In the past month I have been on a couple support calls where Locky ransomware came up. Locky sounded familiar but wasn’t a topic I had yet tackled with any customers. So I took to Google and what I found was surprising. Pages of recent articles surrounded this new ransomware. Except Locky isn’t really new at all. It was introduced back in February of 2016, which is why it sounded so familiar to me.
What is Locky?
Locky hadn’t been too successful in the past, which is presumably why it left the scene not too long after its first introduction. This year Locky is back and like most ransomware, it enters your network through an email attachment.
Despite constant warnings regarding phishing campaigns, the success rate of fake messages has increased 1300% since Jan 2015. It’s not entirely our fault; hackers have begun to use social engineering to attack individuals like the busy accountant, navigating through multiple invoices a day.
In fact that appears to be Locky’s preferred method. Notice the proof of payment in the attachment below.
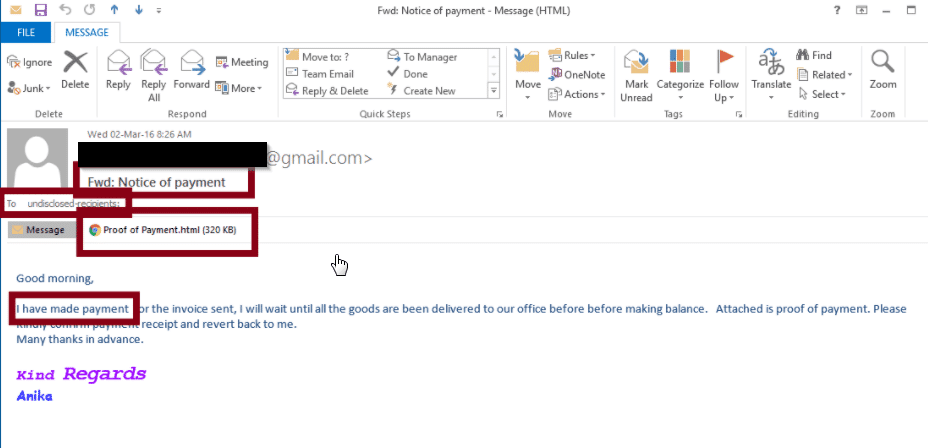
How does it work?
Let’s say we were a bit too eager and decided to download the attachments. It’s still not too late. Locky will download the attachment and request that you enable macros if the data decoding is incorrect.
Do not enable macros.
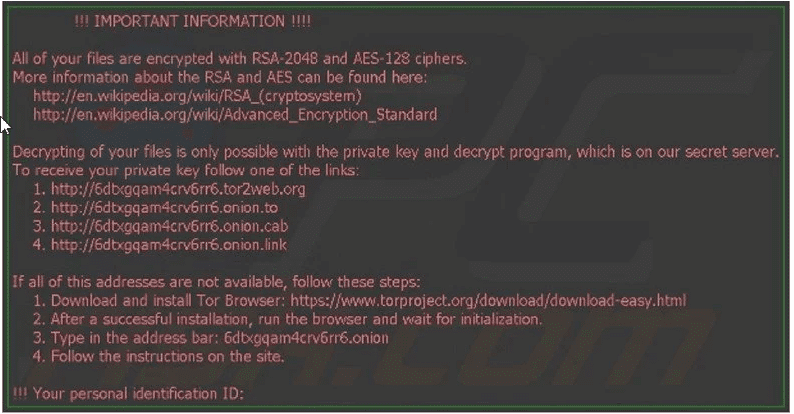
By choosing to enable macros, you are allowing Locky to run the code that it’s saved within the document. This code is designed to save a file to the disk and run it, pulling down the malware. At this point, all your files will be renamed with the new file extension “.locky” and the warning message below will appear. Much like Petya, Locky will insist on a payment in the form of Bitcoin.
Now that we understand how Locky gets into our network, let’s take a look at how we can reduce risk of spreading by monitoring our network.
