As companies continue to move to software defined networks (SDN) and cloud computing, the need for detailed and accurate VXLAN monitoring will continue to increase. Fortunately, there is already a technology available today to monitor the virtual environment – VXLAN’s, Virtual Distributed Switches, and Virtual Machines. If you would like to know more on what VXLAN’s are and VXLAN monitoring in the virtual environment, read on!
What is a VXLAN?
A Virtual Extensible LAN (VXLAN) is a network virtualization technology (overlay network) that attempts to improve scalability issues associated with large virtual deployments. VXLAN does this via a MAC-in-UDP encapsulation which enables the creation of virtualized Layer 2 subnets that can span physical Layer 3 IP networks (Ethernet Layer 2 Frame in IP). The encapsulation header is shown in Figure 1:
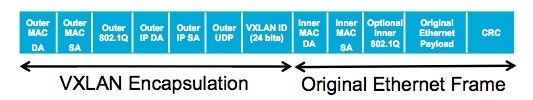
Figure 1: VXLAN Encapsulation Header [Source]
This allows for scalability in the virtual data center (VDC) where there is a need for more than 4000 logical partitions in the network. These 4000 partitions equate to the maximum number of VLANs that can be created as per the 802.1Q standard, which defines the VLAN tag as a 12-bit number. VXLAN addresses the 4000 VLAN limitation by using a 24-bit identifier called the VXLAN Network Identifier (VNID). This allows for over 16 million logical segments. This increase in the logical segments enables the connection between two or more layer 3 networks and makes it appear like they share the same Layer 2 subnet. For more information on VXLANs check out the IETF Draft: VXLAN: A Framework for Overlaying Virtualized Layer 2 Networks over Layer 3 Networks.
VXLAN Monitoring Challenges
The challenge with VXLAN monitoring is that there is a total loss of visibility of the overlay network (VXLAN) because all the traffic is UDP tunneled. Also, as stated before, the VXLAN enables two or more layer 3 networks to share the same layer 2 subnet – this makes it impossible to isolate overlay traffic from the physical network and the different overlay networks can have overlapping address segments. Most importantly, who owns the VM Environment? The Operations Teams and System Admins! This adds an “Achilles heel” for both the network traffic visibility and performance between VM Servers over VXLAN’s on VDS’s for network teams.
VXLAN Monitoring
To monitor the VXLAN, NetFlow will need to be enabled on the Virtual Distributed Switches. A great video guide on setting up VDS NetFlow can be found on YouTube: VMWare VDS NetFlow Configuration
Also, check out this blog post on VDS NetFlow Support on some of the challenges of VDS NetFlow. Figure 2 shows a general overview of the VDS and where NetFlow will be collected:
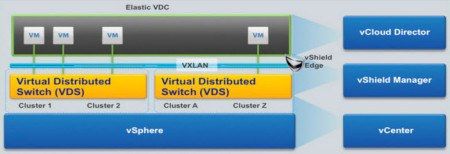
Figure 2: VMWare Overview – Overlay Network [Source]
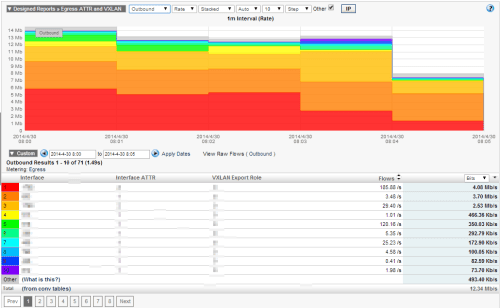
Looking at the VDS flows in a NetFlow collector, the typical version 5/9 exports/reports will be available as expected, but VMWare is also sending unique information that relates to VXLANs. Figure 3 is an example of this:
Figure 3: VXLAN Monitoring
It is now possible to gain insight into information relating to ingress/egress interface attribute, the VXLAN export role, layer 2 segment id, and the maximum time to live.
More to Come?
With the virtual data center and software defined networks, there is likely to be more exports relating to the virtual distributed switch and VXLAN monitoring. Check out this webcast on VMware ESX Traffic Monitoring and Threat Detection for more info VMWare ESX monitoring. If you have any questions, feel free to comment below or reach out to the Plixer Support Team at 207-324-8805 x4