Last week at the Cyber Security Summit in Denver, I participated in a panel that answered questions being asked by the moderator, David Cass – CISO, IBM. Several hundred people signed up for the event, which is being held again in Boston on November 1st.
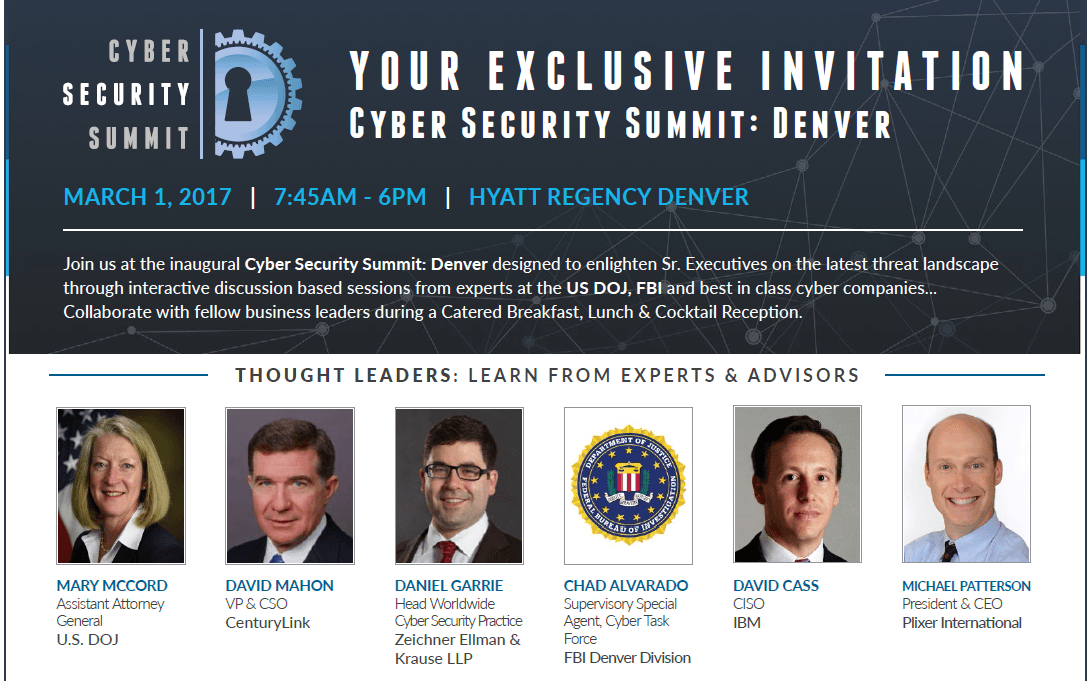
Below are the panel questions and the answers I provided.
Question: What are some of the potential legal issues or potential threats surrounding big data?
Answer went something like this: We all are required to agree to an end user license agreement, or EULA, before we can use new devices or software. The manufacturers like Microsoft, Dell, McAfee, Plantronics, and hundreds of others often write their EULA to give them the most liberal use of the data they collect from our devices. In reality, nobody reads the EULA, and therefore we sometimes don’t consider what data is collected or how it is used. Many mobile phone carriers use their devices for both work and play. The applications we install on them frequently collect and exfiltrate the personal and private data that can be found on the device. This is concerning because in most cases, business and personal data coexist in this one location. When an app is allowed to access a user’s contact list, consider how many of those contacts are business-related—your best customers, for example. Once they take your data, I could be made available for resale. Even if that information is not actively being sold, it is being stored on someone else’s servers somewhere in the cloud. What about if and when that database is hacked? Remember, as a user of their software, we agreed to the EULA, which likely gives us no recourse if the data they have collected from us is stolen from a third party and suddenly shows up on the dark web. As business managers, many of us are worried about data leakage, but many of us are not considering Big Data collection from third-party applications as a possible source. Consider this. Yahoo this week announced even more fallout from the billion or so accounts that were hacked a few years back. Information taken may have included passwords as well as your employee’s answers to security questions like:
- What was the name of your first pet?
- What is your mother’s maiden name?
- What was your first grade teacher’s name?
We all know that based on human nature, people reuse passwords and security questions. The hack of these third-party databases makes your organizations less secure.
We live in a big data world, where companies want to collect as much information about us as possible. They don’t even know how they are going to use it yet, but they expect over time that they will find ways to use this data to make more money. The more data that is being collected and sits outside of our control, the more at risk we are of this data being breached and used against us.
Question: When it comes to securing IoT devices, where does responsibility lie? Is it with the manufacturer, the user, or both?
Answer went something like this: I believe the right answer is for both parties to hold responsibility. Companies selling IoT devices should comply with several security measures such as hard coding them to communicate only with RFC 1918 IP addresses or the manufacturer’s website. Apple’s Home Kit and Google’s Nest devices have a similar architecture. I think that the default password for each individual device should be a set of 10 or more random characters and unique per device. Devices should connect to the manufacturer’s website every day to receive automated updates, and if the IoT device stops communicating with the manufacturer for a period of time, it should retire itself and stop functioning until there is perhaps a successful update. Levying fines against companies failing to comply with these best practices will be the best method of driving this behavior. It would remove the manufacturer’s ability to try and shift the blame to the consumer.
On the customer side, companies have an important role to play as well. The firewall should enforce source address validation to ensure that IP addresses aren’t being spoofed. Network traffic analysis should be deployed to ensure all traffic to and from these devices complies with least privilege on the most critical assets. Any traffic deviation should trigger a high priority alarm for immediate investigation.
Ideally, I’d like to see legislation forcing manufacturers to disclose in their EULA a complete list of the information they are taking from the consumer and be required to use encryption methods such as TLS that can be decrypted by the company using man-in-the-middle techniques to verify the contents of what they are taking. I’d also like a law that outlines how manufacturers can take information from our companies, as many are currently using the DNS protocol. These practices make it difficult to uncover malware and good laws would make it much easier for detection appliances to do their jobs.
It was a great event and I’m looking forward to the next one in Boston. I hope to see you there.