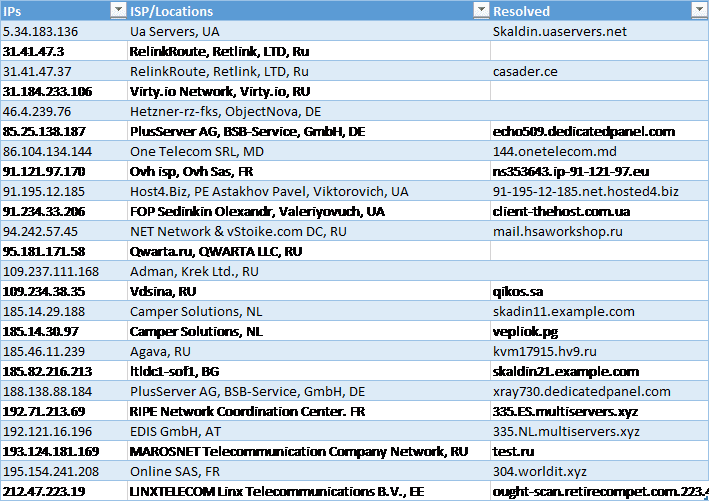
The first step is just good housekeeping, staying on top of new security threats, and doing your research. That’s where I started; below is the list I created based on what I know. It is important to note that these are only the most recent IPs and locations, and you should take time to regularly add to them. It is also worth noting that Locky uses common ports like port 80 and 53, so it won’t be beneficial to filter on those alone.
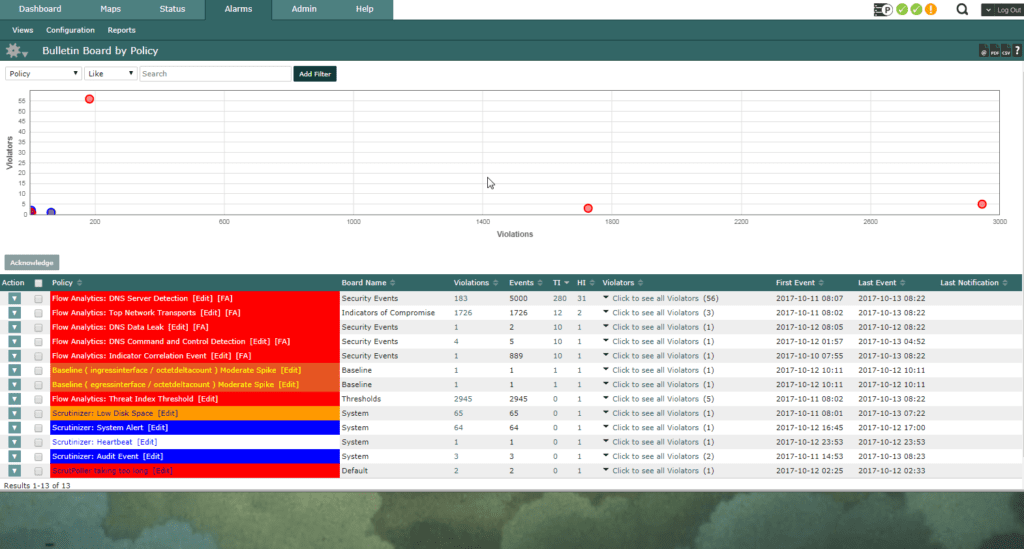
Next we can utilize Scrutinizer’s behavioral analytics to assist us in zero day threat detection and alert on suspicious traffic. Behavioral analytics is a set of algorithms Scrutinizer uses to alert you to anomalies on your network, as well as common threat behavior.
In the alarms tab, we can view any broken policies behavioral analytics has reported on. From the alarms, we can jump into any of these reports directly from the alert, but for Locky I wanted to go a bit further.
How can I reduce risk?
From within Scrutinizer I generated a default report and changed my device filter to include all devices. I continued to filter on the known IPs associated with Locky and changed the report type to pair conversations. I wanted more granularity still, so I changed my interval to 1m data as well as changing from rate to total.
