In this blog, I want to talk to you about investigating zero-day attacks. A zero-day attack can be a huge menace on the network, since it can bypass a lot of your detection systems that currently have in place. It can also go unnoticed on the network for a very long time.
NetFlow/IPFIX threat detection:
Using NetFlow/IPFIX and a behavioral analysis detection system, our incident response system will alert you at the point when the traffic becomes something anomalous. One of the biggest misconceptions in network security seems to be that there is a “silver bullet” solution, when in all actuality it usually boils down to a layered security approach. Using NetFlow/IPFIX plus behavior analysis is just another layer to help improve your security plan.
Behavioral Analysis using NetFlow:
Some of our NetFlow collector’s algorithms will include looking for odd DNS traffic patterns (think ransomware), and ports/protocols that have never been in use before. Think of a sales PC on your network that has never used SSH or FTP. Suddenly you start seeing a slow leak of data over FTP going to a “suspicious” country. That may be something you’d want to be alerted on, right?
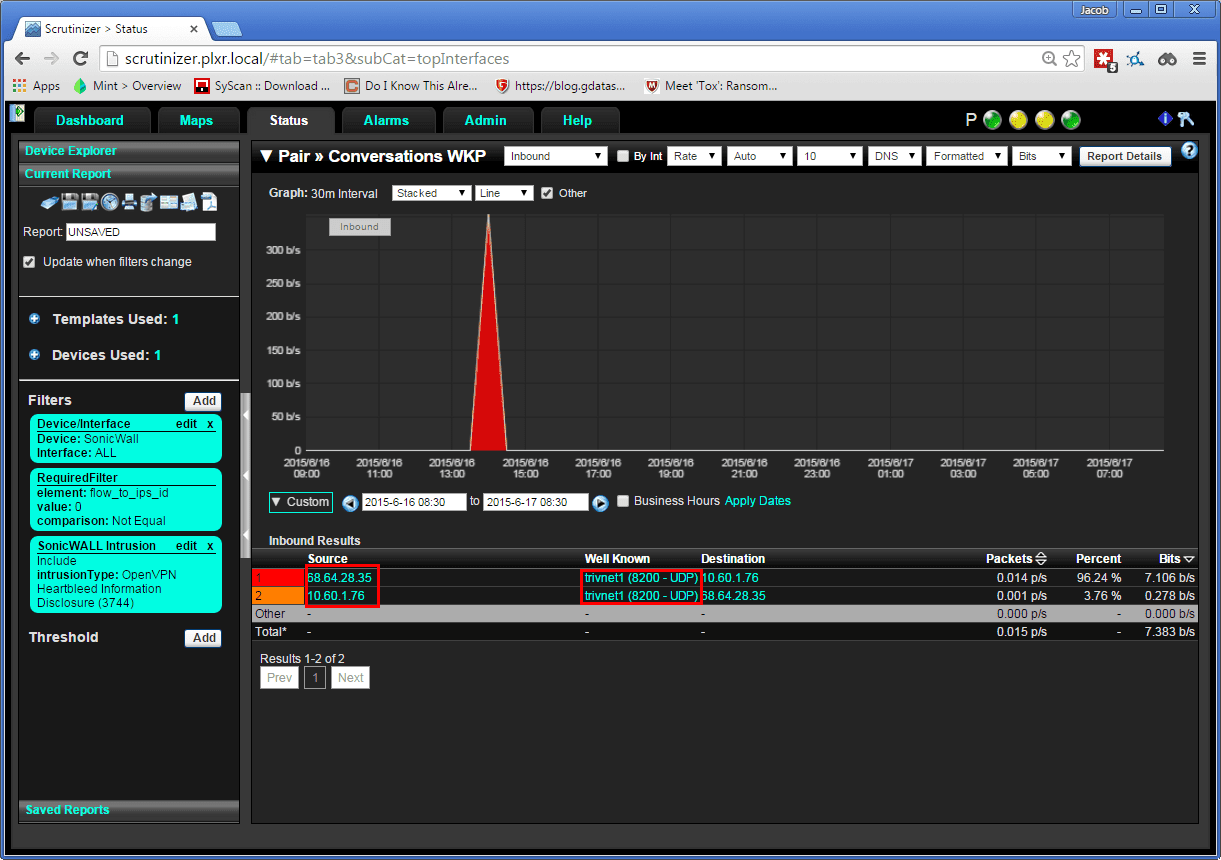
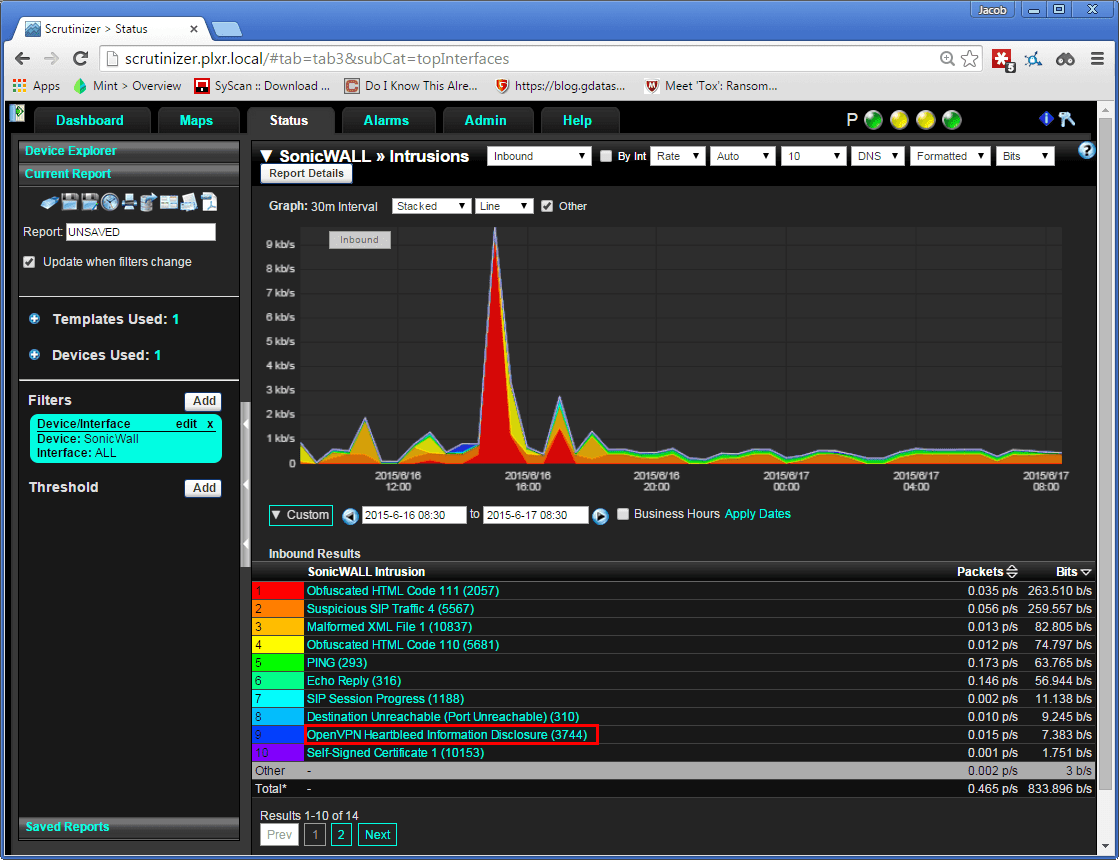
I recently worked with a customer who was having issues with a PC infected with malware. It was sending large amounts of SMTP traffic. Using a simple filter to search for outbound SMTP (not from their email server), we were quickly able to drill down and find the infected host and set up a proactive threshold in the event that this ever happened again. Doing this without the use of NetFlow is often cumbersome and requires the help of multiple parties to find/remediate the situation. Using NetFlow we were able to do this all in one step, and in under 10 minutes. Think back to the last time you had to investigate malware, how long did it take you?
What’s next in IPFIX threat detection?
With new pieces of malware coming out every single day, it’s a hard battle to fight. A layered security approach will always be your best bet in makingsure your defense is adequate. However, don’t forget about the end user. It is always beneficial to the company as a whole to do regular training to make sure end users are aware of new threats and how to avoid them.
“Making the SANS top 20 list for the first time also was human error, which was often exploited in highly targeted spear-phishing attacks. Adding to this problem is the issue of excessive user rights and the prevalence of unauthorized devices on enterprise networks, the SANS report said.” – Blog on Zero Day attacks
Good luck on the never ending battle of malware detection and fighting your zero-day attacks. If you need any help from our team, feel free to reach out to us!




