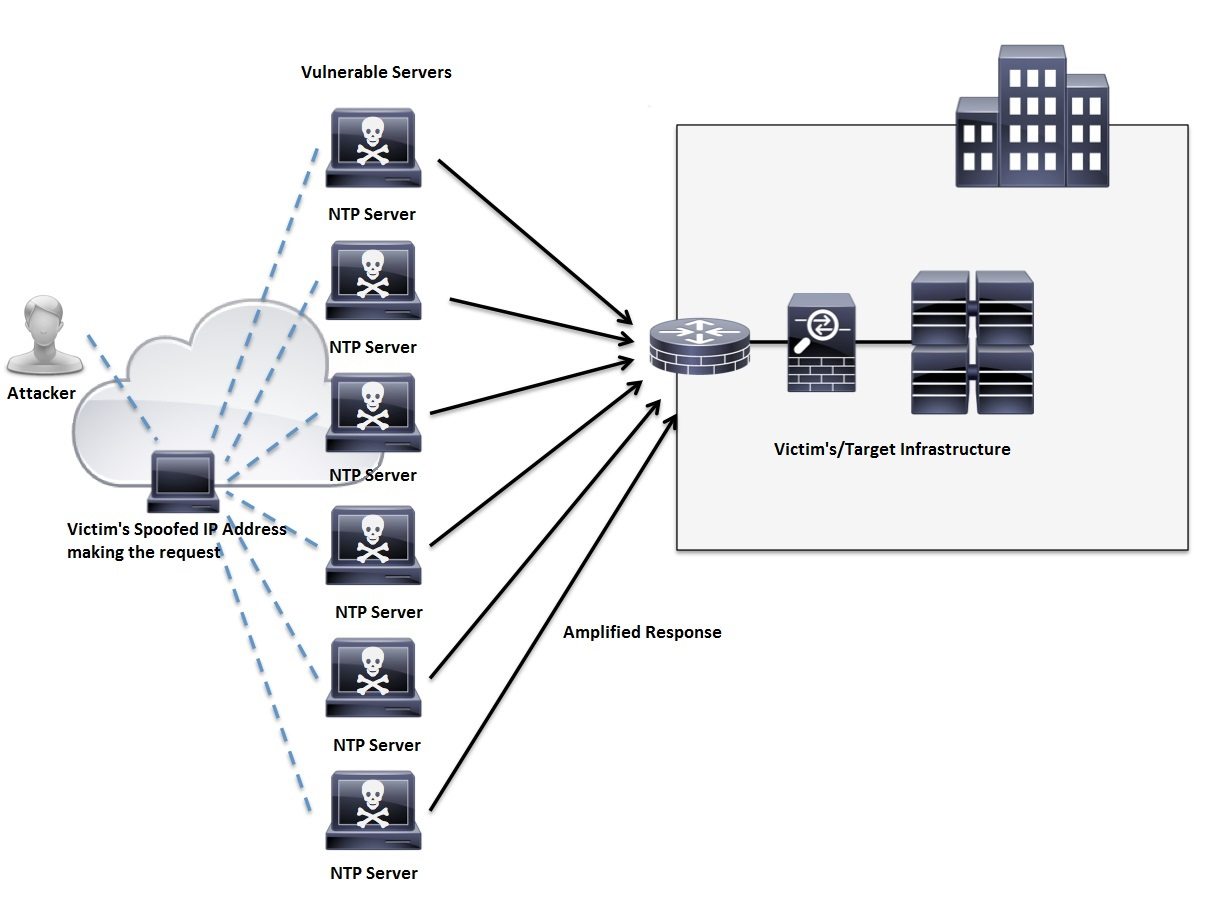
Network Time Protocol Distributed Reflective Denial of Service (NTP DDoS) is an Amplification Attack that relies on the use of publicly accessible NTP servers to overwhelm a target system with UDP traffic. The Network Time Protocol (NTP), typically UDP Port 123, is one of the oldest networking protocols and is used for clock synchronization between computer systems.
