If you work on a corporate security team, endpoint security is an important framework to understand. After reading this blog, you’ll know the ins and outs of this framework, including why it’s crucial to modern networks and the best practices to implement and maintain it.
What is endpoint security?
Endpoint security is simply a method of protecting the corporate network by individually monitoring and protecting user workstations, mobile devices, and more.
This method consists of a central platform where security teams can manage and monitor each endpoint. This typically, but not always, means that a client or agent is installed on each endpoint (although it can cause problems—more on that later).
Solutions focused on endpoint security may include capabilities such as:
- Endpoint encryption
- Network access control (NAC)
- Endpoint detection & response
- Data classification
- User control
Endpoint security vs. antivirus/firewall
So how is all this different from deploying antivirus and/or firewalls on each user workstation? Well, some schools of thought do include antivirus and firewalls under the endpoint security umbrella. But endpoint security encompasses other processes as well, such as intrusion detection and behavior monitoring.
This framework is also distinguished from network security, in which security policies and solutions are applied to the network as a whole. In the endpoint security framework, security policies and solutions are applied to individual devices.
Why is endpoint security important?
Modern networks are tricky to secure. Traditionally, networks were much more static and had an easily definable perimeter.
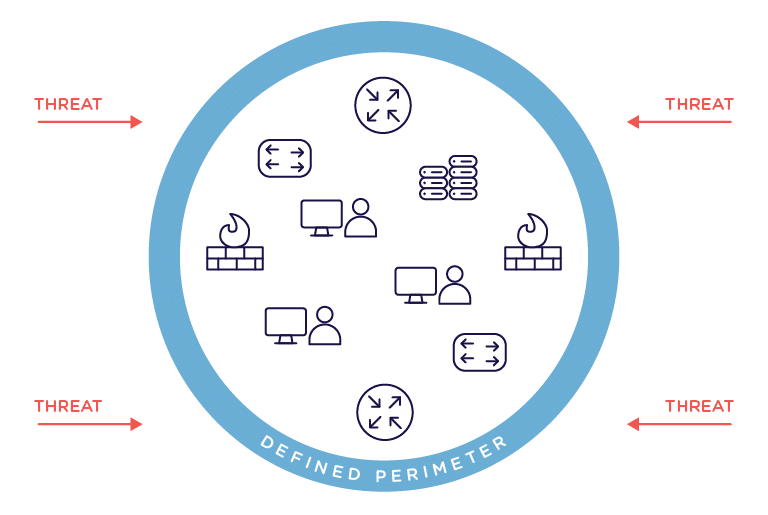
But now, we have to worry about mobile devices, IoT, cloud, insider threats, and more. This results in an ever shifting and hard-to-define perimeter.
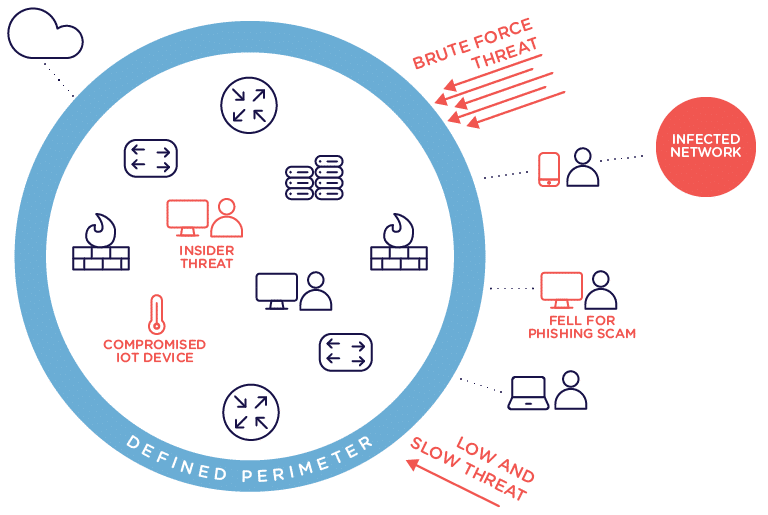
Endpoint security shines in these environments. By protecting individual devices instead of focusing on the perimeter only, you can enjoy the benefits of modern networks while keeping risk low.
Challenges
One big challenge with endpoint security, as I mentioned above, is deploying agents on every endpoint. This often causes significant performance issues and often causes more problems than it solves. Furthermore, agent software may typically be supported by only 30% of the network devices in a traditional environment. But now with IoT on the rise, that number is shrinking to about 10%. And to make matters even worse, there are also instances where placing software on a device could void certifications. For example, placing agent software on medical devices could void the FDA certification. Luckily, solutions like Great Bay are agentless and avoid these problems entirely.
Here are some other challenges with endpoint security.
Lack of visibility: There is an ever rising number of vulnerabilities on today’s networks, and the attacks are more sophisticated, too. Complete visibility into every corner of your network will help you detect breaches earlier, giving you more time to respond.
Ad-hoc PC management: Without any PC management system, it becomes harder to make sure all employees are keeping their software up to date. With inconsistent PC configurations, it becomes harder to solve problems.
Little or no automation: As companies grow, so will their number of endpoints. Unfortunately, many companies neglect to automate manual tasks. These manual tasks snowball into a huge workload for the IT and/or security teams, even though their attention should be focused on more critical issues.
Poor security culture: Security and convenience are in a constant push and pull. But many companies without a strong security culture will completely sacrifice security for agility. This quickly becomes a dangerous situation when you have employees connecting to the network with their own mobile devices.
Endpoint security best practices
Now that we’re familiar with the challenges of endpoint security, let’s cover some best practices for implementing this framework. Some of these are basic security hygiene, but are nonetheless important to remember.
Establish complete visibility of your entire network: Establishing visibility into all your network endpoints is important. But what about visibility into traffic to and from endpoints? You need to know not only what is traversing the network, but precisely where it is doing so. With both real-time and historical data on this, you’ll have a much better picture of your devices’ behavior.
Keep systems updated: Patch management is a challenge in itself, but critical. Have a solution in place that allows you to push updates out to user workstations. If it’s too disruptive to the business to update systems immediately, establish a regular window to batch patch.
Educate employees: Social engineering attacks aren’t going away. Teach employees the telltale signs of phishing attacks. In addition, teach basic security practices like changing passwords regularly and locking your computer when you’re away from your desk.
Enforce least privilege: The least privilege approach is particularly effective when you have IoT devices on your network. Give endpoints exactly the level of access they require. If any endpoints access something against policy, it’s an obvious red flag.
Location awareness: In addition to determining security level by user, it’s good to determine it from the context in which the user is connecting to the network. For example, a laptop may have different policy levels depending upon whether the user logged in from inside the network, from outside the network, or connected via VPN. The specific internal location (e.g. switchport, IP subnet, VLAN, SSID) can drive policy, while location changes (especially frequent ones) are critical to understand the pervasiveness of detected issues.
Concluding thoughts
The endpoint security framework is another method at your disposal for securing your network. If you would like to see how we can help you improve your endpoint security—without agents—or how we can tie full network visibility into your endpoint security strategy, request a demo here.





