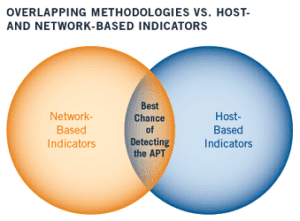
In many cases, previously unidentified malware and back doors were identified through the use of these indicators in both network traffic and host-based information. The combination of both host- and network-based indicators continues to be the most reliable way to identify APT-related malware on a network.
“IPS (or deep packet inspection) is our #1 security defense; Netflow is a very close #2 – Gavin Reid, Manager of Cisco CSIRT.
NOTE: This is part 3 of a 3 part blog on Internet Threat Defense Solutions. You should begin with Part 1.
NetFlow and IPFIX solutions are well suited for organizations trying to identify APTs for several reasons:
- Solutions like Scrutinizer constantly compare IP addresses found in flows to a constantly updated host reputation database
- Scrutinizer can monitor the network for odd traffic patterns such as network scans and odd flow to connection ratios
- Scrutinizer can be used to investigate traffic to determine who a potentially infected host has been communicating with, when and for how long.
- Scrutinizer can be used to monitor system log activities. For example: failed logins.
“We’ve learned that NetFlow can tell us who is talking to who across our network, but how can we tell if either who is a bad actor? By checking the reputation of the IP addresses at both ends of the conversation.“ – Mike Schiffman at Cisco
Exfiltration of Malware
Immediately isolating machines infected with APTs is often not the ideal tactic. Because APTs often setup camps within companies, there are often dozens of other infected machines. NetFlow can be used to determine who the other machines are by:
- Watching the traffic to and from machines infected with APTs.
- Looking at the internet hosts infected hosts are communicating with and determining who else is communicating to the same command and control centers.
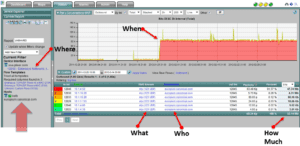
NetFlow is ideal for forensic analysis because it contain the significant details necessary to determine who, what, when, where and how much within the communication patterns.
With numerous internet connections and the voluminous amount of information, flow collection and reporting is really the only cost effective method to perform investigations when absolutely all traffic must be scanned.
Confirmation of Cleanup
Once the malware has been cleaned up, NetFlow or IPFIX monitors should be configured to constantly monitor for the traffic patterns that were telltale signs of the insurgence.
Once the violations stop for a period of time, we can become confident that the malware has been removed.
Summary
All companies are under attack every day. Just as a retail store can’t stop all shop lifters, neither can the best IT security teams stop all forms of malware from getting into a company. When an exfiltration does occur, flow analysis is often either directly involved with the detection or certainly a significant part of the investigation and data analysis effort.
Although deep packet inspection continues to be a primary APT detection method, flow technology is without a doubt an ideal additional layer of protection. Packet capture provides greater detail however, it often can’t be done on every internet connection in every remote office.
Flow Analysis allows security teams to cover and record all traffic to every location on the network at all times similar to security camera’s deployed in a financial institution. If the traffic entered the company, it was almost always captured and recorded with NetFlow or IPFIX. Read the white paper on Internet Threat Defense Solutions.