The Internet of Things (IoT) market is booming. Gartner predicts that 5.8 billion IoT endpoints will be in use in 2020, marking a year-over-year growth rate of over 20% since 2016. While IoT devices undoubtedly make life more convenient, they also present an expanding attack surface as a means of network infiltration. Recent reports suggest that IoT devices have become a primary target with attacks on IoT devices up 300% in the first half of 2019. Given these developments, IoT security has become a hot topic.
What is the Internet of Things?
The concept of IoT is simple. In its most basic form, it means connecting every device in the world to the internet. Connecting devices to the internet means that they can communicate with each other, which can simplify daily routines and tasks. Your fridge can automatically order your favorite items when you run out. Devices such as the Amazon Echo and Google Home can be used to remind your kids to do homework, shut down your house for the night, and bring everything back to life in the morning—all from the comfort of your bed.
To accomplish these tasks, IoT devices have to collect, receive, send, and act on information in a variety of ways. A good example of this is a thermostat using location data on a cell phone to preheat your house when you are on your way home. IoT is all about bringing the power of the internet to all the devices that are not computers and enabling people to use them in new, innovative ways.
What are the security implications of IoT devices?
Despite these benefits, there are major privacy- and security-related downsides to IoT devices.
You may be asking yourself why anyone would co-opt a door sensor, light switch, or light bulb. These devices can be used in a botnet that will then conduct DDoS attacks. This is alarming, but it’s potentially the least troubling aspect of unsecured IoT devices.
IoT devices must collect data about a user in order to be useful. While the data that one device alone collects may not be particularly troubling, it’s important to keep in mind that data is collected from multiple endpoints. These data elements can be analyzed and correlated to paint a complete picture of one’s daily activities.
This is especially dangerous in certain industries. For example, healthcare devices provide life-critical functions. The implications of tampering with these devices could mean life and death, but they are attractive targets because of the sensitive information they contain. These concerns will continue to grow with the proliferation of internet-connected devices.
Scrutinizer can help with IoT security
Scrutinizer is a leading traffic analysis system that identifies malicious behavior by monitoring every conversation on your network. Scrutinizer’s collection of NetFlow and metadata enables you to determine whether any smart devices on your network are targets or have been co-opted.
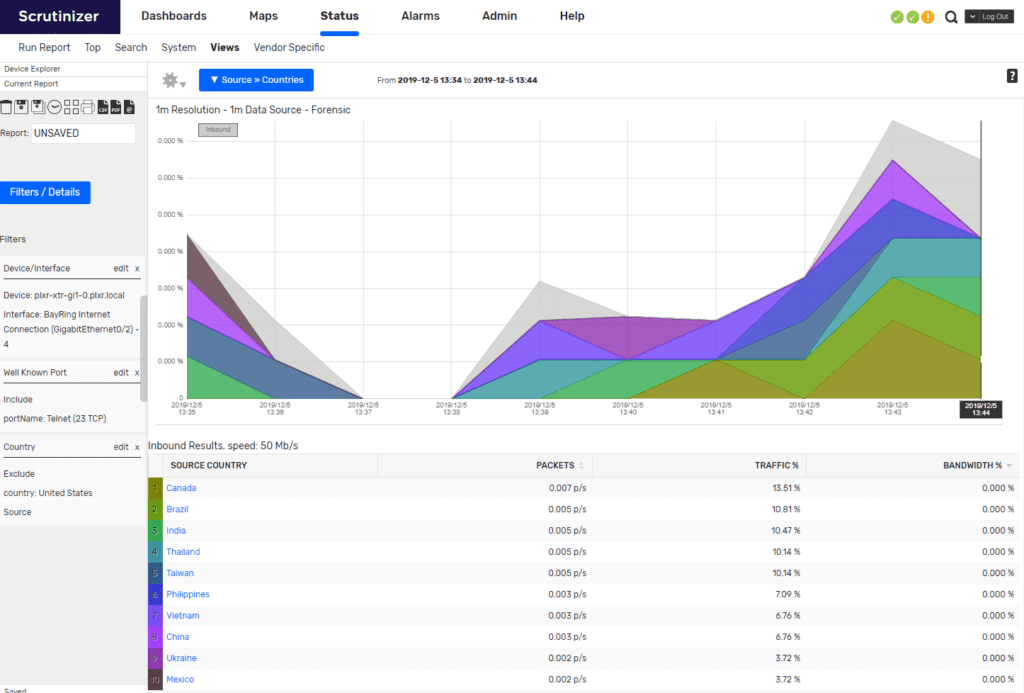
These devices are primarily targeted on the Telnet protocol. Scrutinizer can be leveraged to monitor this service and alarm if brute force attacks are detected. This would be a similar setup to detecting network scans with NetFlow. A simple change to eliminate false positives is to add the “tcpcontrolbits” element. This allows us to remove alerts from public IP scans by focusing only on ACK messages being sent back.
Begin setting up this report by selecting your Internet Connection interface.
I like to start with a Source > Countries report.
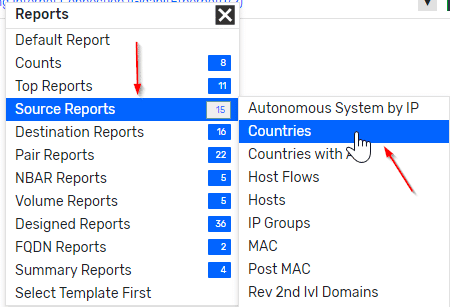
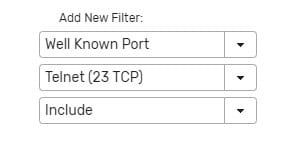
Add a Well-Known Port filter for the Telnet service.
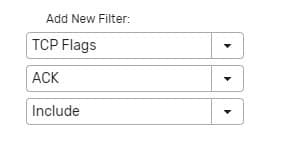
Add a TCP Flag filter for ACK.
The result is a report that can tell you what is going on very quickly.
Try Scrutinizer for free today or give us a call at 207-324-8805 x4 if you need help improving your IoT security.