What’s this? What’s this? There’s IoT devices everywhere!
The joy of Christmas comes with smartwatches, tablets, toys, and malware. IoT devices are often less secure than the phone in your pocket. But as consumers, we view them in the same light as we do toys and accessories: harmless gadgets that schedule our day, tells us the news, and connect to our network. That last part is often forgotten and you can bet that with all the Christmas excitement, it will be forgotten by your colleagues as well.
What is it about IoT devices that make them so dangerous?
They see you when you’re sleeping, they know when you’re awake and like Santa and his elves they work quickly and quietly to navigate your home or office.
Most IoT devices have a secondary common use: to learn as much about you as possible and send that information back to the companies who developed them. The idea is that this data will assist companies in building better products tailored to your needs. Or maybe they just want to use that data for marketing purposes, so they know what to get you for Christmas.
Why is this dangerous? Any device that allows for communication beyond your network is at risk of becoming exposed to malware.
How can IoT devices impact my network?
As colleagues bring in their new gadgets to the workplace, they will most likely attempt to connect them to your network. This leaves you open to attacks. Here are the most common ones:
- Man-in-the-middle attacks: This is when the attacker sits between at least two systems, convincing both that he/she is the other. With this type of attack, the attacker is looking to either intercept or send data.
- Botnets: These are another common attack that is often distributed through various IoT devices with the purpose of continuing distribution to later perform large-scale attacks. You may recall the recent IoT Reaper and Mirai botnet attacks.
- Denial of Service (DoS) attacks: Sometimes carried out by a botnet army, this is an attack with the purpose of bringing an organization’s network to a halt. DoS attacks use botnets to send a massive number of requests to a server at the same time in hopes of overloading it.
How can I improve my IoT security before Christmas?
Why, stop it from coming, of course!
