Back in April of this year, the Swift international money transfer network which connects 11,000 global banks in over 200 countries was used to steal $81 million from the central bank of Bangladesh. It appears that for some hackers, banks are a better target for stealing larger amounts of money rather than the individual consumers.
“With financial institutions, the payback is greater. Hackers target financial institutions because the thefts are greater with less effort,” said Mike Vigue, VP of Product Strategy at Bottomline Technologies. “Stealing from retail customers is less efficient.”
Although the infiltration strategies used by hackers continue to evolve and become cleverer, many banks are still trying to protect themselves using traditional defensive measures. For many financial institutions, their strategies weren’t working when they were initially setup, and they aren’t working now. This is why many banks are still losing the fight.
Banks Continue to be Exposed
As long as banks and financial institutions continue to provide on-line services, they will be vulnerable and continue to be hacked. “All financial institutions who run SWIFT Alliance Access and similar systems should be seriously reviewing their security now to make sure they too are not exposed.” According to BAE Systems researchers.
Better authentication and confirmation mechanisms are a great place to start. Finance organizations serious about protecting their 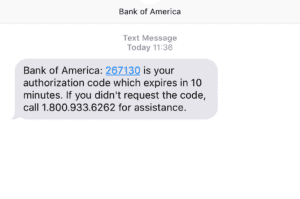 customers require two-factor authentication which involves the mobile phone when logging in to transfer money. As an added measure of protection, when transferring money to a new vendor that isn’t already in the customer’s profile, a text message is sent to the customer’s phone with a code that must be entered into the on-line profile. For a hacker to compromise this process, they would have to hack both the customer’s computer and their mobile device.
customers require two-factor authentication which involves the mobile phone when logging in to transfer money. As an added measure of protection, when transferring money to a new vendor that isn’t already in the customer’s profile, a text message is sent to the customer’s phone with a code that must be entered into the on-line profile. For a hacker to compromise this process, they would have to hack both the customer’s computer and their mobile device.
In the case of the Swift heist, analysis of the code repository uploaded from Bangladesh showed that the malware allowed the hackers to delete records and intercept incoming messages. As a result, the hackers were able to intercept confirming messages sent for printing as a security measure. Sending instead “manipulated copies”, thus evading detection and potentially running away with huge sums of money. source
Better Authentication
Sending an email for confirmation on a money transfer is not ideal. A better strategy is the combination of entering data, received via text on a separate device, into a secure website. This is currently one of the best forms of security because once a machine has been compromised as in the Swift incident; the infection could have access to everything on the PC including email.
An even better authentication process might be adding in human intervention. Consider this: unresolved attacks cost organizations an average of $21,155 per day! This is a hefty multiplier when you consider that it takes more than four months to resolve targeted attacks (source) plus the even longer amount of time leading up to the actual detection. The $21,155 savings per day would go a long way toward a call center with few dozen more people on the payroll to confirm money transfers and help avoid electronic thefts like the $80 million witnessed by Swift.
Late last year, Swift announced a global payment initiative focusing on developing a blockchain roadmap which is used by Bitcoin which has never been hacked. Innovative changes like this demonstrate promise toward securing the banking industry.
Collection of Logs
Beyond building better authentication processes, the finance industry should be offloading the logs that hold evidence of every transaction. In other words, all details on every business critical device should be sent in real-time to some type of SIEM. Even the traffic generated by the critical devices (i.e. NetFlow) should be archived off for routine threat detection and future investigations.
Logs are often the first thing requested when embarking on incident response. Immediately after asking a few questions about the compromise, the security team will want to query the flow collection server or SIEM. These combined systems, contain all of the events that occurred on each mission critical system.
UDP Forwarder
To add additional security, a UDP Forwarding appliance should be inserted between the devices sending logs and the flow collector or SIEM. A UDP forwarder can make duplicates of UDP packets forward them onto multiple collection systems without modifying the source IP address. As a result, in order for an infection to remove the evidence maintained in the logs, it would have to hack the UDP Forwarder to find out where the messages are going and then hack each collection server. Most infections won’t do this and move onto easier targets.
Adding Contextual Awareness
The faster the answers can be sought out, the lower the cost of the security event. To improve speed, security teams need context-aware security analytics which is the process of pouring through logs and other pieces of information, correlating it with other sources ‘context’ to make it comprehensible and actionable.
Context can come in the form of NetFlow, Syslog, proxy records, Amazon AWS logs, DNS lookups, URLs visited, username directories, PTAM information, etc. Pretty much anything that can correlate with a device is context. The differentiator between competitive systems is how easily you can pivot from one piece of context to another. Simplicity and speed result in a shorter Mean Time to Know (MTTK).
Financial Institution Security
Ultimately there never was nor ever will be a 100% reliable cyber protection solution for our financial deposits. There is only “reasonably good” or “better than other banks” protection. If your institution has the best protection, hackers will usually go after an easier target.
Better dual authentication, offloading logs, and improved context will all contribute to a best defensive security posture.