I’m no network administrator, but I know that monitoring network abuse and policy observance is imperative to keeping a network safe. After writing my last blog on incident response system guidelines, I received a few emails about going more in depth using custom data correlation and thresholds. It can be difficult finding the information you want before you even know you want it. Would you like to know that the phone is about to ring because of a possible infection or that the network is about to become slow? Now, no one can tell the future but having a little more insight using NetFlow and IPFIX data will help predict a possible issue.
Monitoring Bandwidth Usage:
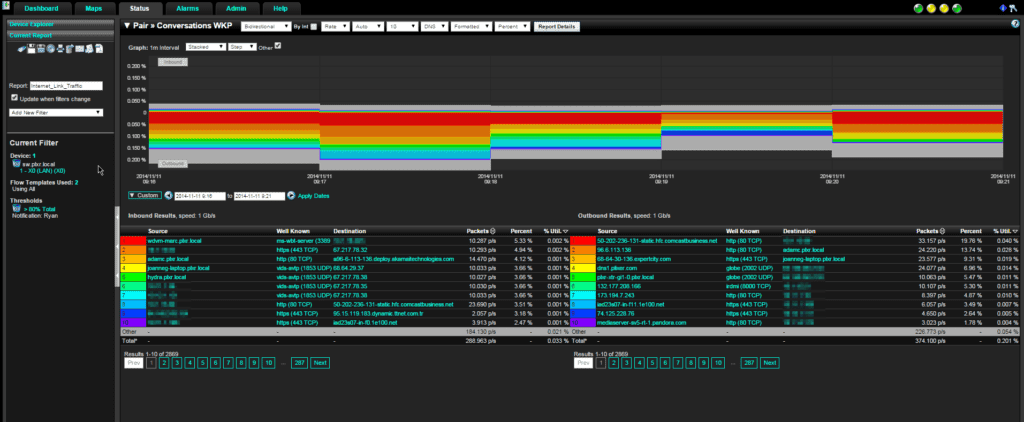
Let’s start with a simple example of knowing when your network is about to become slow by monitoring bandwidth usage to the Internet. In the image below, I set up a report on the LAN facing interface of our SonicWall firewall. This shows total traffic going in and out of our network. If you look to the left side of the screen shot you will see that I set a threshold on the total traffic in this report to send a notification when this link hits 80% of the designated link speed. The report will be emailed to me when the threshold is exceeded, letting me know that this link is getting low on bandwidth. This way I can make the first call to the employee that is utilizing that link the most and stop the issue before it becomes a problem for anyone else.
Enforcing Network security policies:
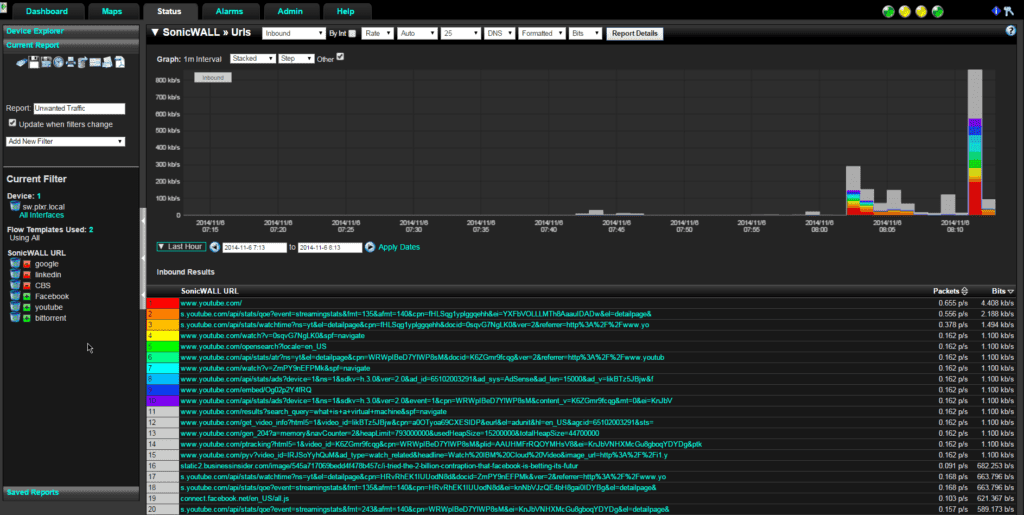
Even being at a company that allows unrestricted access to the Internet during working hours would have policies in place that say “in moderation”. I will be the first to admit, I’ll hit YouTube every once in a while if there is something that I need explained in a little more detail. Now, let’s monitor that traffic to see if it becomes excessive for any one user. Take the next report below. We again are going to use the SonicWall firewall for their excellent URL reports. I set up a few filters on the left hand side to aggregate the domains I want to see and filter out the ones that I know to be normal traffic. From here, we can select a conversation that is taking up the most bandwidth and find out who that conversation is with.
UPX Packed Executable File:
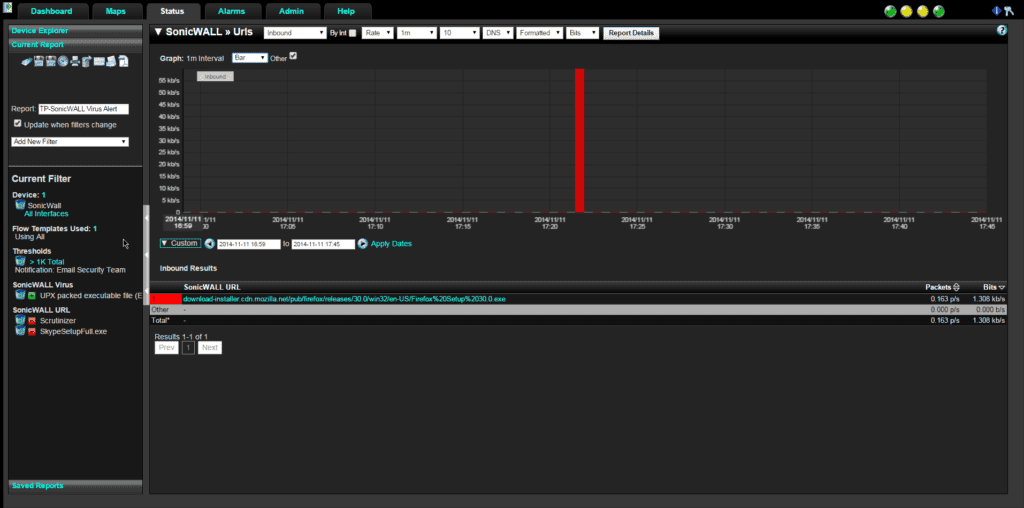
In this last report, we are going to monitor UPX packed executable files that are being downloaded from the Internet. The UPX packer is a common packer for malware so we want to know when it is seen being uploaded to the network. We set up another report of our trusted SonicWall firewall to show UPX packed executables. We have filtered out a few executables that we would expect to see then set a threshold to alert our security team when there is any traffic to show in this report.
How you monitor network abuse and policy observance will change from company to company but the logic is the same. Find the traffic that is important to you and be alerted using NetFlow and IPFIX data before the problem becomes too much to handle. Save time and money by resolving issues faster and keeping your network safe.

