Network Address Translation reporting is now available from NetFlow exported from the Cisco ASA.
The traditional NetFlow reporting that can be done from the Cisco ASA is great. But have you noticed that when your firewall NATs an address, it becomes the source or destination within your flows, and thus makes NetFlow a lot less useful.
How can you tell who this conversation is going to when the destination address is NAT’d?
We are one of the only flow analysis technologies that can currently report on the non-traditional, unique NSEL elements being exported, such as username, NAT, ACLs, and event codes.
Let’s take a look at how we can use the NAT report filters to track the private address involved in a conversation.
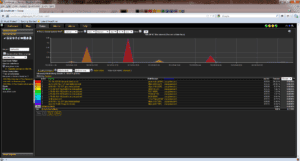
Looking at a Conversation report we can see all of the incoming traffic taking place on the WAN interface.
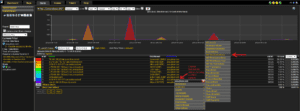
We can now easily look at the public to private address translation for any conversation by clicking on the destination IP Address and selecting the DST NAT Translation from the Cisco ASA report category.
The ASA’s NSEL templates allow the network or security analyst to “see around” the NAT, which can help reduce Mean Time To Know as well as the Mean Time To Repair.
Do you know where conversations are going inside your network? Gain insight into your network by using NetFlow exported from your Cisco ASA that is invaluable for application and user security monitoring.