As technology continues to evolve, so do the challenges of IoT security. We can do our best to educate our colleagues, and even collect their IoT devices at the door like the Grinch stealing Christmas. But the truth is that we can’t catch everything; there will always be that one Who in Whoville who thinks they are the exception.
But we can strengthen our IoT security by baselining our network traffic prior to Christmas vacation. By doing so, we’ll have a better understanding of our network and be able to recognize irregularities.
Below I’ve used Scrutinizer (Plixer’s network traffic analytics solution) to display my custom reports on a dashboard I’ve named “BYOD Monitor.” This way I can view my holiday reports all in one place.
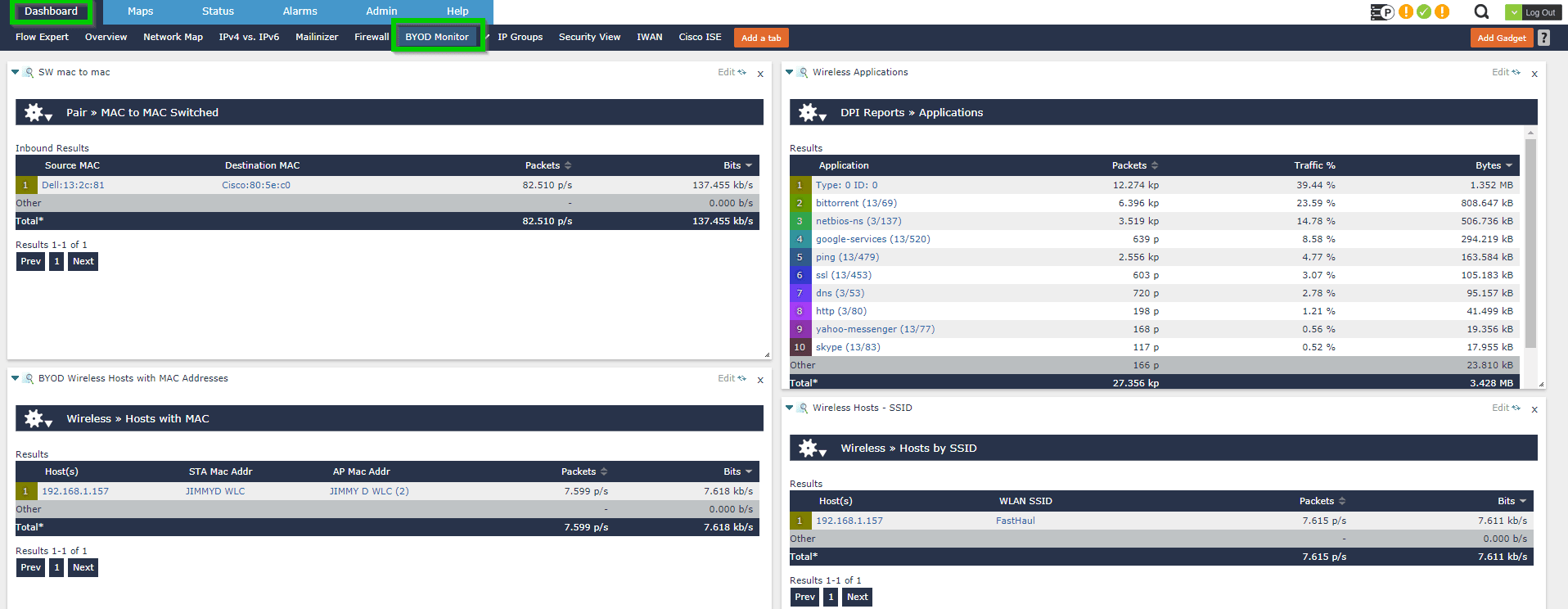
I then built a report of suspicious countries often referenced in attacks.
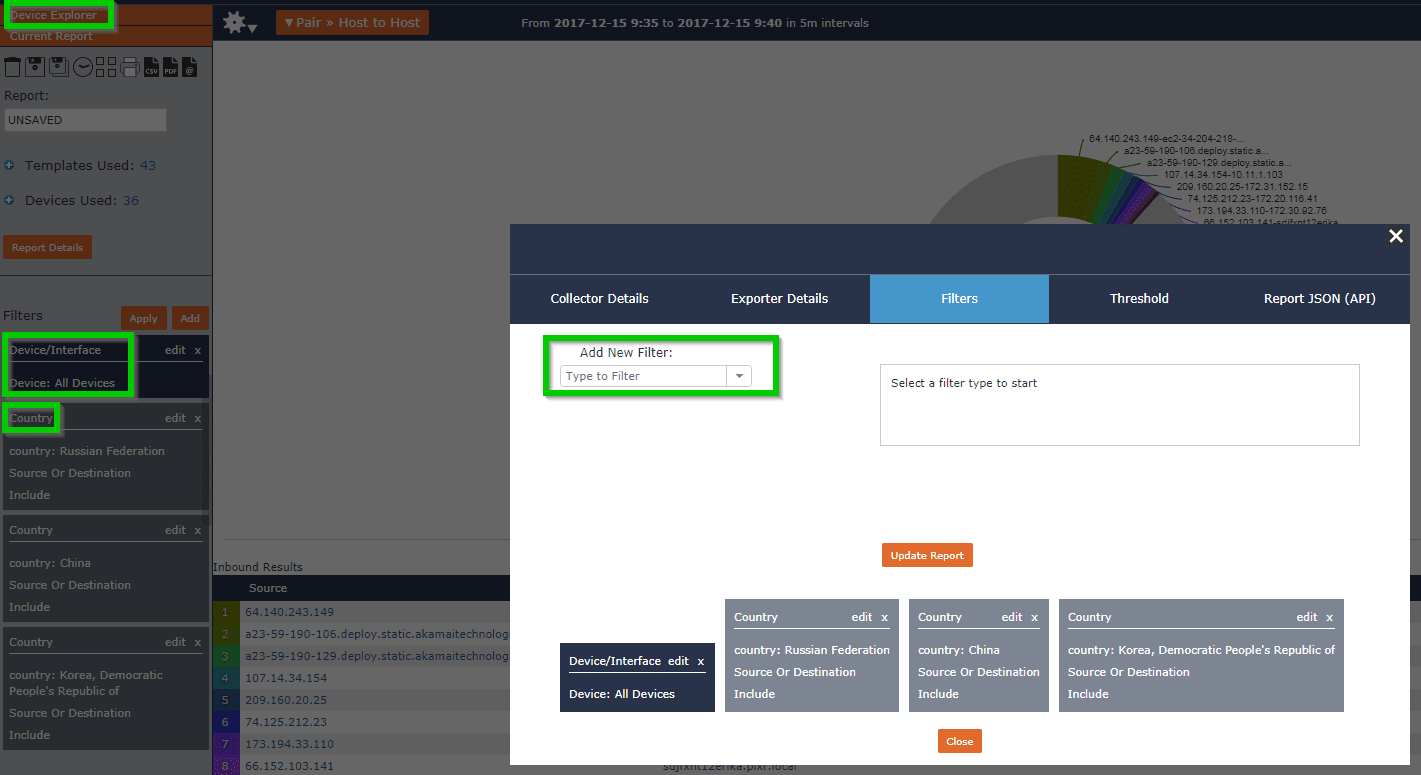
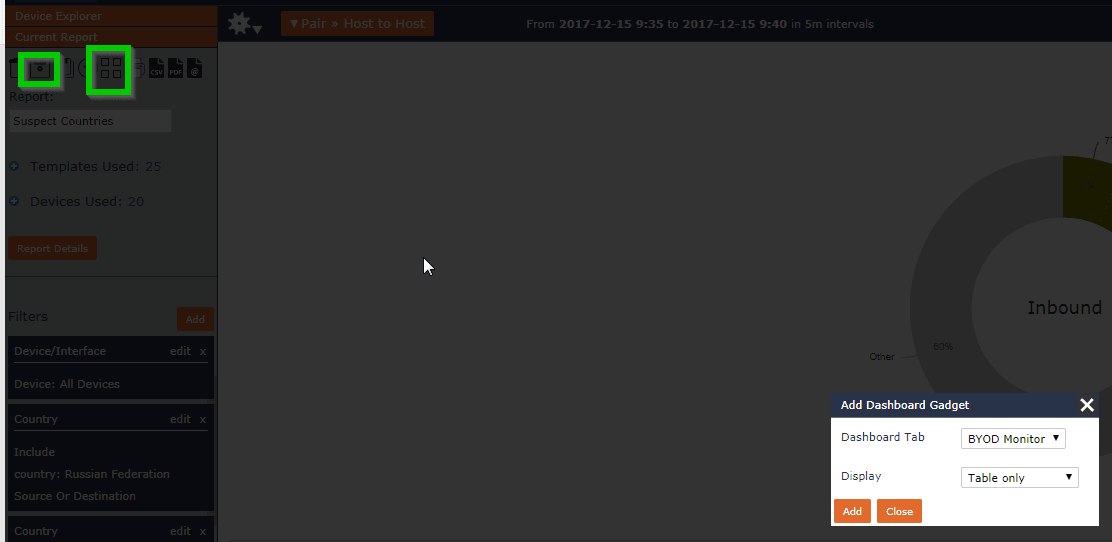
I then named this report “Suspect Countries” and added it to my BYOD dashboard:
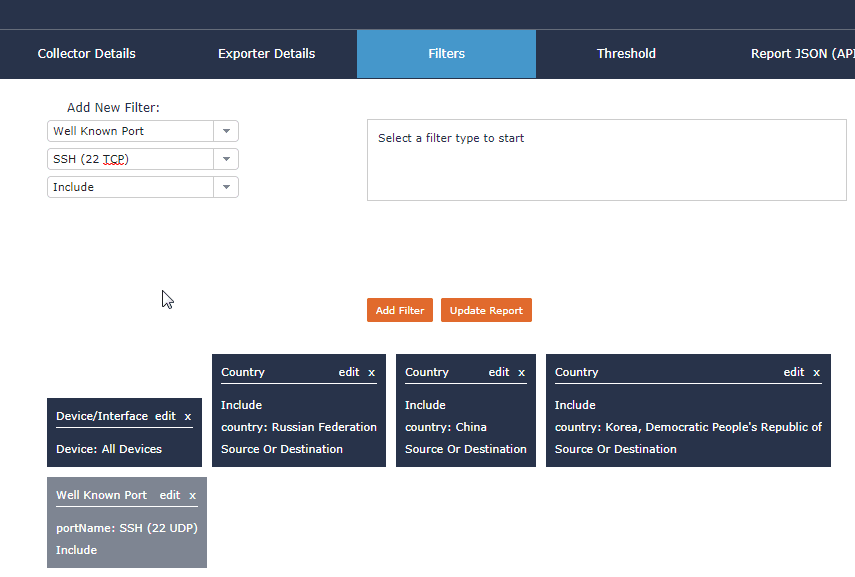
I then went back to the report and filtered on ports. I only used SSH ports for these countries, but you can filter by both IPs and ports you know to be associated with various ransomware or botnet attacks.
