This is part #1 of a two part series on detecting P2P botnets with NetFlow. For years botnets such as Zeus and Spyeye made use of a centralized command and control (“C2”) server. This approach to botnet management was easily detectable using reputation services and other black-listing technology. While many botnets still use a traditional C2, a new breed of botnet has emerged that removes the need for a C2. These botnets make use of peer-to-peer technology to download configuration data and commands as obtaining the C2 IP to upload stolen information to the attacker. In part #1 of this blog series we’ll explore how P2P botnets work then cover detection and mitigation of P2P botnets in part #2.
This is part #1 of a two part series on detecting P2P botnets with NetFlow. For years botnets such as Zeus and Spyeye made use of a centralized command and control (“C2”) server. This approach to botnet management was easily detectable using reputation services and other black-listing technology. While many botnets still use a traditional C2, a new breed of botnet has emerged that removes the need for a C2. These botnets make use of peer-to-peer technology to download configuration data and commands as obtaining the C2 IP to upload stolen information to the attacker. In part #1 of this blog series we’ll explore how P2P botnets work then cover detection and mitigation of P2P botnets in part #2.
Traditional botnets such as Zeus made use of a domain generation algorithm (DGA) to calculate the command and control server’s domain name. Security researchers could decode a given botnet’s DGA to anticipate the domains to which the infected machines would connect. An enterprise could detect and mitigate infected hosts by looking for DNS queries against the known DGA generated domains. Examples include:
serva4ok.server2.eu servicespaypal.be sfimnakedgirls.com tongomario.com top.got-game.org topnew.got-game.org
Recent Zeus variants such as Gameover remove the C2 server and thus the ability to match against known domain names.
But before we go too much further, let’s cover the modus operandi of the modern P2P botnet herder.
Rise of Do-It-Yourself (DIY) Malware
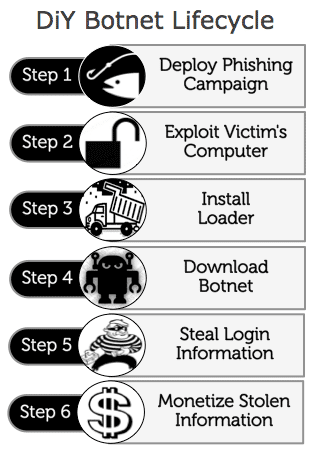
The professionalization of malware has begun. Attackers no longer need to write their own malware. For the right price or with the right connections, anyone with the proper motivation and basic technical know-how can deploy a successful cyber-crime campaign. The diagram below illustrates the steps involved in deploying a botnet for credentials theft purposes. Note the use of commercial DIY software at almost every step. DIY malware frees the attacker to spend more time and energy managing the spam campaign and money mules leading to greater productivity overall.
Step #1 (Deploy Phishing Campaign)
Botnets have no innate ability to spread or install themselves on the victim’s computer. This much be accomplished by convincing the victim to click a link or executing an attachment in email. Malware toolkits such as Cutwail are used to distribute a link or malware attachment. The attacker formulates an email to look like an invoice, account update request, or even an unpaid bill…
Step #2 (Exploit Victim’s Computer)
Of the millions of emails sent out in a given campaign, it’s inevitable that many users will click the link or open the malware executable. Once the user clicks the link, toolkits such as Blackhole are used to find exploits on the user’s computer. Using Javascript, the user’s browser will download a variety of exploits trying each until one is successful. When a successful exploit is found the malware code is downloaded and run locally. Again, much of the exploit process is automated by sophisticated DIY malware such as Blackhole. The screenshot below shows a Blackhole dashboard used to inform the attacker of success/failure rates of various exploits. This allows the attacker to tune the exploits that are tried and in what order to improve the effectiveness of the phishing campaign.
