
Monitoring applications with Plixer Scrutinizer
Monitoring applications is a useful tool in the network administrators tool belt and I’d like to go over how Scrutinizer can help monitor your...

Monitoring applications is a useful tool in the network administrators tool belt and I’d like to go over how Scrutinizer can help monitor your...

This blog will focus on Plixer’s current capability to extract flow from the different solutions Aruba has to offer today. I will go over...
Has management made enhancing your network monitoring toolset with an NDR component a priority for the new year? Have the demands of the pilgrimage...

Microsoft has redone their release cycle format, and although it makes things easier for the end user, it can prove difficult to ensure your...

The purpose of this blog is to de-mystify the hype around machine learning (ML) by exploring three topics: What kind of ML is Plixer...
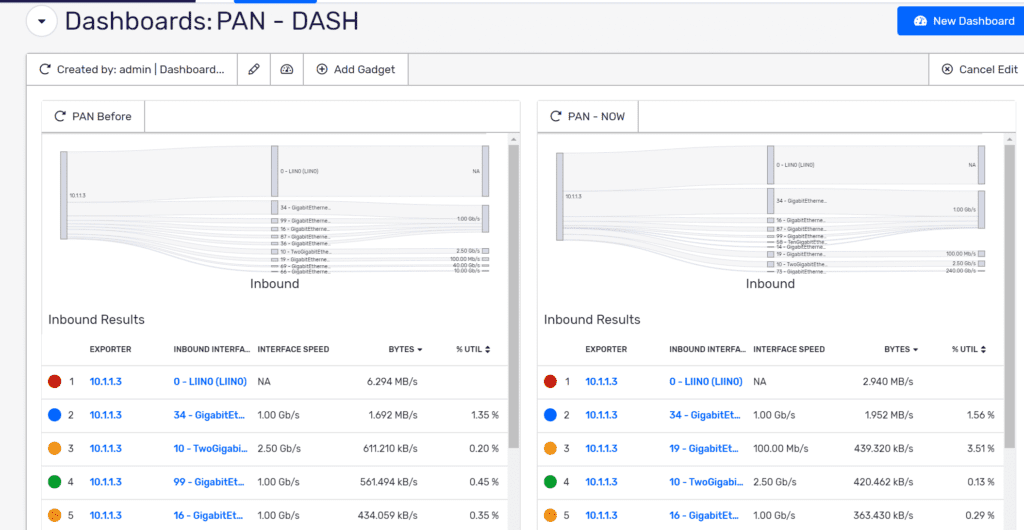
When this pandemic started and nearly the entire workforce went remote, our focus was to maintain the quality of service outside of what was...

Competition generally ends up being good for the consumer. It keeps prices down and forces innovation as vendors compete for market share. A great...

A few years back, Jake Bergeron, one of Plixer’s Sr. Solutions Engineers, wrote a blog about Ubiquiti NetFlow support and how to enable it....
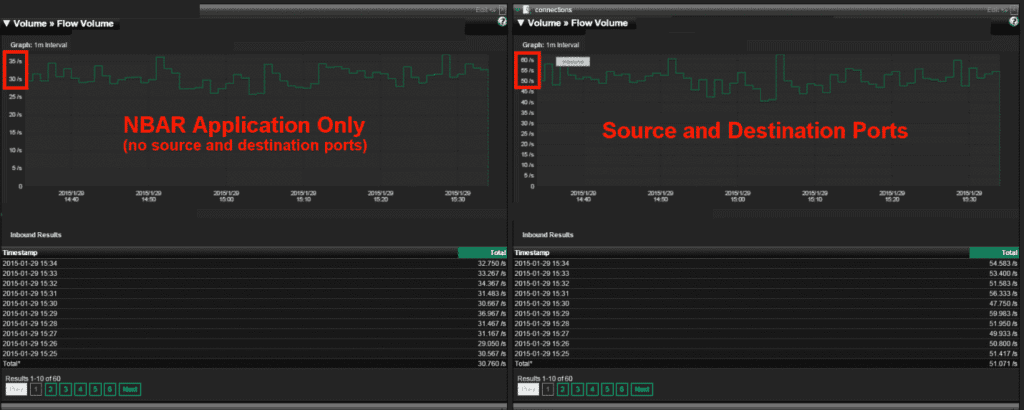
As resource demands and bandwidth speeds in many of today’s network infrastructures continue to increase, many network administrators believe that NetFlow sampling is the only...

As OEMs continue to invest in WAN optimization, what differentiates vendors’ capabilities so that enterprises seek to scale their infrastructure? In this blog, we’ve...