You can then build thresholds to trigger alerts on these reports when traffic exceeds a defined volume by selecting the threshold option below device explorer.
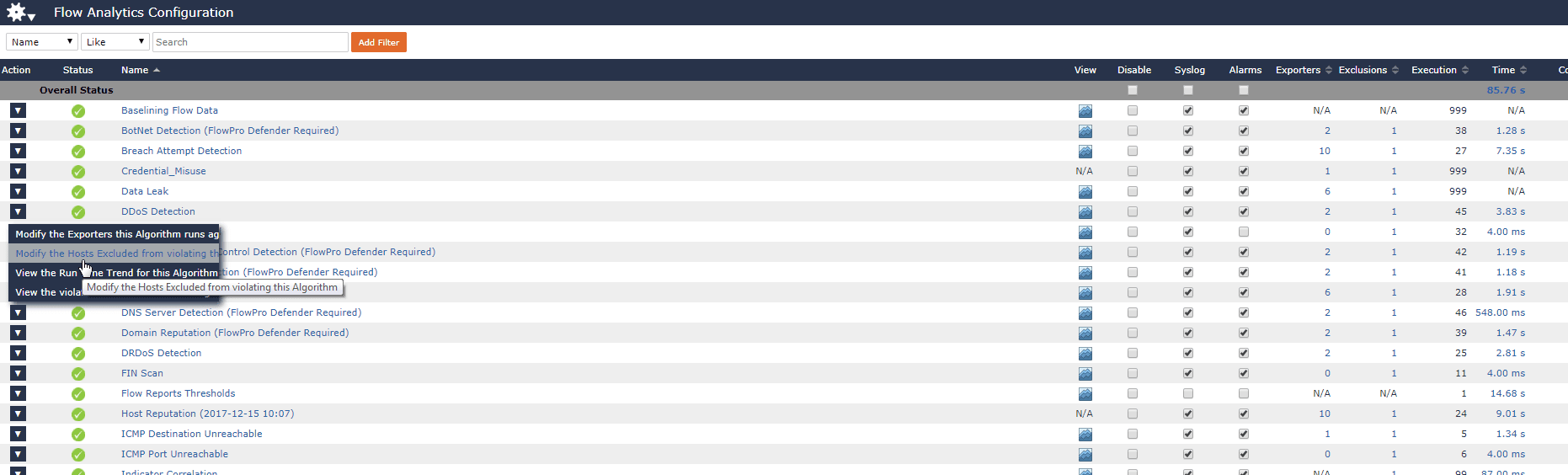
I then reviewed Scrutinizer’s 53 predefined algorithms to ensure that I had enabled DDoS detection, botnet detection, and a couple others I found useful for my network. I continued editing these alarms to match my network. I also spent some time defining a notification group for these alarms so that I’ll automatically have the report emailed to me and my team should one of our policies be violated.
Now I am prepared for the joys of Christmas! You can prepare your team for these many new devices by monitoring and alerting on the traffic crossing your network using Scrutinizer’s free version this December.


