Users are the weakest link. How many times have you heard that? Better question, how many times have you said it yourself? We can deploy the most sophisticated technology, write the best policies, and it will all fall apart with a single click on a bad link. We’ve talked about it here, too—even I’ve written about how easily users succumb to social engineering attacks. But blaming users is just the easy thing to do. Introspection will go farther in solving the big problems.
Feudal security
Renowned security technologist Bruce Schneier discusses what he calls “feudal security.” In essence, he means that the power of the internet has become consolidated around few groups.
On the corporate side, for example, we have vendor-managed devices and large data aggregators. We no longer have control of our own data; it’s all on servers owned by Google, Apple, Microsoft, Facebook, and so on. We no longer have control of our computing devices, either, as we increasingly access our data using devices that offer less user control, such as iPhones and Kindles.
Governments make up another group, and in many cases corporate and government interests align. The repeal of net neutrality is the most notorious recent example.
But opposing them is a third group: the marginal, dissident, or criminal. Schneier likens them to Robin Hood, whereas the large institutions above are the Sheriff of Nottingham. This is less in the sense of good vs. evil and more in the sense of nimble vs. strong. As technology evolves, the Robin Hood group adopts it first and gains the upper hand. The Sheriff group, while slower, has more power to magnify with that technology when it finally does so.
But what happens to everyone else—the majority, the users?
Those with relatively low technical ability get caught in the middle. This is where the analogy comes in: when feudal lords fight, peasants get trampled. When a criminal breaches large organization—Sony, Yahoo!, Equifax—the organization is large enough to ultimately remain standing while users’ PII is in who-knows-whose hands. Yet we blame the ones who suffer most?
What’s more, we keep the harm at arm’s length. It’s all vague terms and statistics. We avoid talking in second person like we’re afraid to be personal. I don’t want to hear just that some percentage of users experience phishing attacks every year. Show me that you care about William and Nancy, who lost their life savings to one.
Claiming users are the weakest link lacks empathy
It’s hard to remember that we were once ignorant. As we accumulate knowledge, we forget that that knowledge isn’t common sense. We’re not smarter than anyone else; we’ve just focused on different fields. To say that users are the weakest link demonstrates that you’ve forgotten this.
As a result, we’re too focused on the fancy things like targeted attacks, which make up a tiny fraction of unwelcome cyberactivity, and not the majority of what actually harms users.
Facebook CSO Alex Stamos gave a keynote on the subject at Black Hat 2017. He showed these two images:
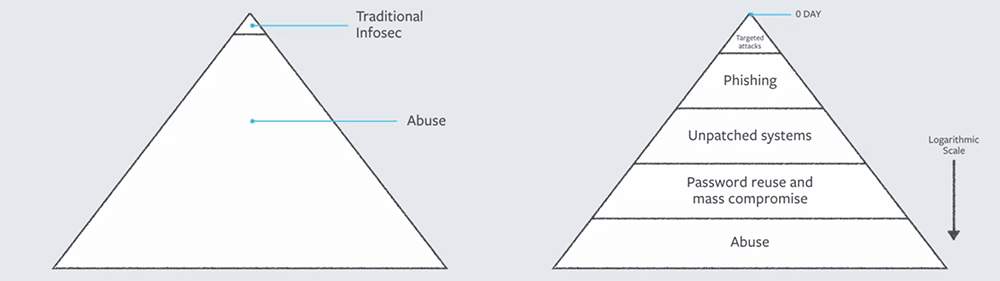
Stamos posits that we spend too much time at the top of the pyramid. The huge area labelled “Abuse” represents harm caused by using systems in technically correct ways, such as spamming, doxing, DDoSing, and “vulnerabilities” caused by simple, straightforward problems like re-used passwords, unpatched systems, and phishing. There’s little there that’s so dramatic as the iconic hoodied hacker or organized nation-state team using 0-day exploits.
He goes on to say that we “have a real problem with empathy.” Using Facebook as an example, he talks about their users who buy a phone for $50-100. They receive that phone from the factory with vulnerabilities that may already be years old. “We can’t just write off these people,” he says. “We can’t say they’re not worth protecting.”
Take a more empathetic approach
A few years ago, I freelanced in a creative field. Not only is it common to have different ideas from your clients, it’s an absolute given. But you still have to help your clients succeed under the constraints they give you. If you don’t, you’re out of a job and the client doesn’t get a good solution to their problem. It’s a loss for everyone.
This is not dissimilar to the dynamic between an IT professional and their users. The stakes, however, are much higher. Why don’t we consider it a part of our job to work within our users’ constraints, whether that means a lack of technical skill, a desire for better usability, or a need for a more security-focused culture?
When a user makes a misstep, let’s stop groaning and work with them. Saying that users are the weakest link doesn’t solve anything. Let’s think about what we could have done instead of shunting the blame.
As a start, check out my colleague Mikel’s blog on how to write an acceptable use policy and actually get your users familiar with it.


