
Understanding Supply Chain Attacks: Methods, Risks, and Defenses
Supply chain attacks have become a greater risk as businesses grow more interconnected. Rather than directly targeting an organization, attackers gain access by exploiting...

Supply chain attacks have become a greater risk as businesses grow more interconnected. Rather than directly targeting an organization, attackers gain access by exploiting...
As we navigate through 2024, the cybersecurity landscape is increasingly dominated by stealth and sophistication. The recent CrowdStrike Global Threat Report highlights a dramatic...
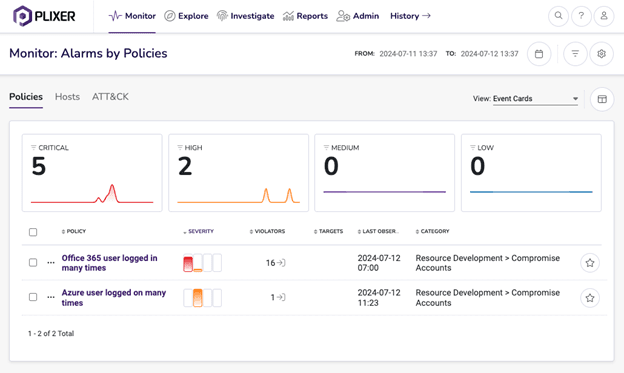
User and Entity Behavior Analytics (UEBA) provides the critical insights needed to identify these hidden dangers by monitoring behavioral patterns across users and entities,...

I think I can safely assume that everyone knows the cautionary tale of the boy who cried wolf. If you don’t, the moral is...

We’ve all had days when we think to ourselves, “Man, I wish I could just work from home in my PJs.” Recently, as companies...

Single sign-on (SSO) is a way to secure users while reducing the number of passwords they need to remember. SSO has been a highly...

If this ever changin’ world in which we live in makes you give in and cry say I’m only one guy...

Phishing attempts have been showing up a lot in the news lately and scammers are getting smarter. What can we do? What shouldn’t we...

A large-scale DNS hijacking campaign called ‘Sea Turtle’ has been spreading across more than 13 countries. With our FlowPro Defender, you can monitor your...

Local authentication into software or even hardware is useful for both the end user and the organization as a whole. Logging in with your...