Have you considered using NetFlow for detecting DoS attacks on your network? Well, let me show you how simple and easy DoS attack detection is with NetFlow security monitoring.
What is a DoS attack?
A Denial of Service (DoS) or Distributed Denial of Service (DDoS) attack is an attempt to make a machine or network resource unavailable for its intended users. Though the processes, motives, and targets of these attacks may vary, generally the intent is to interrupt or suspend services of a host (for example a web server) on the Internet.
DoS attack vs. DDoS attack
DDoS attacks (Distributed Denial of Service) are sent by two or more persons, or bots. DoS (Denial of Service) attacks are sent by one person or system.
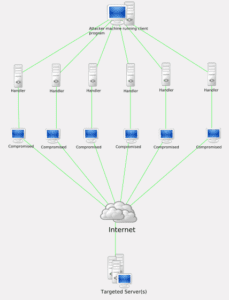
What does a DoS Attack look like?
In the DoS Attack Case Study, the customer was facing a significant decline in server availability with their bandwidth being drained from an unknown source. It was discovered the the DoS attacks were overloading the server with multiple “pings” and other requests which slowed availability.
With their current network monitoring tools, visibility into their server traffic was very limited, leaving them in the dark as to how to fix it.
By utilizing an advanced NetFlow security monitoring solution, the server traffic was quite visible, and soon became apparent that the situation extended beyond just simply taxing the server. The attacks were also utilizing their infrastructure to send additional packets to a location in Korea, literally transforming their servers and flooding all outbound traffic. Compounding the situation was that this flood of outbound traffic resulted in CPU spikes on their firewall.
DoS Attack detection
With a comprehensive NetFlow-based network traffic monitoring and threat detection solution such as Scrutinizer, the IT team was able to accumulate enough data in the first 30 minutes of installation to determine the threat’s point of origin and that the breach was a DoS attack.
The IT team identified the top talkers on the network, including the traffic volume passing through the affected server. Then, by setting thresholds for normal traffic behavior for this server – typical top talkers and their respective typical traffic volumes – and real-time visibility into the network traffic, the threat was immediately detected.
Once the attack was identified, they were able to resolve this instance, and then, leaving the threshold and alerting setup for this DoS attack in place, provided proactive network traffic monitoring for future potential attacks.
And then there are DDoS attacks
Which, by the definition above, is a Distributed Denial of Service, or a denial of service by two or more persons, or bots.
Source: DDoS Prevention
To help detect DDoS attacks, we’ve developed a network threat detection algorithm based on the unique traffic pattern exhibited by DDoS attacks which is available in our NetFlow Analyzer. You can set your bytes deviation, number of flows per source, packet deviation and other variables to detect a DDoS attack in your environment. Reach out to our team to change these settings in a way that best fits your network environment.
To gain visibility during a suspected DoS attack, please download our NetFlow security monitoring solution today.