The Digital Millennium Copyright Act (DMCA) was passed on October 12, 1998 as a means to mitigate the effect torrent use was having on the music and film industries. In my opinion, the most famous use of this act was in the year 2000 when A&M Recordings, along with others, used this act to file suit against the most popular media-sharing platform at the time: Napster. This lawsuit bankrupted Napster, who sold most of its remaining assets and closed its doors in 2002.

What does a DMCA notification look like?
A DMCA notification icontains plenty of legal jargon along with evidence that is associated with the claim.
This evidence typically contains:
- Protocol used to download the copyrighted materials (e.g. BitTorrent)
- What was stolen (e.g. Fate of the Furious)
- File size
- Infringer’s IP address
- Infringer’s Port
- Timestamp of when material was stolen.
How does DMCA affect service providers?
A portion of DMCA protects service providers against copyright infringement liability, given they can block their users’ access to illicit downloads as well as provide the identity of the end user should a subpoena be issued.
This protection is great, and next-generation firewalls like Palo Alto Networks and Cisco ASA with FirePOWER do their best to shut down protocols like BitTorrent at the application layer.
But when somethings gets through, forensic investigation into network data is the next step. Crawling through firewall logs can be time-consuming, and IT professionals are busy—very busy. Turns out NetFlow data provides everything we will need to perform a quick investigation so we can get on with our lives and focus on priority projects.
How does flow data help?
First things first—it is critical that your flow collection system be capable of storing 100% of the data sent to it. Keeping track of flow sequence numbers is imperative to ensure data integrity, and customizable data retention is a must-have feature to ensure the system coincides with your incident response plan.
Traditional flow data includes source and destination IP, source and destination port, timestamp, and traffic volume. This will give us everything we need to investigate the violation.
What happens if our violator is hiding behind NAT?
Luckily for us, Palo Alto and Cisco provide NAT translations within their flow exports and a sophisticated flow collection system like Scrutinizer will be able to decode these elements to provide the needed report.
Carrier Grade NAT and High Speed Logging have been increasing in popularity due to IPv4 address exhaustion. These translations are also exported in flow data and can be used to track down the offender.
Using Scrutinizer to investigate!
In the below screen capture you can see I have applied a filter for the IP address from the DMCA notification along with the BitTorrent application.
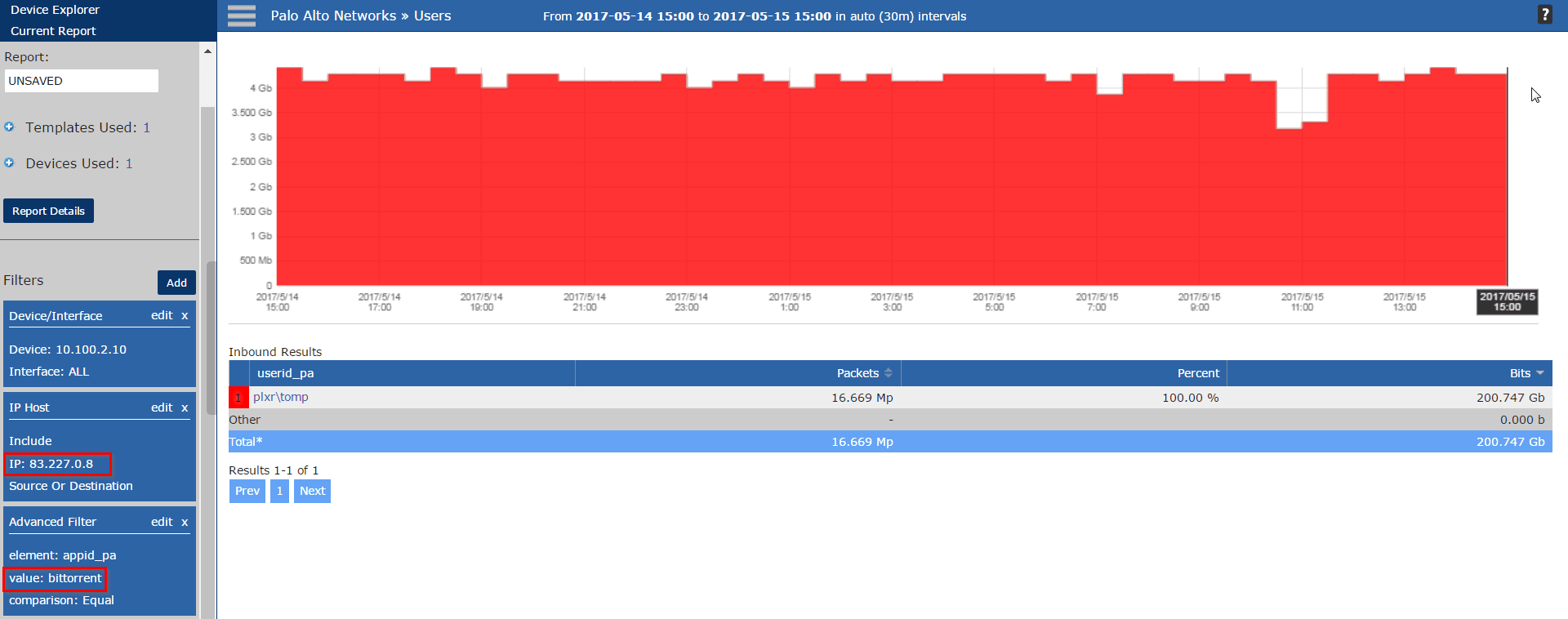
If the devices I’m collecting flows from do not export layer 7 application ID, then I can use the ephemeral port from the DMCA notification to get the same result.