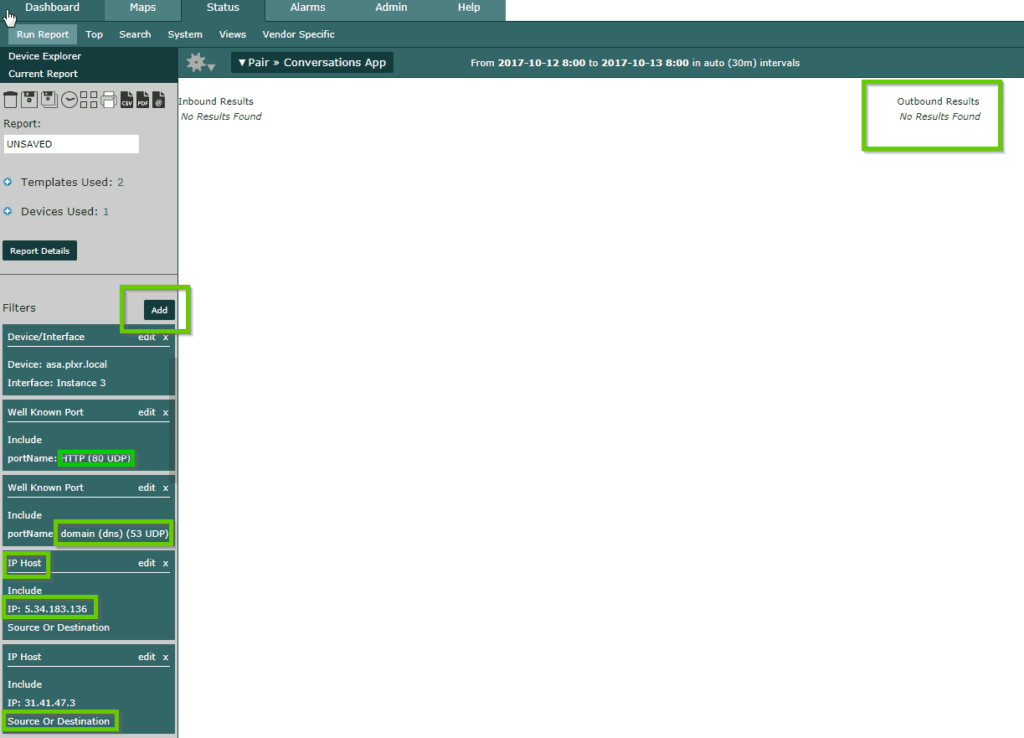
The fact that this report came back empty is a good thing. I don’t want to see locky on my network.
Using this report, I will be able to see when Locky entered my network, who allowed it, and who else on the network it is continuing to communicate with. But again I wanted more.
I wanted to be notified the second Locky dared to show its face on my network. So I saved the report, named it Locky and got to work setting thresholds.
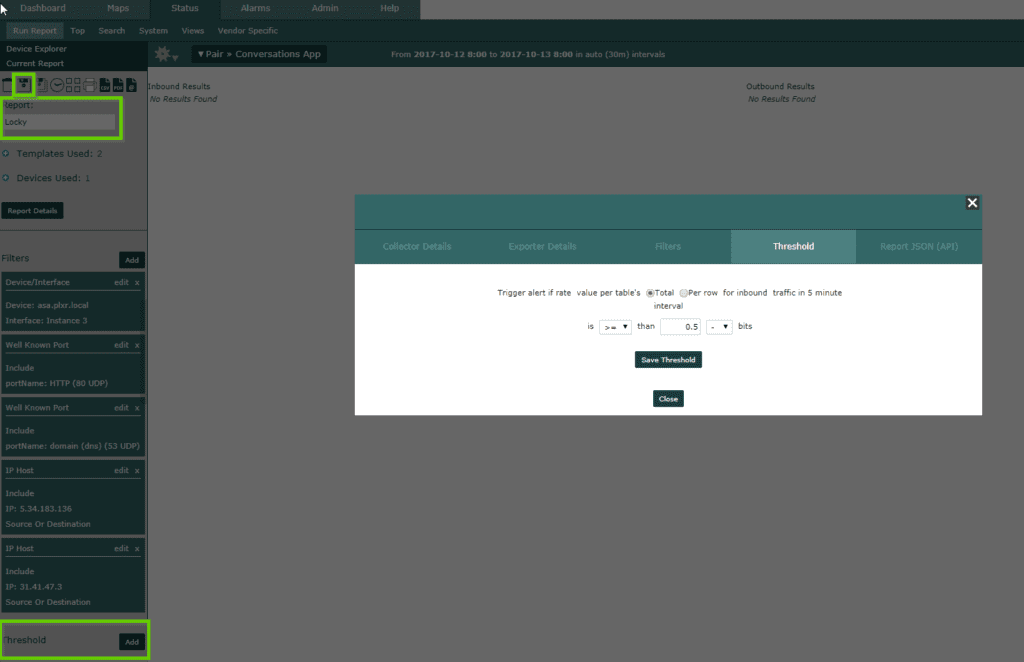
I created a threshold with the report that would not only alarm at the sight of Locky but also email the graph and table directly to me. I did this so that I would have the ability to quickly respond, and pull the infected device off the network before it has a chance to spread.
Behavioral analytics can help you track many of today’s biggest threats. To learn more, check out our blog on reducing risk against another prominent threat, WannaCry.



