I recently joined Plixer (August 2016) and as part of my onboarding process, received a new cell phone. Over the last two months, on a nearly daily basis, that cell phone has been ringing, showing caller IDs originating from all over the US. When I answer, there is no one on the other end of the line. I find this an interesting phenomenon. If this weren’t happening so frequently I might pass it off as people dialing a number that used to belong to someone else and hanging up. Given the situation, however, I find that highly unlikely. This got me thinking about what could be happening. I have a theory—Short Message Service (SMS) cybersecurity attacks are about to become the next big threat surface.
I believe that bad actors are using automated dialers to compile a list of valid cell phone numbers. Although the Telephone Consumer Protection Act (TCPA) makes this an illegal practice, do bad actors really care? Similar to profiting from the sale of personally identifiable information or email lists, bad actors would profit from the sale of valid cell phone numbers. Additionally, SMS is a platform with a higher likelihood for the success of phishing attacks.
SMS is a target-rich platform for bad actors to use as an attack vector. There is a massive user base with nearly 7 billion mobile subscribers worldwide. In comparison, Radicati Group projects there are currently just 2.5 billion email users. People tend to trust text far more than they do email. As of April 2016, Textedly reports that SMS marketing efforts have a 98% open rate compared to only 22% for email and that people open text messages within minutes of receiving them. This makes SMS a platform ripe for bad actors to exploit. To do this, they just need a database of numbers to target. For instance, in just the last 2 weeks I have received two suspicious text messages that I have since deleted because they appeared to me to be phishing attacks.
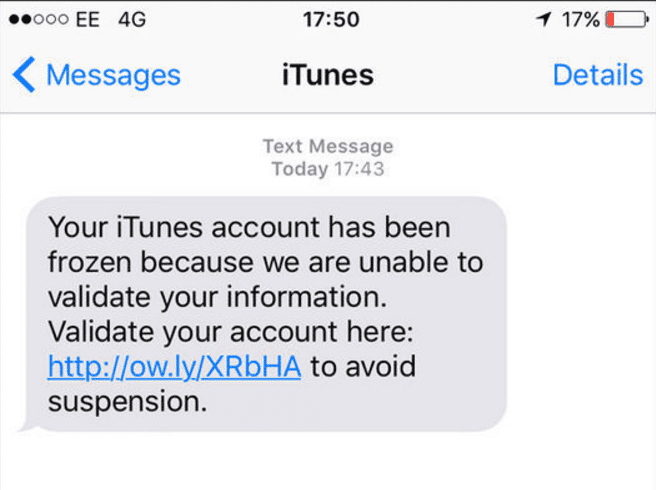
Unfortunately, phishing attacks continue to succeed, which is why they remain a common means of infections for the bad guys. In an effort to help protect users, Plixer created an online game called Click Click Phish. It teaches people how to recognize and avoid phishing attacks. The game shows players how to hover over the link with their mouse and inspect the URLs to determine if they are valid or malicious. This works great when you are on a computer using email, but SMS is a different story. A serious challenge with SMS as a platform is that when you receive a URL via a text message, it is often a TinyURL and there is no way to inspect it prior to clicking on it. As a user, you must make a trust decision based on very little information. You need to make a judgement call on the veracity of the message, which has the potential for disastrous results.
In August 2016, an unprecedented, zero day attack using SMS was discovered and documented. Ahmed Mansoor, a human rights activist from the United Arab Emirates, received a text message with an embedded link. The message, written for and specifically targeting Ahmed, purported to link to secret information about torture of Emiratis in state prisons. Ahmed was suspicious of the message and forwarded it to Bill Marczak, a researcher at Citizen Lab. Investigation of the message determined it to be a very sophisticated piece of cyberespionage, comprised of three zero-day attacks with the ability to remotely jailbreak the phone. Had Ahmed simply clicked the link in the SMS text, he would have given the attackers full access to the phone and every app on it. This was clearly a highly targeted attack, but it demonstrates that SMS is a viable attack vector for malicious purposes and if databases of cell phone numbers are created and targeted, the impact could be severe.

At first glance, it could appear to be a problem specific to cell phones and the data on them. This, however, doesn’t identify the full scope of the potential problem. Consider, for example, the frequency at which people tether laptops or mobile devices to their cell phones to get internet access when WiFi isn’t available. As soon as you connect another device to the phone, you have provided a path for malware to spread. Now let’s say that the tethered device is an enterprise asset—your work laptop, perhaps. Then the SMS breach and subsequent infection also become a problem for the company where you work. If SMS cybersecurity attacks do in fact begin to grow, they could have a profound impact on Bring Your Own Device (BYOD) technologies and security processes.
Time will certainly be the judge of my hunch, but I believe bad actors are already using automated dialers to find and identify valid cell phone numbers. They are looking to create cell phone databases to sell and exploit in the same fashion that email databases were sold and exploited in the past. I believe that SMS cybersecurity attacks are the next big attack vector for bad actors. This will drive a greater need for companies to use tools like Scrutinizer to monitor flow data from BYOD devices as it traverses the network. Book a demo to see how Scrutinizer can help you visualize and secure the mobile device traffic flowing across your network.



