NetFlow Security Monitoring
When you hear NetFlow/IPFIX, what is your first thought? For most people, their first thought will be “NetFlow’s great for performance monitoring” or “IPFIX allows us to monitor a user’s traffic, even Layer 7 traffic”. These are the most common applications of flow technologies, but what about NetFlow security monitoring or incident response? If flow data can give me the Who, What, When and Where, then why not leverage these contextual details in your forensic investigation. Most people will tell you they’re happy using their IDS or IPS, alerting when a signature-based attack is detected. The problem here is two-fold.
Detecting a signature-based attack absolutely has value in IT Security, but what about when new malware is written, or a few bits of code are changed in existing malware giving it a new ‘identity’. This is where flow Data can help by adding a layered security approach. Cisco has an excellent document overviewing the valuable metadata within NetFlow that can be used in IT Security. You can view the document on Cisco’s site.
I’d like to look at a few key applications of Flow Data in forensic investigations.
Mean Time to Know
One of the biggest benefits of using flow data for security purposes is that it will drastically cut down your company’s mean–time-to-know. NetFlow is the All Seeing Eye on your network. By providing a 24×7 view into all network activity, flow data can be used to alert you to an incident as it occurs, as opposed to after the damage is done. Having these details at your fingertips not only cuts down investigation time, but saves the company time and resources.
Layered Approach to Security
Having a layered approach to your security practices is incredibly important in networking today. Every solution has areas where they excel and others where they come up a little short. While having an IDS and IPS on your network is important, there are times something will sneak past. That’s where the real time view that flow data provides will excel. flow data can be used to monitor and alert to anomalous traffic based on its behavior. A colleague of mine wrote a blog on having a layered security approach and preparing by having an Incident Response Protocol that’s very informative.
NetFlow vs Packet Capture
First I have to clarify, NetFlow isn’t meant to replace a packet capture. Packet captures have great value in providing insight into the payload traversing your network. However, packet captures can be expensive to deploy, especially if you have an extensiveinfrastructure. NetFlow data is lightweight and extremely inexpensive to collect and store. If you will, NetFlow and Packet Capture are almost the perfect marriage.
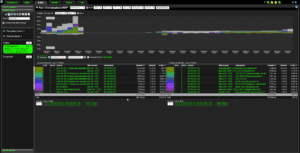
Let’s look at a few examples of how NetFlow can be used in the field. We’ll start with a Pair report looking at conversations over well-known ports.
Here you’ll see we have some great information at our fingertips. Right off the bat we know who’s talking to who, which protocol and common port were used, as well as how much bandwidth was consumed. In this report, we can see what interface they’re coming in and what interface they leave on. These are great details, allowing you to know at a glance what is happening on your network.
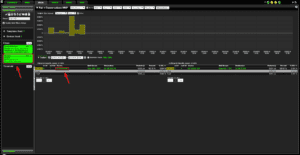
Let’s assume you see something strange in here; there’s an IP at the top of the list consuming your bandwidth, but you don’t recognize this IP; let’s investigate further.
Here you can see I’ve added a filter for the IP in question, and now I’m only seeing traffic involving that particular IP. In the case of this IP, this seems to be an innocuous conversation.
We can dig deeper from here if necessary by performing a WHOIS on this IP and gathering some more details.
The power of NetFlow is growing every day, especially with IPFIX allowing us to export more contextual details.
If you’re interested in learning more about utilizing Flow data for malware or breach investigations, reach out to our helpful support team; they would be happy to help.