 There are several network visibility solutions nowadays; however, NetFlow based network management tools give you an unprecedented level of visibility into network traffic. NetFlow helps IT professionals understand who, what, when, where and how traffic is flowing. An advanced NetFlow application should not only be about deciphering IP flow data for analysis, but should also have proactive network security capability such that it can detect threats and intrusion patterns in your traffic. In this blog I would like to discuss some of the things IP flow technology has to offer pertaining to Network visibility, and I will also touch on how a NetFlow application can assist you in proactive network security.
There are several network visibility solutions nowadays; however, NetFlow based network management tools give you an unprecedented level of visibility into network traffic. NetFlow helps IT professionals understand who, what, when, where and how traffic is flowing. An advanced NetFlow application should not only be about deciphering IP flow data for analysis, but should also have proactive network security capability such that it can detect threats and intrusion patterns in your traffic. In this blog I would like to discuss some of the things IP flow technology has to offer pertaining to Network visibility, and I will also touch on how a NetFlow application can assist you in proactive network security.
With the level of Cyber threats companies and government agencies are facing, traditional security methods are not sufficient to keep a network secure. For a greater visibility into network traffic and cyber threats monitoring, you need two things:
- NetFlow or IPFIX capable routers, switches and Firewalls.
- A robust NetFlow Analysis program.
A. What exactly can you see with NetFlow?
Recent NetFlow implementations such as Flexible NetFlow and IPFIX greatly increase awareness and reduce vulnerability due to a much greater visibility into traffic, compared to earlier versions. Here is a limited list of some of the information you will now be able to monitor:
- URLs
- Applications visibility
- Application Performance
- Response time
- Latency
- Jitter
- User names
- Source and destination Mac Addresses
- Source and destination IPv4 or IPv6 addresses
- Source and destination TCP/UDP ports
- Type of service (ToS)
- DSCP
- Packet and byte counts
- Flow timestamps
- Input and output interface numbers
- TCP flags and encapsulated protocol (TCP/UDP) and individual TCP Flags
- All fields in IPv4 Header including IP-ID, TTL and others
- All fields in IPv6 Header including Flow Label, Option Header and others
- Next-hop address
- Source and destination AS numbers
- Source and destination prefix mask
- BGP Next Hop
- BGP Policy Accounting traffic index
- Application Monitoring
REPORT EXAMPLES
Application Monitoring: In this example, the NeFlow exporter is doing deep packet inspection to identify application and sends this information in the flow packets. Facebook traffic was characterized as facebook, and Google mail as gmail. The report also shows how much bandwidth they are using. If we had room for the entire report, you’d see even when this traffic was seen.
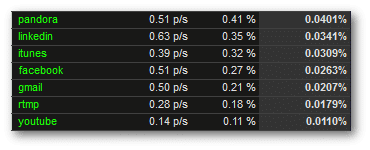
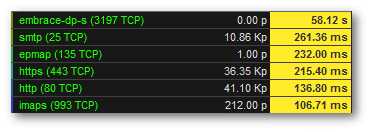
Application Performance: Determines application latency
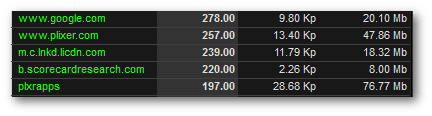
HTTP URL Monitoring: Which specific web addresses were visited
B. Proactive Network Threat and Intrusion Monitoring.
Proactive Behavior Analysis: Your NetFlow and IPFIX Analyzer can detect threats that Firewalls, VPNs, and antivirus software are not able to detect. On top of the fantastic network visibility you get, it analyzes NetFlow data to detect 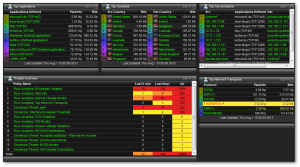 network threat behaviors in your traffic. It is able to detect DDOS attacks, DNS hits, NULL scans, SYN violations, FIN violations, P2P, and several more.
network threat behaviors in your traffic. It is able to detect DDOS attacks, DNS hits, NULL scans, SYN violations, FIN violations, P2P, and several more.
Proactive Essential Flow Data Consolidation: The traffic monitoring application also proactively analyzes flow data to gather and consolidate real time information that allows for faster troubleshooting and less downtime. This information includes top applications, top host to host conversations, most utilized interfaces, top protocols, most visited domain names, busiest subnets, IP reputation lookups, etc.
Are you looking to deploy NetFlow on your network? Contact us to learn more about how you can enhance security using NetFlow.