Palo Alto
Palo Alto Networks’ next-generation firewalls coupled with Plixer’s Scrutinizer software enables IT organizations within an enterprise to identify the applications running on their network as well as the end users using these applications. The combined solution can, among other things, identify the users and applications that generate excessive traffic on the network. Plixer works closely with the engineers at Palo Alto Networks to support their flow export. 100% of their unique elements have been translated from PAN-OS to ensure that our mutual customers gain the maximum insight when investigations take place. Scrutinizer complements the Application Command Center (ACC) by providing thorough filtering capabilities and long-term archiving of the exported data.
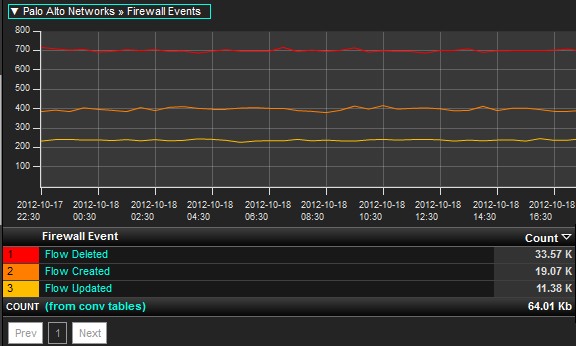
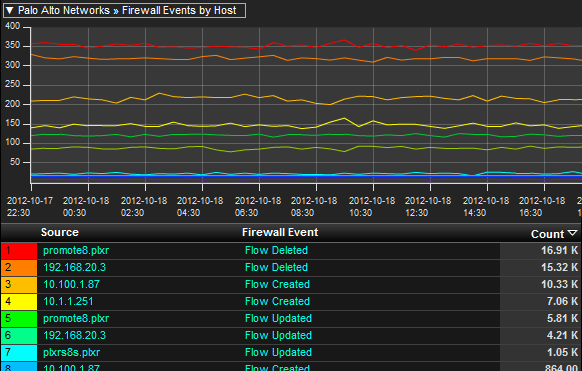
The ability to trend flows Deleted, Created, or Denied, for example, allows administrators to gain visibility into historical baselines on how the Next Generation Firewall traditionally treats traffic headed for the Internet. If an abnormal spike or drop occurs in the above trend, administrators can drill in to find out what machines were involved, and which applications were being used at the time. This data can also be bundled together with multiple firewalls to gain a more enterprise view of the corporate Internet behavior.
Stay up to date on network activity
Administrators can use the above report to set thresholds on volumes of unacceptable ‘denied’ events. If a host causes connections in a way that violates a threshold, unacceptable rates of denied violations can trigger events which lead to notifications.
The combined Plixer and Palo Alto solution also includes:
- Reports on username, layer 7 application, firewalls events, and more
- Distributed collector performance monitoring
- Fast searching to find a host across collectors
- Audit trails of all internal and external traffic
- Access from Scrutinizer to Palo Alto logs in Splunk
Leaders in Network Traffic Analysis
Industry-leading NetFlow features include:
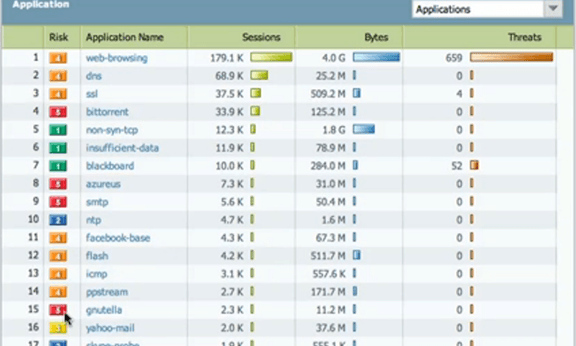
- Application Awareness: They use Deep Packet Inspection (DPI) to identify and separate applications that share ports such as TCP 80.
- Username: If users have to authenticate with Microsoft Active Directory, Cisco ISE, or LDAP, the flows exported by the firewall can be tired to the username. This eases troubleshooting efforts during times of forensic analysis.
- Network Address Translation: This can be a time saver when trying to find out what an IP address was internally before it was NAT’d by the firewall.
- Firewall Event: Report on which flows were denied and verify policies.
- Correlation: Integrate with Splunk and Elasticsearch / Kibana to correlate flows with logs.
All major firewall vendors recognize that flow technology is a primary feature necessary to be a contender in the Next Generation space. Clearly Palo Alto Networks understands which features matter most and has moved quickly to service the needs of their customer base and has partnered with Plixer to bring them to market.
Get the Palo Alto Networks solution brief to learn more.


