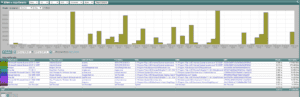
After analyzing their impressive export, Ziften ZFlow reporting support or Ziften IPFIX support is now supported by our flow collection system. Per their announcement recently at the RSA conference, Ziften joins the ranks of dozens of other vendors who are supporting IPFIX with extensions. We worked with the engineers at Ziften to become the first vendor to report on their unique exports. Check out the example below.
The above is very similar to the IPFIXify technology that we released in 2013. IPFIXify is a free and open source project for exporting IPFIX from end systems – both Windows and Linux.
Great Example of Innovation
Like IPFIXify, ZFlow is basically IPFIX with their vendor specific elements. In other words, it’s really just IPFIX. For marketing reasons, some companies like Riverbed (CascadeFlow), Citrix (AppFlow), 3Com (NetStream), Juniper (JFlow) rename NetFlow or IPFIX to emphasize that they are exporting something more unique than plain old NetFlow. This is true if they added support for enterprise specific information elements which the IPFIX standard made provisions for. Ziften’s export is awesome and goes beyond what is currently defined in the IANA standard. Details include:
- Layer 7 application and version
- application description and base file
- Internal Name and File Name
- Path of executable and CMD
- MD5 Hash
- The user name and IP address
- Operating system and machine name
- Process ID adn agent UUID
- Many other details – to much to list
We are one of the industry standard IPFIX collectors that can work with it.
About working with IPFIX
When vendors add support for IPFIX they typically first try to support the IANA standard elements. This strategy helps ensure that more vendors will support and report on their export. However, when a standard information element hasn’t been defined by IANA, the vendor will create an enterprise specific element to export something unique. In order for the collector vendor to interpret the unique enterprise information element, they will need documentation on the format. Think of this documentation as the MIB file that has to be compiled in SNMP to read enterprise specific OIDs. Some IPFIX exporters avoid the need to create documentation on how their enterprise specific elements are formatted by implementing RFC 5610. SonicWALL and Plixer are the only vendors I know of that have done this to date. It’s really too bad because the effort to support it is really minimal and it would result in a lot more vendors supporting each others export.
Ziften can identify a variety of Indicators of Compromise (IOCs) and elevated risks by correlating endpoint observation context with network observation context. Metrics or key performance indicators (KPIs) provided by their appliances include:
- Count of exposed vulnerabilities
- Individual system risk scores and population risk aggregates (taking into account the number of vulnerabilities and the severity of each vulnerability)
- Count of endpoints with security policy violations
- Count of unique, low-prevalence binaries
- Aggregate score of exposed vulnerabilities
If you have invested in a Ziften solution and you would like to report on their IPFIX export (ZFlow), reach out to our support team and we’ll have you get up and running with Ziften ZFlow Reporting Support. Don’t forget to try IPFIXify as well.