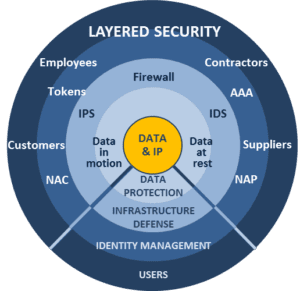
A layered security approach for detecting malware cyber-attacks is the current “go-to” way to defend both network perimeters and individual endpoints. But layered security doesn’t accomplish much unless it triggers an appropriate and effective response.
Typically for the stand-alone layers, the local independent countermeasures of each layer are not enough unless they are consistent with pre-planned responses specific to the enterprise network being defended. Active anticipation of potential cyber-attacks and how to respond is key. As Edmund Burke once said: “Better to be despised for too anxious apprehensions, than ruined by too confident security”.
Defense against the increasing scale and complexity of today’s cyber-attacks (e.g., DDOS, zero-day, password list, APT, and targeted attacks) relies heavily on advances in commercially-available automated security software and appliances. Collectively, enterprises spend billions of dollars on these products and services adding layer upon layer of security from advanced firewall appliances to data loss prevention (DLP) applications.
Over the past decade, layered security and defense has developed into a distinct and widely-adopted enterprise security strategy. The concept is simple: Any one layer of security may not catch everything, but multiple layers, each with its own strengths and weaknesses, compensate for the shortcomings of other layers. Firewalls, anti-malware, anti-spam, intrusion detection, DLP, encryption, sandboxing are layered to provide multiple opportunities to prevent successful cyber-attacks.
Unfortunately, cyber-attackers all too easily probe and learn how each of these defensive layers works. They can then adapt their malicious Advanced Persistent Threat techniques to defeat individual new layers and, worse, figure out ways to circumvent the entire structure of the layered defense. Ultimately, the layered security approach suffers from weaknesses similar to those of the individual layers it so effectively combines: Each layer that is added carries its own costs – adding maintenance and operations costs to the enterprise while possibly negatively affecting network performance and user experience.
At best, a layered security approach by itself is only a way for defenders to try to keep up with the adaptations of attackers. It will always be at least half a step behind the latest innovations of the cyber-attackers [TechTarget].
Incident Response Planning offers a way to incorporate automated layered security into an overall defense that succeeds in thwarting attackers even when they penetrate all of the security layers.
The first step is to make layered security part of overall network visibility. Rather than stand-alone defense systems, detection information from firewalls and anti-virus can be integrated real-time and correlated with other sources (such as network flow data), that provide alerts to the occurrence of something suspicious. These alerts, in turn, can focus attention and trigger investigation with a much broader context than an individual stand-alone security layer can provide.
Incident response is not another layer of security defense. An Incident Response Plan anticipates the behavior of malicious activity that may occur within an enterprise and sets policy, in advance, for detecting, responding, and recovering from actual cyber-attacks and malicious activity [webcast: Malware Incident Response]. The plan defines what network events will trigger security incidents and investigations, as well as the procedures and timing of escalations if incidents remain unresolved. Building an incident response system for cyber-security is a combination of (i) security policies and employee awareness; (ii) integrated and cross-correlated detection systems, (iii) security staff that investigate, understand, and resolve triggered incidents, (iv) pre-planned procedures and timing that ensure unresolved incidents receive timely escalated attention to executives responsible for ongoing risk management and, if needed, the engagement of external security resources to ensure resolution.
Incident Response is not another layer of security. It is an integrated dynamic system of policies, people, and automation tools that ensure effective and timely detection, understanding, and response to all security incidents wherever and however they occur in the enterprise network. A good incident response system integrates all the layers of security with a contextual understanding of all the network activity to provide timely and effective information assurance.
To learn more about enhancing your layered security with incident response planning visit the Incident Response System page.