You received a call about an IP address behaving strangely and now you need to investigate the issue and start collecting details surrounding the event. As the information is gathered, you will try to put the puzzle together and hopefully discover what is happening, why it occurred and how long it will take to clean up. From small networks with a few routers to massive – distributed network environments, searching for the system is often where it all begins.
In 2014 it was reported that 94 percent of organizations had experienced at least one cybersecurity incident in the past year. Of those incidents, 12 percent of respondents reported at least one targeted attack – up from the 9 percent reported by organizations in 2012 and 2013.
As for the potential losses incurred from such attacks, Kaspersky estimates roughly $2.54 million in damages for enterprises and $84,000 for small businesses.
Searching – Usernames
If you can, start with a username. You don’t always want to search for an IP address, enter the username when possible or a portion of it and let the flow searching system do the rest. Within seconds, our incident response system will search dozens of distributed collectors located all over the world. The results are brought back to a single interface where sers can drill in to find out what the user was doing and if necessary, find out where on the network the behavior was observed and when.
More Context = Security Analytics
Integrating Microsoft Active Directory, Cisco ISE, Mobile IAM or other authentication system with your incident response system allows for improved security analytics. Greater context surrounding a located IP address means you obtain greater details such as operating system, MAC address, applications installed and more. The faster you gather the contextual details related to an infected computer, the better your security analytics and the sooner you can take action and start the remediation process.
One Wrong Click
If you believe the infection started with a phishing attack or a drive-by infection on a web page, you can run a report on the URLs visited by the host, check the reputation of the site visited and even search for other internal systems that may have visited the same web page.
DOS Attacks – Botnets
Just because you haven’t found yourself investigating targeted attacks yet, that doesn’t mean you aren’t participating in one. All it takes is one user, somewhere in the internal network to visit a web site that is infected and your company could be participating in an attack on another company. See: cyber attack – incident response.
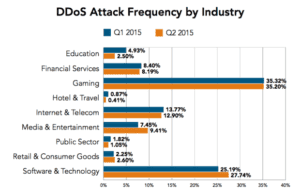
DDoS Attacks aren’t going away, in fact, they are on The Rise. They increased 132% in Q2 2015 with HTTPS being the most targeted.
Check out Investigating Internal Network Attacks and learn how BYOD walks infections right in.
No Packet Analyzer – No Problem
Although packet capture provides all the details at a transaction level, the cost of acquisition and the on-going maintenance can prevent deployment in all areas of the network. To remedy this problem, the NetFlow and IPFIX exports collected today from many major vendors (E.g. Ixia, Cisco, Citrix, Dell, Palo Alto), include details that come close to packet capture. Details include MAC address, username, URL, layer 7 application, and more. Even SSL connections are decrypted and the contents of the secure connection can be archived for future analysis. All of these enhanced flow details means improved security analytics when investigating a problem. Make sure your cyber threat incident response system can report on these details from all vendors.