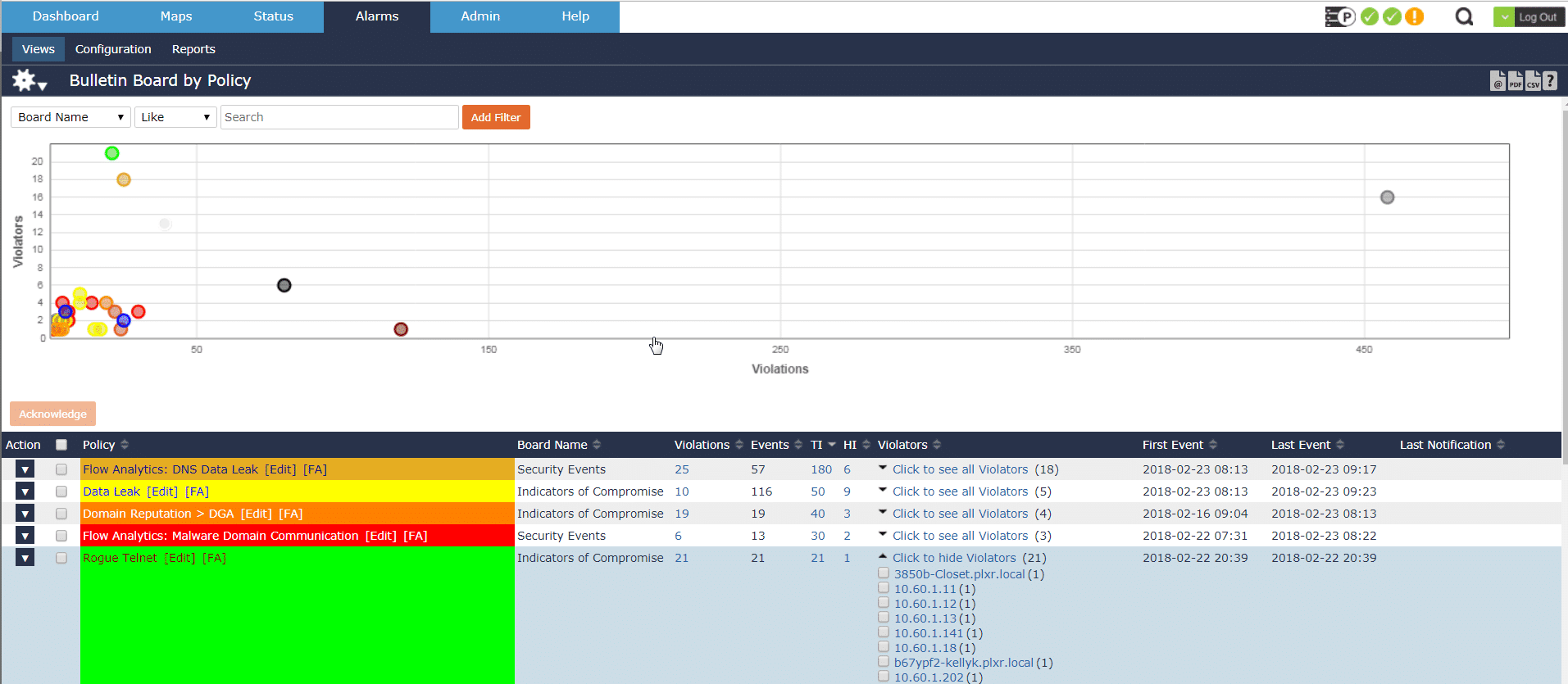
NetFlow plays an important role in increasing the performance of our network and security teams by reducing our mean time to know, limiting risk, and monitoring bandwidth across many different device types.
Take a look into Scrutinizer if you would like to review NetFlow traffic generated by your own Extreme devices.