I’ll be the first to admit that my patience starts to wear thin when troubleshooting a problem and having to jump through 10 different tools to tie all of the pieces together. NetFlow collector integrations are a huge benefit to look for when scoping out a new solution. This blog aims to cover some integrations you might want and why they are important.
Why are integrations important?
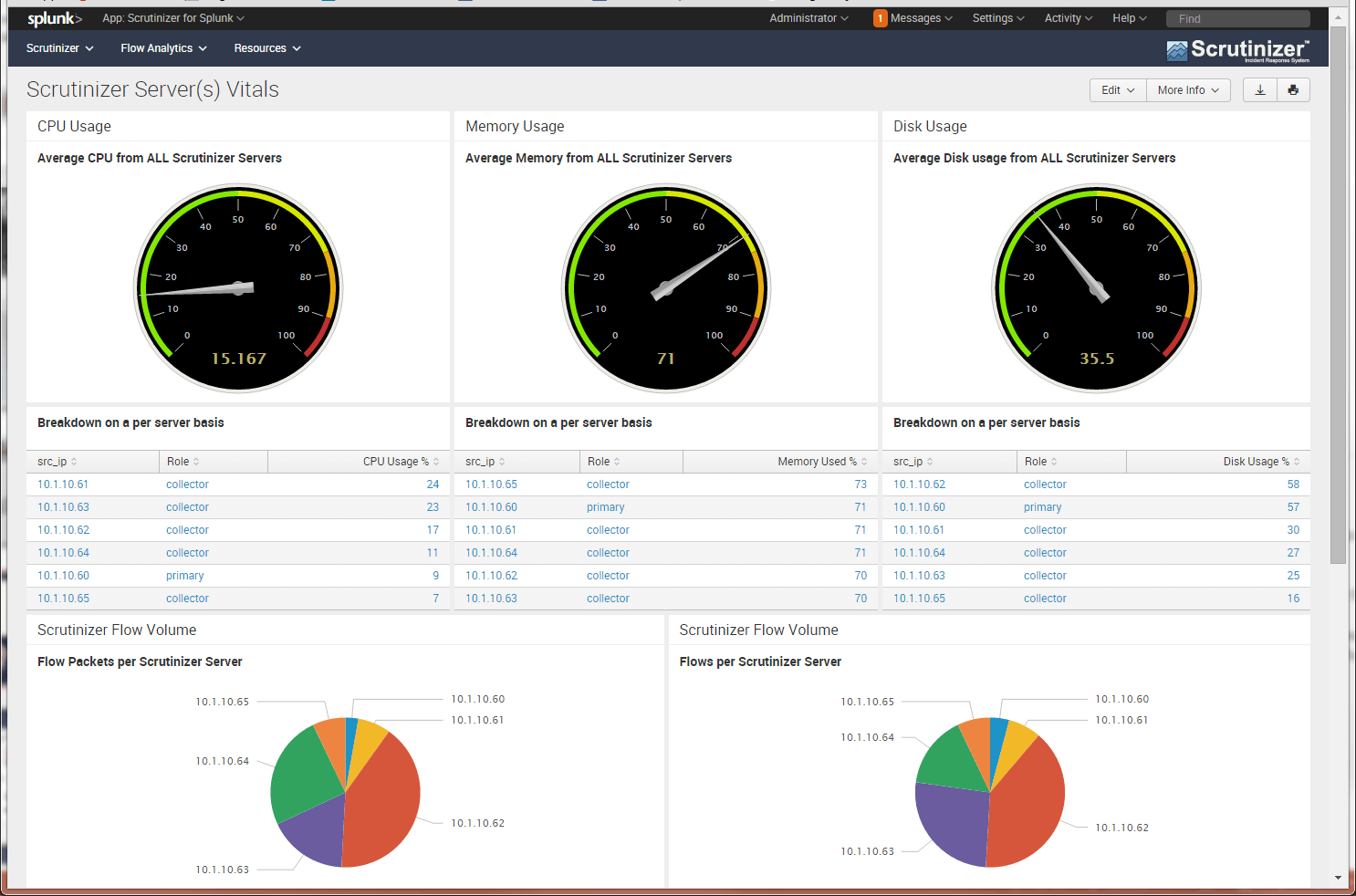
We always hear the term “single pane of glass” and that’s what we have been told we want to see in a solution. While this may be true, often times it leads to useless noise that makes a tool cumbersome and hard to manage. It’s important to know exactly what information is important to you and present it in a way that is elegant and easy to understand. This is why a customizable dashboard is very important to look for. Are you able to customize it for each team that’s using it? Are you able to link to other solutions rather than having to jump between tabs? Can you create custom “widgets” or are they all pre-canned? These are important questions you should be asking and will only aid in the usability of the tool.
NetFlow Collector Syslog Integration
So now you know why you need integrations; what should you be looking to set up? One of the most common integrations we set up is Syslog support. Often times we will set up our IPFIX collector to send out syslogs; if an alarm or certain criteria is met, often times this will be sent to Splunk, Kiwi, or ELK, but usually can be sent to anything accepting syslogs.
This will help you correlate events that you find in NetFlow with different logs that you might be collecting. Lowering the time it takes to resolve an issue and simply pivoting to another tool rather than having to search from the ground up keeps you organized.
NetFlow Packet Capture Integrations
Another popular integration (usually for Application or Security teams) is to integrate a NetFlow collector with a packet capture solution (such as Endace or Moloch). This allows you to easily parse through the flows to find an event that is suspicious and to simply pull packets from your browser to easily open in a packet decoder such as Wireshark. Since NetFlow is more lightweight than full packets and is easier to sift through, it makes the MTTK (Mean Time To Know) a lot shorter than if you were to try and search through 24 hours (or more) of full packets.
If you are currently frustrated with having to jump through multiple tools to find the root cause of a problem, reach out to use today to find out how we can help!