What makes the NTP DDoS Vulnerability so effective and appealing from the attackers’ perspective is how quickly the amplification scales. A command sent with an initial request over NTP may contain a small amount of traffic, but the response maybe hundreds of times larger. There are a couple of ways to create the amplification with NTP, but the most common has been the ‘monlist’ feature. This command causes a list of the last 600 IP addresses which connected to the NTP server to be sent to the requesting system. This is where the “Reflective” in NTP DDoS comes into play. The source supposedly requesting this list of IP Addresses is spoofed to the attackers intended target. This is illustrated in the following figure:
Source: A Cisco Guide to Defending Against Distributed Denial of Service Attacks
NetFlow DDoS Detection
The quickest and most cost effective way to understand what is taking up all the traffic on the network, device, or link at any given time is NetFlow/IPFIX. NetFlow security monitoring provides a means for network administrators to monitor flow traffic, as well as changes in the traffic based not on signatures but on traffic patterns. This is key when looking at NTP DDoS/UDP Reflection attacks because NTP traffic is expected on the network, just not at the volumes that are occurring during these attacks.
The United States Computer Emergency Readiness Team (CERT) recommended solution for Detecting UDP-based Amplification Attacks is as follows:
“Detection of DRDoS attacks is not easy, due to their use of large, trusted servers that provide UDP services. As a victim, traditional DoS mitigation techniques may apply. As a network operator of one of these exploitable services, look for abnormally large responses to a particular IP address. This may indicate that an attacker is using your service to conduct a DRDoS attack.”
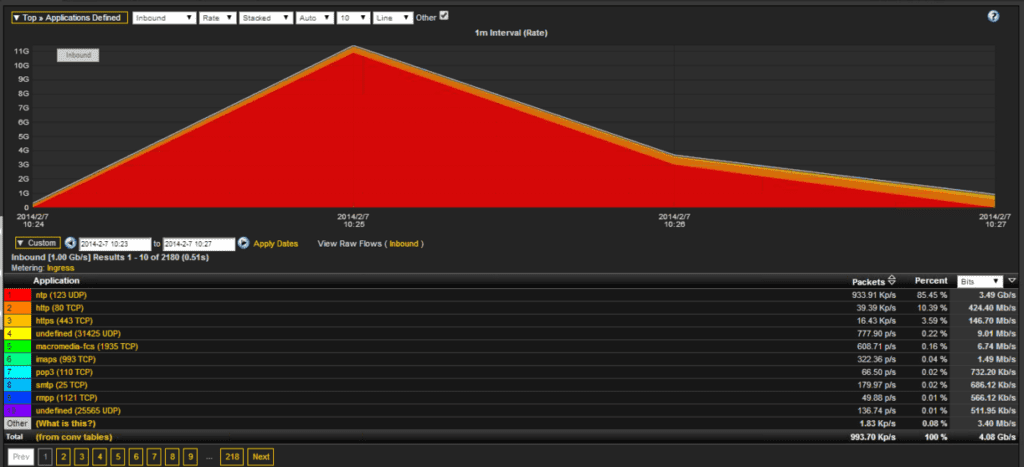
The challenge with what CERT recommends is the IP with a large amount of responses will generally not show up in the TopN in a DDoS attack because the traffic is thousands of small conversations. In the following example/screenshot, the destination host of this 10Gbps NTP traffic did not show up in the TopN as a paired conversation; however, when summarized on the application UDP 123 it became number one.
NetFlow Security Monitoring
Are you currently using NetFlow to monitor NTP DDoS or other similar UDP attacks? How are you verifying the changes made to your NTP servers will prevent a NTP DDoS attack? Check out this webcast for more information on using NetFlow to Detect and Isolate Network Problems. If you have any questions on NetFlow security monitoring, please comment below or call the support line at 207-324-8805 x4.