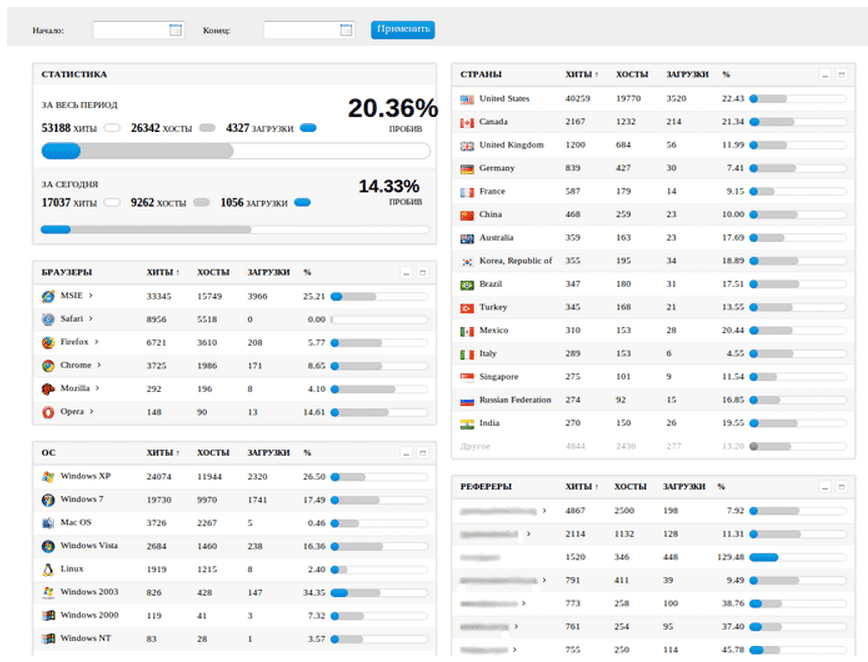 source: SecureWorks, 2012
source: SecureWorks, 2012
Step #3 (Install Loader)
![]() The exploit toolkit doesn’t usually install Zeus directly. Installation of the botnet itself is performed through the use of a “loader” such as pony. In addition to managing the download and installation of the botnet code, Pony also attempts to mine the victim’s system for existing stored credentials. Status of the malware download and any stolen credentials are reported back to the Pony C2 server. As with the Cutwail and Blackhole toolkits, Pony provides a sophisticated web-based management interface for configuring and maintaining pony installations. Loaders such as pony are designed to be very difficult to detect for both anti-virus and network-based intrusion detection.
The exploit toolkit doesn’t usually install Zeus directly. Installation of the botnet itself is performed through the use of a “loader” such as pony. In addition to managing the download and installation of the botnet code, Pony also attempts to mine the victim’s system for existing stored credentials. Status of the malware download and any stolen credentials are reported back to the Pony C2 server. As with the Cutwail and Blackhole toolkits, Pony provides a sophisticated web-based management interface for configuring and maintaining pony installations. Loaders such as pony are designed to be very difficult to detect for both anti-virus and network-based intrusion detection.
