Do you have a solution in place for detecting network threats? If you say no, you are not alone. Or maybe you have firewalls blocking the unwanted network traffic. Either way, you may be interested in network behavior analysis, another network threat detection option to consider.
Network behavior analysis is based on traffic patterns, as opposed to the more common signature format of threat detection, providing more flexibility and also quicker response times for new threat patterns.
Network Behavior Analysis
We have a Network Behavior Analysis solution for you in our Flow Analytics solution. It is comprised of a suite of network threat detection algorithms covering many of the traffic patterns that these threats take.
Today I’ll go through some of these algorithms, including a brief description of each and what devices’ traffic you would want to monitor for each traffic pattern.
[table id=17 /]
The above is only a partial list and the Host Reputation Monitor also includes reputation categorizing, some examples of the categories are:
- CnC: Malware Command and Control Server Observed or DGA predicted domains and IPs that are command and control for known trojans. Specifically criminal, differentiated from spyware and user tracking domains which are classified in SpywareCnC.
- Bot: Known Infected Bot A host observed checking in to a command and control server, or exhibiting clear indications of unwanted and criminal code on the host.
- Spam: Known Spam Source We don’t track all spam sources, but those observed sending spam or being rejected as blacklisted are included.
Network Threat Detection Reporting
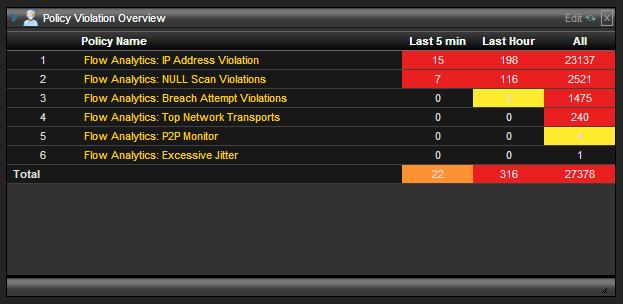
When alarms are generated for network threat violations, alerts can also be generated, in addition to providing visual reporting on network threat detection as shown in the image below.
This reporting shows which network threats have been detected on your network, how often, and when.
If you’re ready to try this solution yourself, just click the Download Now! link, then give us a call at 207.324.8805 x3 and we can help you start detecting network threats.
Also, for more information on detecting network threats, I highly recommend taking some time to read Michael Patterson’s blog on detecting advanced persistent threats.