An ever increasing attack vector in the healthcare industry are attacks against open or unsecured RDP connections that allow a bad actor to gain a foothold into the network and use this to propagate malware or export the client via ransomware. In this blog, you’ll find some simple-to-follow workflows that you can use to identify and remediate any potentially vulnerable servers.
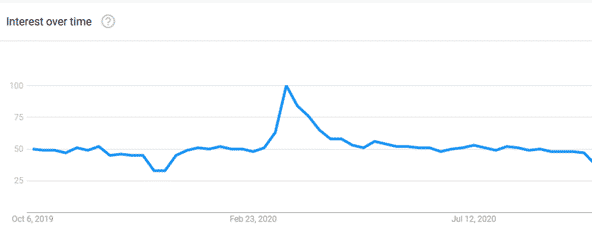
It appears there was a sudden uptick in interest around RDP right at the beginning stages of quarantine, coinciding with the sudden increase in these attacks.
What is RDP and how do RDP attacks work?
RDP is a remote desktop protocol used by Windows-based machines. This allows an admin to remotely view the desktop of another server and use it as if they were physically consoled into the machine. This can make your life simpler because it allows you to download, install, and use applications not located on your local machine.
The problem is that some of these servers can be remotely accessed over the internet and some use very simple passwords that can be easily brute-forced.
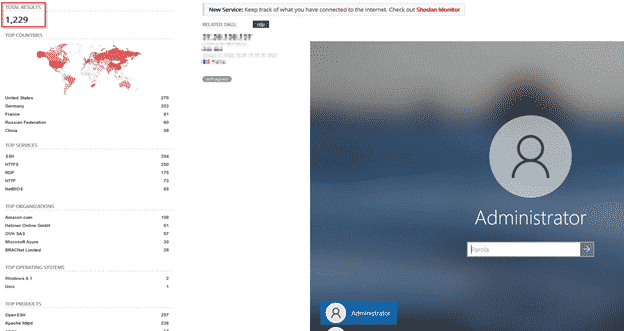
A quick search on shodan.io (an online tool that routinely scans the internet and finds which services are open on which IPs) shows 1279 open RDP sessions. It even shows some that have administrator credential access.
An attacker could gain a foothold by simply guessing the correct password, but typically this is done through other nefarious means such as dictionary attacks and various scan attempts.
RDP attacks in the wild
Just in the last few weeks, there have been some major healthcare industries hit with large ransomware attacks that have cost companies millions of dollars. Most (if not all) of these attacks got their foothold into the network via RDP. ESET recently found a huge uptick in these attacks.
The company has tied the spike in attacks to the COVID-19 pandemic. With lots of office workers forced to log in from home, RDP has become a common way for them to access machines back at the office, it explained. It distributed a graph showing daily attacks against unique clients rising from just under 30,000 in December to over 100,000 during May.
—Infosecurity Magazine
Since I’m a bit of nerd and was interested in exactly how prevalent these types of attacks were, I decided to spin up a honeypot on a segregated license on my network and within just a few minutes, I was already experiencing attacks.
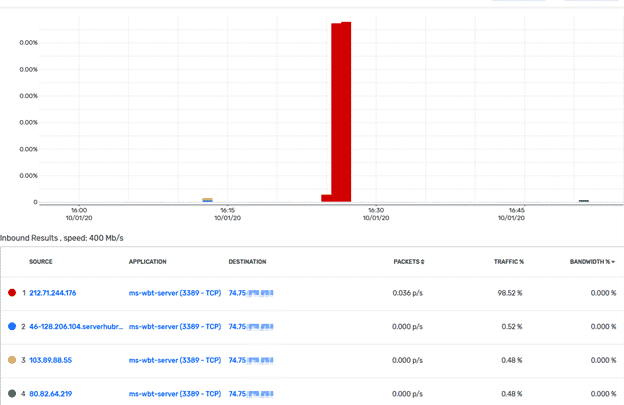
As shown above, a few attacks immediately tried to probe 3389 TCP on my lab network. Using Plixer Scrutinizer’s new PSI machine learning algorithms, I was quickly alerted to some new and unusual traffic.
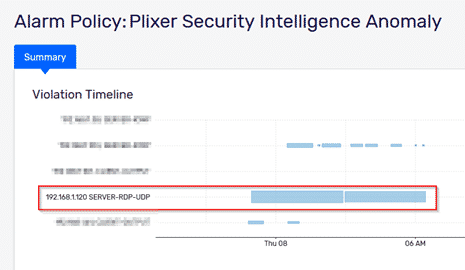
One of the many benefits of ML-based detection is that it didn’t require any special tuning on my part (I didn’t even have to tell it I don’t expect RDP to that host). I simply trusted the models to do their job and was greeted with an easy-to-read, actionable alarm. As always, I recommend viewing the best practices for your network and constructing a game plan that fits your need, but hopefully this helps you lock down applications that may leave you vulnerable.
Healthcare attacks moving forward
The healthcare industry is one of the many verticals seeing an uptick in RDP attacks and everyone should practice proper network hygiene to combat them. What attacks do you think are going to be the next big thing? Let us know and see how we can help!