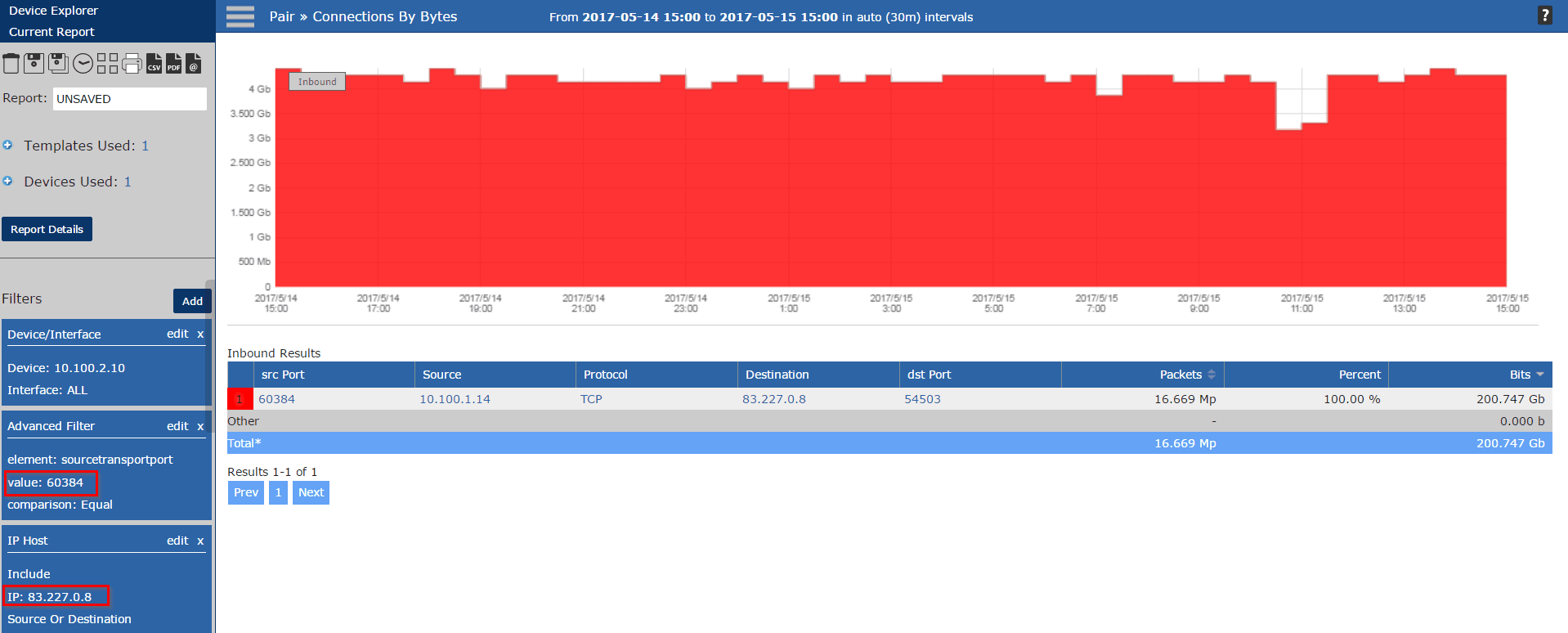
Either of these options provide a quick result when investigating one of these violations!
Contact Plixer with Questions!
If root cause analysis or forensics investigations with flow data is something you are interested in, please don’t hesitate to contact our support team with questions! There are many more ways to track user activity, like integration with Cisco ISE, ForeScout CounterACT, or Microsoft Active Directory. We are passionate about NetFlow / IPFIX and always happy to help in an investigation!



