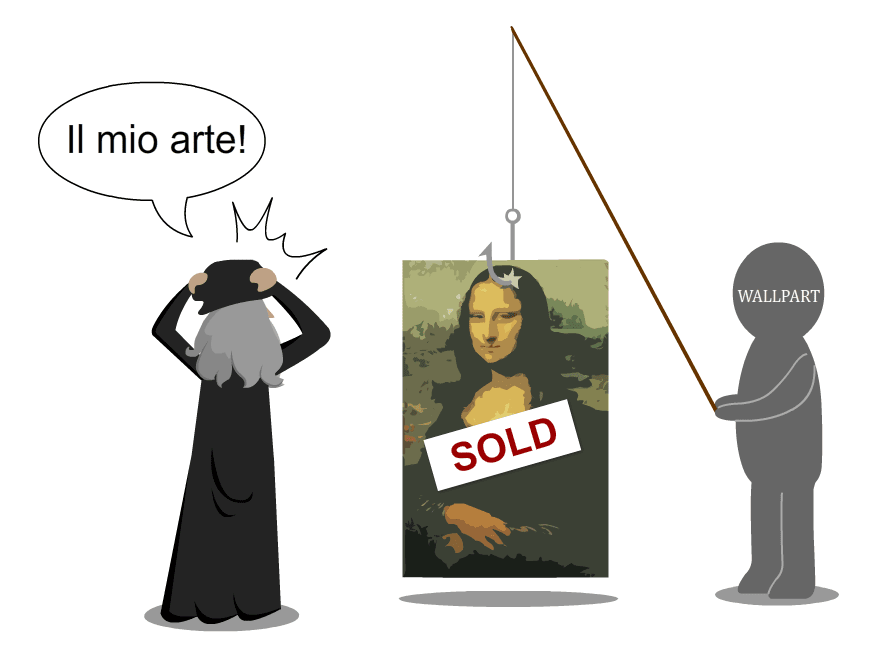
There are a lot of clever phishing scams out there. One recent scam is particularly underhanded, however, as it preys on artists’ instinct to protect their work from theft.
Warning: Do not visit Wallpart’s site–doing so may endanger your computer and/or network.
Wallpart (also referred to as Poster Shop) is a site that pretends to sell posters. It fakes a catalog by using images pulled from search engines such as Google Images. The ease with which Wallpart accomplishes this allows it to dupe artists into thinking their work is being sold without permission.
The first thing that may come to mind when you see the site is, “Hey! That’s a lot of copyright infringement!” But the devious bit is how Wallpart uses that gut reaction to pull its phishing scam. When the artist becomes aware of the alleged violation, possibly by Wallpart initiating contact, they can fill out a “Report Violation” form. The answers to the form’s questions are what they’re after, but they can get a lot more information than just what is filled out on the form.
Furthermore, visiting the site alone is dangerous; malicious code has been found embedded in various places throughout Wallpart’s website. In reaction, a couple of change.org petitions have been formed to take Wallpart down for art theft, but, unfortunately, I doubt this will work. First of all, Wallpart protects themselves by stating they don’t actually have a catalog in their “About Us” section:
We have no base of images, and doesn’t host and store the image on servers. Wallpart.com only helps the user to find the images interesting him, the site uses data of the most known third-party search engines. Process of search happens at user’s browser.
The real problem here isn’t art theft, anyway–the danger is in the phishing attempts.
Secondly, Wallpart has been caught before, but it’s slippery–it changes its hosting domains after being revealed for what it is.
Bigger than Wallpart
While Wallpart may have the biggest spotlight lately, image scraper sites like it aren’t uncommon. It’s like a hydra; take down one malicious website and two more pop up in its place. This will keep happening until the scam no longer works.
How do we get the scam to stop working? By becoming wise to the trick.
When you get an email from a company, ask yourself whether you’ve heard of that particular company before (and examine the name closely to make sure it’s not just an iteration of a well-known company’s name). If you haven’t heard of it, Google it before you visit the site. I’ve done this before and quickly found out that the email I received was a scam attempt.
Another good habit to develop is to hover over links in the email and see if they start with http or https. Typically, links that begin with https are more secure because those sites have obtained an SSL certificate. If you’d like to see what one of these looks like, click the small green lock in the address bar of this page.
It’s easy and cheap to acquire a domain-validated SSL certificate, however, so you should not rely on this method alone (DigiCert, a recognized SSL certificate provider, has a great article on why domain-validated SSL provides a low level of validation.)
If you know somebody who regularly posts artwork online, please make sure that they are aware of Wallpart and other ne’er-do-wells who seek to take advantage of them.
For more cybersecurity news, follow Plixer on Twitter.
Sources: