What is a security threat? A network security threat is any unwanted traffic trying to get onto your network or cause harm to it. Today I want to talk about a DNS reflection attack which is when attackers send a large number of queries from a spoofed source address to your DNS. The address which is spoofed is typically that of the victim. When the requests are received by the name server, all ensuing responses to these queries are directed back towards the spoofed IP of the victim. Recently, one of our customers detected a DNS reflection attack with our network threat detection solution and shared the following story.
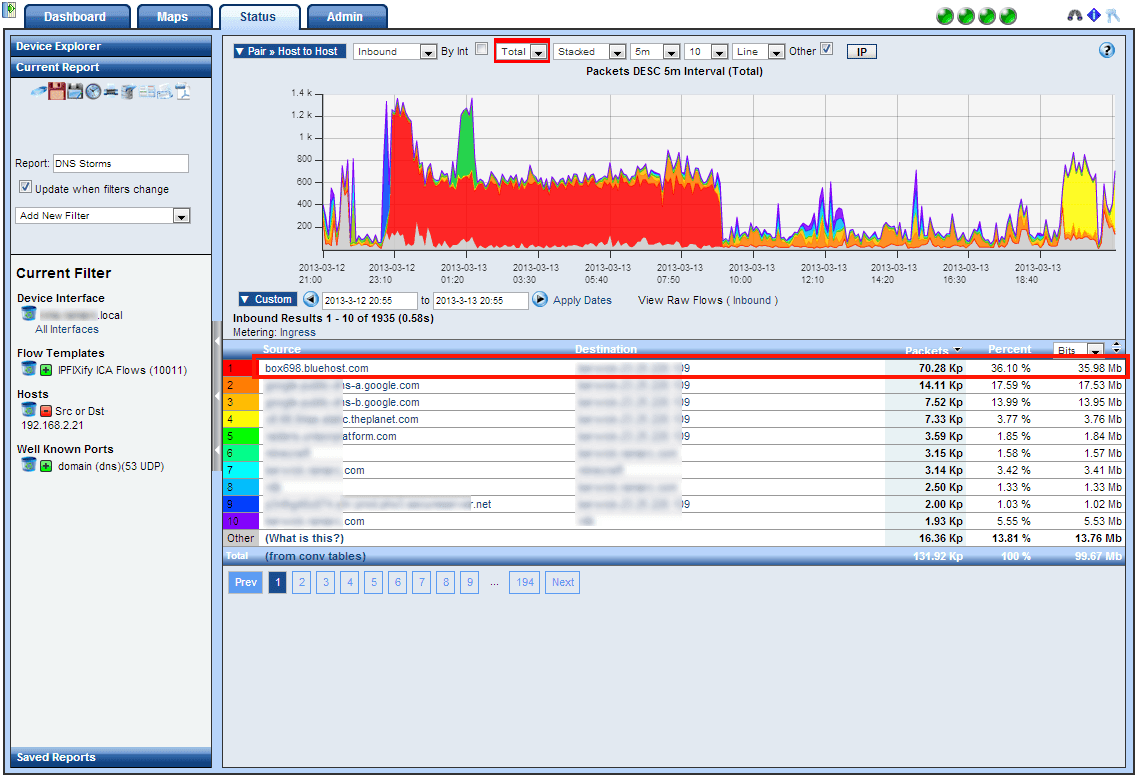
After receiving a notification about the DNS reflection attack, the customer carried out a forensic investigation to discover the traffic pattern and learned that the attack was only causing 4 – 8 flows per second from their end. The perpetrator was sending a DNS request from a spoofed host which in this case was doc.gov to the customer’s authoritative DNS server. The customer’s DNS only resolves requests for domains it is the master of. Therefore, the customer’s DNS server did what it’s supposed to do and sent a REFUSE message back to doc.gov instead of the original sender. Imagine 100s of DNS servers like the customers sending these ‘refuse’ messages. The result is that the target will get a massive flood of traffic back to doc.gov (I.e. DDoS attack). Below you can see 70.28 thousand packets were sent over almost a 10 hour period.
Not realizing the source was spoofed, the customer contacted the hosting service for doc.gov. The hosting service for doc.gov told the customer that they have seen attacks of 8GB at a time hit their network because of DNS hosts like the customers who are doing the damage for the attacker. In other words, our threat detection solution had spotted a DDoS attack the customer was participating in. The doc.gov hosting service also shared this bit of information:
“If you can restrict your DNS servers to only respond to queries for the domains that it is authoritative for, you can reduce the issues. Any other queries (for example, being used as a normal resolver) should be restricted to subnets that you need to use the resolver on.”
IT security threats like this are dangerous because the DNS is supposed to send a REFUSED message back. In the customer’s implementation of bind9 which is one of the most widely used DNS servers deployed, there is no option to not reply back. To resolve this, our customer had to do other hoop jumping and get clever by actually filtering on the hex within the server’s firewall software iptables to black hole these requests.
After further investigation into the logs, the customer discovered that these attacks have occurred on more than just to doc.gov. He found evidence of attacks on fda.gov, ripe.net, and isc.org.
Reflection Vs Amplification?
- DNS Reflection Attack : a cyberattacker leverages zombie computers in a botnet to send domain name requests to DNS servers in a way that causes DNS servers to send a flood of responses to a targeted domain.
- DNS Amplification Attack: the response to the DNS query is significantly larger than the query itself.
Many DNS DDoS attacks involve both the above strategies which is why the terms are often used interchangeably.
Don’t let DNS reflection attacks and DNS amplification attacks cause problems on your network. Our network traffic monitoring solution can be setup to monitor for DNS attacks and send notifications when a threshold is reached.