Username NetFlow Reporting is a hot topic since the Cisco Visual Networking Index (VNI) report in late May. By 2016, Cisco’s forecast predicts that there will be “nearly three networked devices per capita”. Firewall vendors like Dell-SonicWALL and Palo Alto are also paying attention. Network admins are asking “Who is authenticating all of these devices onto the network?”
With only an IP Address, tracking down who or what that address belongs to can be a cumbersome and tedious process. When DHCP and NAT are changing IP addresses on a fairly regular basis, how can we find out the history of an IP Address? Where do we start?
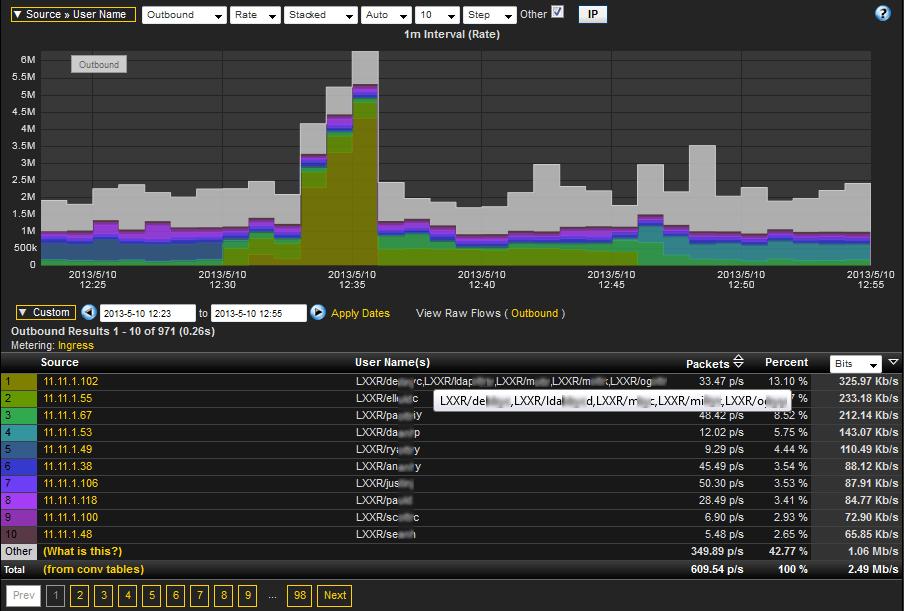
NetFlow Reporting
NetFlow reporting is the best way to track IP traffic on the network. Some routers and switches export the MAC address with each flow enabling admins to observe when the MAC address changed for an IP address. The vendor ID portion of the MAC address (i.e. the first 3 bytes) can be helpful when trying to determine the type of device (e.g. Blackberry, iPhone, HTC, etc.) but, we still don’t know who the end user was that authenticated the device onto the network.
Identity Aware NetFlow
Tying the user name to the flows created by a host makes tracking down a culprit much faster. It seems like a no brainer, but this strategy has its faults as well. Remember, IP addresses can change. This begs the question: What is the best way to see which other laptops, smart phones, tablets, printers, etc., have made use of the same IP addresses? To make matters worse, perhaps the computer is located in a conference room where any number of employees could be remotely or locally authenticating for daily meetings. We need to create identity aware NetFlow.
These are just some of the reasons why username NetFlow reporting should be a major concern for anyone interested in network traffic monitoring solutions. Having access to NetFlow and username in the flow reports increases contextual awareness, and can even help reduce mean time to know and mean time to resolution. Greater situational awareness is one of the primary goals in today’s network security solutions.
Vendors Exporting Username in NetFlow/IPFIX
Vendors exporting username in their NetFlow export include:
- Cisco Systems
- Dell SonicWALL
- Palo Alto Networks
The above vendors have been first to step forward with user name details in their exports, but there is a problem. The user name is only associated with the traffic passing through their firewall. What about internal traffic that doesn’t utilize the Internet? Often times, internal routers don’t export user name in the flows they export.
Plixer, however, can leverage the user name details from one flow export and apply them to another. In fact, our NetFlow collector can grab the username activity log from any authentication system and correlate it with any flow export.
Very likely, one of the best ways to obtain username information is by leveraging logs from a network authentication system like Cisco ISE or the Microsoft domain server. Both maintain logs about the users authenticating onto the network, including where and when they gained access:
As you can see in the above example, Username NetFlow Reporting allows administrators to determine who authenticated the IP address onto the network at the time of the incident. We can then trend the most (or least) active users in a given time-frame. Notice how multiple users are listed as having authenticated onto the network, from the same IP address, for the time-frame selected in the first entry. This might be worth investigating; Network Behavior Analysis or baselines cannot always be relied upon to catch all odd patterns like this one. Think of NetFlow with username as another layer of security.
Username is especially necessary when performing Network Security Forensics, because when combined with NetFlow Reporting it allows us to narrow in on all the devices the username has authenticated onto the network. The helpdesk can then pick up the phone, call the user and ask if they intended to authenticate the device in question. Imagine for a moment what could happen if a malicious user obtained credentials with network-wide permissions – Since their access to a remote site on the WAN will appear legitimate, it may go unnoticed until it’s too late.
With the number of devices growing 3 times between 2012 and 2016, using network behavior analysis tools to pin down a specific employee’s traffic, is going to require an enhancement to this technology. Username NetFlow Reporting is the addition needed to better manage the influx of more addresses.
Jan 22, 2015 UPDATE with more technical details on username reporting with NetFlow (IPFIX).