Verizon recently released the 2016 Verizon Data Breach Investigations Report. The Verizon Data Breach Investigations Report (DBIR) is an annual publication that provides an analysis of information security incidents, focusing on data breaches. As an active member in the security community I look forward to this report annually. While reading this year’s release, I discovered a hidden message!
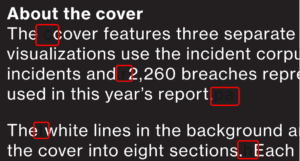
On the last page, which is dedicated to explaining the cover, I noticed that there was some strange spacing in the text. After closer examination, I realized there were characters in the text with the same font color as the page background.
I took a few minutes to locate and decode the hidden message. The text spells out a domain:
cyber.pathogen.ai
What is cyber.pathogen.ai?
This looks to be a satirical website based on a statement made by Michael Ramos, the San Bernardino County district attorney. The site references an Ars Technica article, which links to a court document filed by the district attorney in which it is stated “[t]he seized iPhone may contain evidence that can only be found on the seized phone that it was used as a weapon to introduce a lying dormant cyber pathogen…”. IPew Cyber Pathogen AI Conquest Status is a real time pewpew map indicating worldwide infections of fictitious cyber pathogens similar to Norse Corp’s Attack Map.
Some of the worldwide infections taking place include: Type 1 Cross-Site Diabetes, conflu, Trojan.Coli-E, and Type 2 Bipolar Coding Disorder. These infections are spread with a number of different attacks including, but not limited to: Conficker, Sharknado, Ping of DOOM, and Heartbleed Hotel.
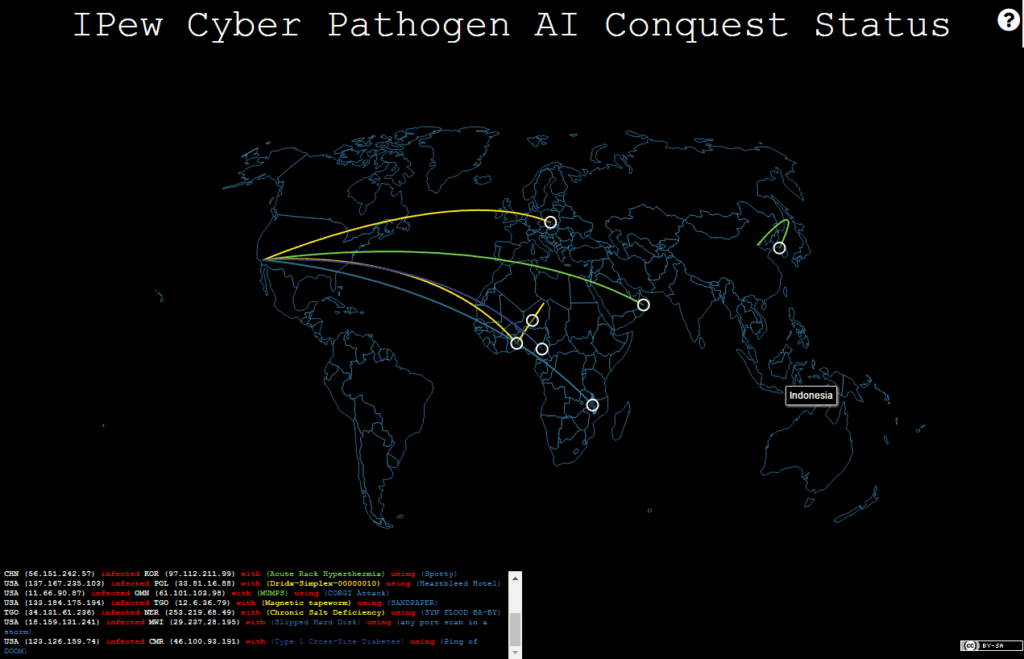
Sample of pathogen infections
SA (41.29.175.171) infected WLF (141.214.234.188) with (conflu) using (Sharknado) WLF (49.152.40.166) infected VUT (235.165.151.54) with (Acute Rack Hyperthermia) using (Ping of DOOM) USA (200.169.55.148) infected COM (84.108.198.123) with (Infinite Monkeypox) using (SNAILshock) USA (162.247.247.18) infected USA (87.27.51.181) with (threatbutt) using (Ping of DOOM) USA (156.92.173.245) infected JAM (223.96.51.20) with (Metasploit-ressitent Security Architecture) using (Po_ODLE) JAM (51.178.238.249) infected USA (30.156.209.88) with (Metasploit-ressitent Security Architecture) using (Goldfinger) USA (13.200.3.119) infected MEX (78.221.111.185) with (Rapid Organ Failure) using (Driduplex) MEX (192.188.103.15) infected USA (172.234.213.74) with (Trojan.Coli-E) using (Heartbleed Hotel) USA (156.13.183.243) infected GBR (141.100.68.4) with (influendianza) using (any port scan in a storm) USA (125.212.177.124) infected ALB (248.65.209.36) with (Type 2 Bipolar Coding Disorder) using (Driduplex) USA (93.211.232.43) infected DOM (13.209.125.121) with (infectious Boring Monotony) using (Po_ODLE) DOM (239.198.103.105) infected HTI (3.223.109.74) with (Mono) using (SANDPAPER) HTI (233.140.92.44) infected DEU (59.128.195.246) with (Metasploit-ressitent Security Architecture) using (CORGI Attack) HTI (165.92.63.76) infected CUB (30.71.126.177) with (Ruby) using (Heartbleed Hotel) HTI (110.54.124.109) infected CHL (221.245.91.93) with (Slipped Hard Disk) using (any port scan in a storm) DEU (87.215.82.124) infected TUR (198.99.81.212) with (MUMPS) using (Conficker) TUR (138.129.43.164) infected POL (17.151.166.227) with (Ruby) using (any port scan in a storm) POL (162.217.221.241) infected UKR (215.216.63.59) with (Ruby) using (Thought Leader Tweet) POL (104.187.6.92) infected UKR (112.23.0.241) with (Metasploit-ressitent Security Architecture) using (any port scan in a storm) POL (114.134.220.188) infected GBR (49.65.53.195) with (conflu) using (SANDPAPER) GBR (168.234.221.54) infected ZAF (38.138.237.122) with (MUMPS) using (Spaghetti RAT) GBR (133.71.96.152) infected DEU (47.11.91.199) with (Mono) using (Po_ODLE) DEU (233.29.25.240) infected ITA (143.189.223.199) with (Acute Rack Hyperthermia) using (Goldfinger) DEU (226.38.29.196) infected CZE (144.250.52.232) with (Magnetic tapeworm) using (SNAILshock) DEU (210.63.130.35) infected CHN (164.81.112.75) with (Infinite Monkeypox) using (Po_ODLE) USA (3.68.246.42) infected ATG (237.14.170.104) with (Infinite Monkeypox) using (any port scan in a storm) USA (20.51.60.196) infected SLV (115.51.4.189) with (Type 1 Cross-Site Diabetes) using (Ping of DOOM) SLV (65.195.139.233) infected USA (155.138.113.55) with (Acute Rack Hyperthermia) using (Conficker)
So, what conclusions could one draw from the DBIR using an old SEO Evasion Technique to hide a message for its readers? A number of possibilities come to mind.
Given the wave of social media postings, many of which mocked the DA’s use of the non-technical term “cyber pathogen” to describe the supposed malware, is Verizon following suit? Does this suggest that Verizon is taking a stand with Apple against the district attorney’s office? While there is no definitive answer, the data suggests this as a possibility. UPDATE: 4:37 PM. I have learned that this is part of a DBIR Cover Challenge and does not reflect any political views of Verizon.
Are there other messages hidden in the DBIR just waiting to be found? UPDATE: 4:37 PM – Yes, there are!