Step #4 (Download Botnet)
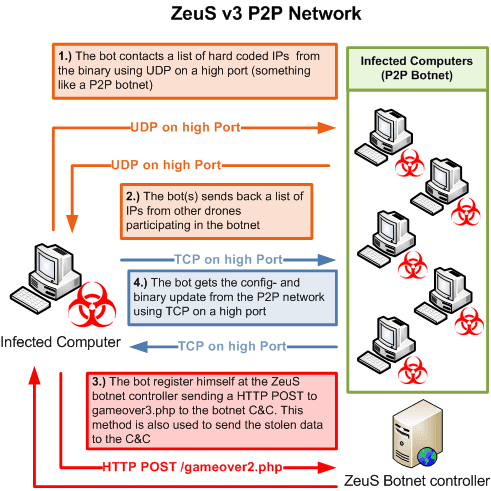
The next step is to download and execute the botnet code itself. In the case of a P2P botnet such as Gameover, the botnet first tries a list of hardcoded peers then falls back to a DGA list. The Gameover botnet uses TCP/UDP ports 10,000 through 30,000. The diagram below provides an overview of the Gameover P2P connection process:
source: abuse.ch
Step #5 (Steal Login Information)
Every step up until this point is in support of step 5. Zeus includes a variety of features designed to enable the theft of login credentials. Some of these features include:
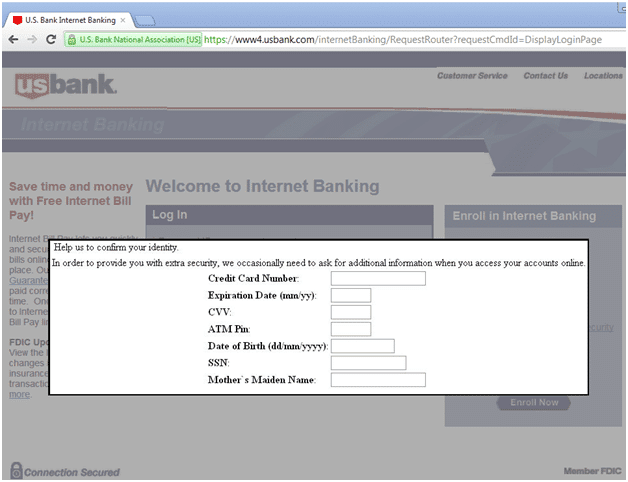
HTTP injection (man-in-the-browser) “webinject”
MitB attacks are perhaps the most dangerous of botnet credential theft mechanisms. The botnet intercepts HTTP connections to banking websites and inserts web-based forms of its own to coax the user into entering information about their account. The attack is effective since the user believes they are “safe” within the confines of their trusted bank account. The example below shows a webinject in action for US Bank:
source: malwarebytes.org
Selective screen scraping
Zeus can be instructed to take screenshots of the user’s desktop when certain events occur such as when the user clicks the left mouse button on a “Login” web form object.
Key logging
Keystroke logging is a botnet staple feature. The attacker can choose to log all keystrokes or only key strokes when the user visits a specific website such as “bankofamerica.com” or “salesforce.com”.
Back door establishment
Zeus can be instructed to listen on a back-door port for execution of commands by the attacker.
Remote code download and execution
In addition to establishing back-door access, the botnet can be told to download additional code, modules, and configuration data.
Credential stealing (http, FTP, pop3)
Zeus will intercept HTTP, FTP, and pop3 activity to enumerate credentials which are then sent back to the C2 (learned from P2P peers).
VNC access
One of the more advanced Zeus modules (and more expensive) includes the ability to access the victim’s computer via VNC.
DDoS toolkit
More recent Zeus variants such as Citadel allow for DDoS capabilities. DDoS is often used to distract the security team’s attention away from the real attack.
Steal form details
Zeus can also be instructed to intercept HTTP form entries as well again based on a list of websites that the attacker finds interesting.
URL redirection
When the user browses to a specific website, the browser can be redirected to alternative websites that can contain forms to capture user credentials.
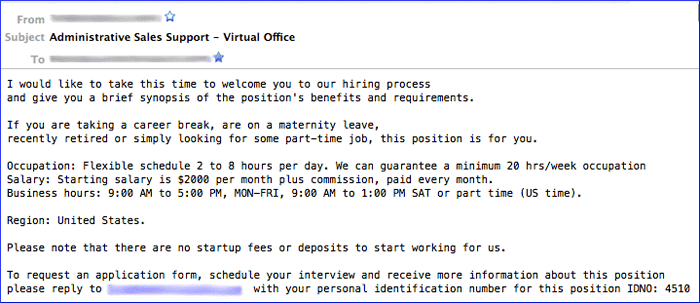
Step #6 Monetize Stolen Information
Stolen credentials aren’t worth anything until they are converted to cash. Credentials can be sold to other cyber criminals or, in most cases, converted to profit through the use of a money mule. Automated Clearing Houses (ACH) are used to siphon cash from compromised accounts. Again, Cutwail or a similar spam sending botnet is used to mine money mules. An example is shown below:
source: SecureWorks, 2012
In Part #2, we’ll discuss methods of combating the process described above. Stay tuned.