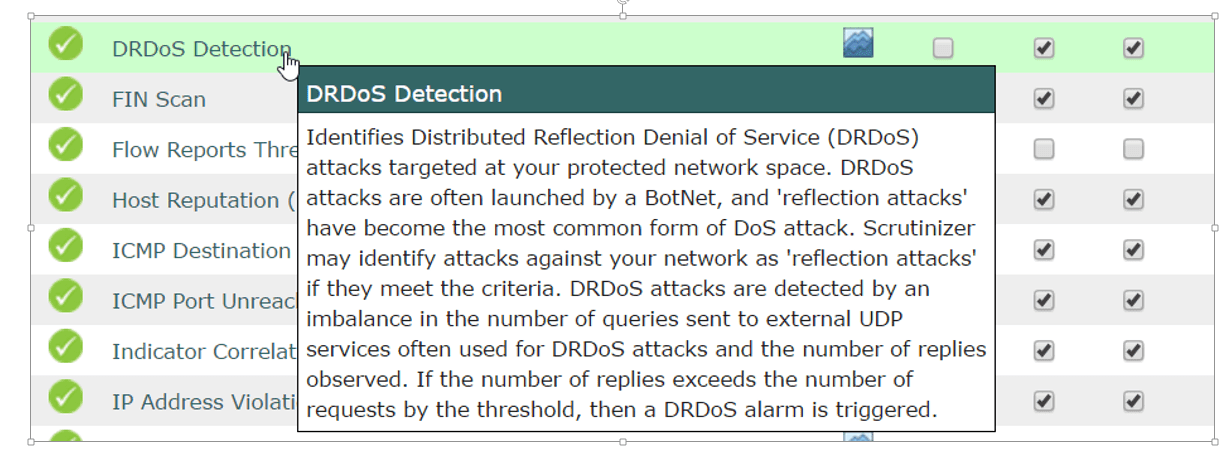
In this line of work I find myself talking with network professionals daily. With this constant exposure to a variety of network environments and people, certain terms tend to float to the surface. Lately DDOS and Reflection DDoS attacks are on the threats to discuss. They are becoming easier to conduct and larger in scale, and due to the lack of network visibility we can clearly see why there would be an upward trend in the frequency of attacks. Today we are going to take a look at a member of the denial of service family, DRDoS (Distributed Reflection Denial of Service) attacks and how we can harness the power of NetFlow to catch and monitor these attacks.
DRDoS Stands for Distributed Relection Denial of Service and is quickly showing itself to be a powerful weapon against networks in every industry. The basic premise of the attack is to spoof the victim’s IP and send UDP requests to various servers or reflectors, so that when they respond they respond to the spoofed IP.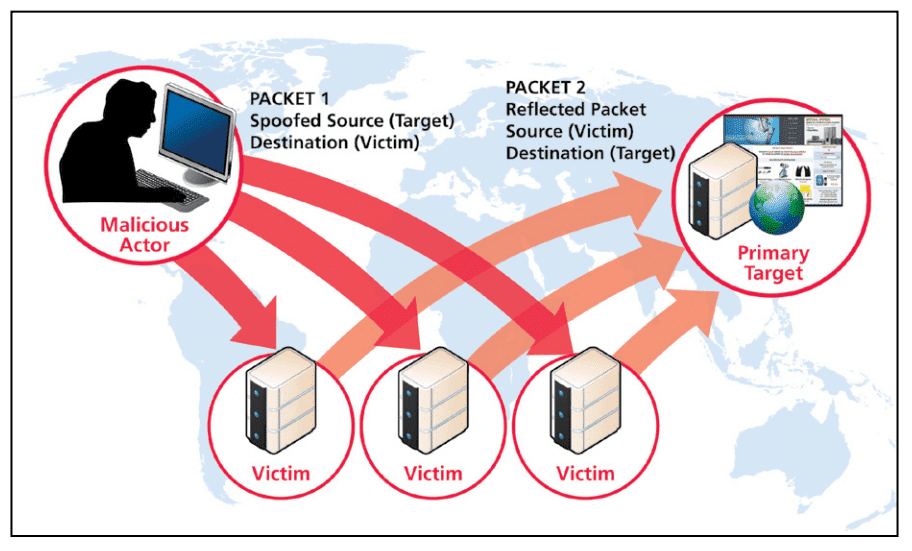
As stated in Prolexic’s White Paper on the Distributed Reflection Denial of Service Attacks
“The malicious actor makes it appear to a victim host server that the primary target is contacting them with a request. The victim host servers therefore respond back to the primary target, which they mistakenly think made the initial request (a spoof). The reflected denial of service attack is called distributed because of the involvement of multiple victim host servers. The attack may be a single actor or multiple actors.”
So with this method a single attacker can inflict massive damage all while having the protection of hiding behind the reflectors.
As of July 19th 2016 Arbor noted that
- An average of 124,000 events per week over the last 18 months.
- A 73% increase in peak attack size over 2015, to 579Gbps.
- 274 attacks over 100Gbps monitored in 1H 2016, versus 223 in all of 2015.
- 46 attacks over 200Gbps monitored in 1H 2016, versus 16 in all of 2015.
- USA, France and Great Britain are the top targets for attacks over 10Gbps.
Some of these DDoS attacks are reportedly tipping the scales at over 500 Gbps! To put that in perspective an average organizations can be taken offline completely with just a 1 Gbps attack.
With the continuous threat of being blindsided by a DRDoS or even a standard DDoS, companies are leveraging technologies like NetFlow to greatly reduce their mean time to know (MTTR) and detect network threats. Having the ability to be alerted when an attack is seen by using behavioral analysis means that an organization can be quick to act, limiting their losses.
The above screenshot is taken with our NetFlow Collector Scrutinizer and shows an example of one of the many algorithms we use to catch nefarious behavior on the network including catching Reflection DDoS Attacks.
We are currently in 2016 which is already proving to be one of the worst years in DDoS history. There is no longer any excuse to stay blind when dealing with network visibility and the possible threats we face. For more information on how to enable NetFlow on your preexisting network gear and take advantage of the 100% visibility offered by Scrutinizer, please contact our team today!